Hackers Launch "Phishing Attack" on OpenSea Users
Author: Jasmine, Hive Tech
On February 19, as the world's largest NFT trading platform OpenSea began supporting users with new contracts, some users' NFT assets were stolen.
The next day, OpenSea's CEO Devin Finzer disclosed on Twitter, "This is a phishing attack. We do not believe it is related to the OpenSea website. So far, it seems that 32 users signed malicious valid payloads from the attacker, and some of their NFTs were stolen." Finzer stated that the attacker's wallet once gained $1.7 million worth of ETH by selling the stolen NFTs.
After the users' NFTs were stolen, many speculated on Twitter that the phishing attack link might be hidden in a fake "OpenSea to Users" email. This was because on the same day, the trading platform was undergoing a smart contract upgrade, requiring users to migrate their listings to the new smart contract. The attacker likely exploited this upgrade announcement to disguise the phishing link as a notification email.
On February 21, OpenSea's official Twitter updated its response, stating that the attack did not seem to be based on email. As of now, the source of the phishing attack is still under investigation.
OpenSea Users Lose NFTs to "Phishing"
On February 18, OpenSea initiated a smart contract upgrade to address the issue of inactive listings on the platform. As part of the contract upgrade, all users were required to migrate their NFT listings on Ethereum to the new smart contract, with the migration period lasting 7 days, ending at 2 PM EST on February 25. During the migration period, users' old listings on OpenSea would expire.
On February 19, users began the necessary operations to complete the migration. Little did they expect that during the chaotic migration process, hackers would reach into OpenSea users' wallets. From user feedback on social media, most attacks occurred between 5 PM and 8 PM EST.
From the addresses later marked as "phishing/hacker" on the Ethereum blockchain explorer, at 6:56 PM on the 19th, the stolen assets began to be transferred from the hacker's address, and by 10:30 AM on February 20, operations to "wash" the stolen assets using the mixing tool Tornado Cash appeared.
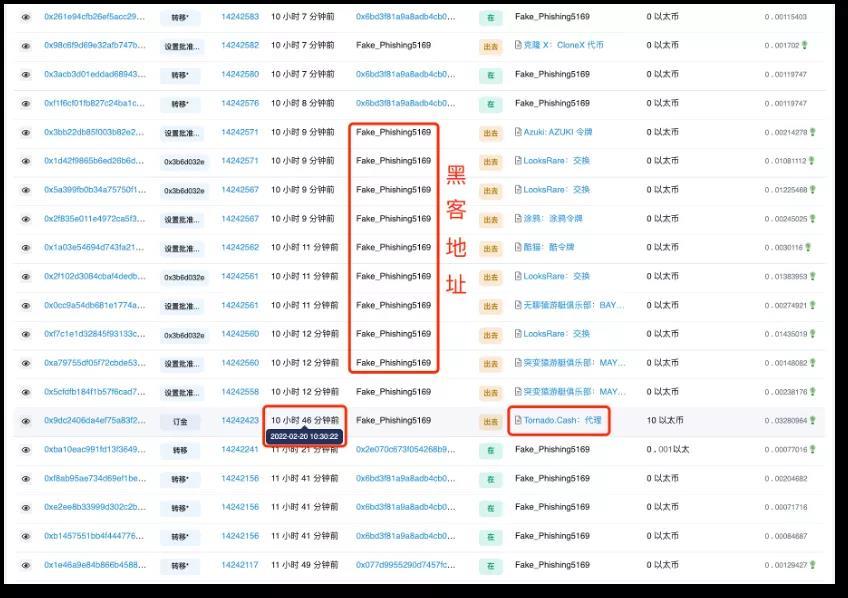
Some movements of the hacker's on-chain address
After the users' NFTs were stolen, the claim that "OpenSea was hacked, and $200 million worth of assets were stolen" began to spread online, leaving people unaware of the exact cause of the theft and unable to confirm how many users were affected.
It wasn't until February 20 that OpenSea's CEO Devin Finzer disclosed on Twitter, "To our knowledge, this is a phishing attack. We do not believe it is related to the OpenSea website. So far, it seems that 32 users signed malicious valid payloads from the attacker, and some of their NFTs were stolen." Finzer refuted the rumor of a "$200 million hacker attack" and stated that the attacker's wallet gained $1.7 million worth of ETH by selling the stolen NFTs.
Blockchain security auditing firm PeckShield listed the number of stolen NFTs, totaling 315 NFT assets, of which 254 were ERC-721 standard NFTs and 61 were ERC-1155 standard NFTs. The involved NFT brands included assets from the well-known metaverse project Decentraland and the NFT avatar "Bored Ape Yacht Club." The firm also disclosed that the hacker laundered 1,100 ETH using Tornado Cash, which, at the then price of $2,600 per ETH, amounted to a laundering value of $2.86 million.
How Did the Attacker Obtain User "Signature" Authorization?
After the incident of user NFT theft, some netizens speculated that the hacker exploited the news of OpenSea's upgrade to create a phishing link disguised as a notification email to trick users into clicking the dangerous link.
In response, Devin Finzer stated that they were confident this was a phishing attack but did not know where the phishing occurred. Based on conversations with the 32 affected users, they ruled out several possibilities: the attack did not originate from the OpenSea official website link; interactions with OpenSea emails were not the attack vector; using OpenSea to mint, buy, sell, or list NFTs was not the attack vector; signing the new smart contract (Wyvern 2.3 contract) was not the attack vector; using the listing migration tool on OpenSea to migrate listings to the new contract was not the attack vector; clicking on the official website banner page was also not the attack vector.
In short, Finzer attempted to clarify that the phishing attack did not come from within the OpenSea website. In the early hours of February 21, OpenSea's official Twitter explicitly stated that the attack did not seem to be based on email.
As of now, there is no accurate information on what link the phishing attack originated from to reach the users. However, the explanation that Finzer agreed with is that the attacker obtained user authorization to transfer NFTs through phishing.
Twitter user Neso's statement was retweeted by Finzer, where the user claimed that the attacker made people sign a "semi-valid Wyvern order," because aside from the attacker's contract and calldata, the order was essentially empty, and the attacker signed the other half of the order.
This attack seemed to exploit the flexibility of the Wyvern protocol, which is the foundational open-source standard for most NFT smart contracts (including those created on OpenSea). OpenSea verifies orders on its frontend/API to ensure that the content signed by users will operate as expected, but this contract can also be used by other more complex orders.
According to Neso, first, users authorized part of the contract on Wyvern, which was a general authorization, leaving most of the order content blank; then, the attacker completed the remaining part of the order by calling their own contract, allowing them to transfer NFT ownership without payment.
To put it simply, the hacker obtained a "blank check" signed by the user and filled in the other details to take the user's assets.
Some netizens also believe that at the source of the phishing attack, OpenSea ruled out the upgraded new Wyvern 2.3 contract, so it cannot be ruled out that the old version contract, which had been authorized by users before the upgrade, was exploited by the hacker. OpenSea has not yet responded to this claim.
As of now, OpenSea is still investigating the source of the phishing attack. Finzer also reminded concerned users that they can revoke their NFT authorizations on the Ethereum Token Approval checker.










