Decentralized VPN: Exploring a New Wave of Privacy
Original Title: “Decentralized VPNs: Surfing a New Wave of Privacy”
Author: Kaushik Guduru, Messari
Compiled by: Biscuit, Chain Catcher
Summary
- Commercial VPNs are highly centralized, posing risks to user privacy. Decentralized VPNs can be positioned to gain market share in the rapidly growing billion-dollar market.
- Due to physical requirements, hardware dVPNs may face challenges in terms of scalability. However, software dVPNs allow anyone with a network and a computer to act as a node.
- Hardware dVPN operators typically provide bandwidth for shared networks, while software dVPN operators sell their bandwidth individually on a peer-to-peer market.
- Following the success of Web3 infrastructure projects like Helium and Filecoin, dVPNs aim to incentivize operators to build distributed networks using token rewards.
From 2016 to 2020, the VPN market grew from $16 billion to $30 billion, with strong interest from both enterprise and individual users due to potential online threats. Therefore, by 2027, the VPN market is expected to exceed $92 billion.
Traditional VPNs establish encrypted connections through centralized providers' servers, providing dedicated tunnels for all user activities on the network. VPNs mask users' IP addresses and prevent any form of external surveillance.
However, regardless of the advertised privacy and security, users still need to trust the centralized third parties behind commercial VPNs. Centralized third parties can claim they do not track user activities on the network but cannot guarantee that the VPN is open-source. Users face the risk of their data being logged and sold to third parties or being exposed in data breaches.
Moreover, the location of VPN servers may be limited. Therefore, if users attempt to virtually position themselves in other countries, they may not find servers available there. Finally, monthly and annual subscription fees can become expensive for users, who still have to pay for the service even when not using the VPN.
Web3 infrastructure has been built to address some issues with current technology, placing greater emphasis on privacy and security. Decentralized VPNs (dVPNs) can replace commercial virtual private networks (VPNs) by eliminating centralization. Although they still represent a small part of Web3 infrastructure, dVPNs aim to create a distributed, secure, and private network for users worldwide. Both software and hardware versions of dVPN play a crucial role in achieving this goal.
In-Depth Look at dVPN
From a technical perspective, dVPNs are very similar to VPNs, but they have some notable differences:
Incentives ------ Incentivizes node operators to run nodes on the network and share their bandwidth in exchange for token rewards, rather than relying on centralized servers. Network speed depends on the number of users. The more users there are, the faster the network speed, and the quicker the network grows.
Compensation Structure ------ The compensation structure of dVPNs is starkly different from that of commercial VPNs. Hardware dVPNs require a one-time payment when users purchase their products, while most software dVPNs use a "pay-as-you-go" service model. Both options are economically more viable than commercial VPNs.
Multi-routing ------ VPNs can only route through one network channel at a time, but dVPNs allow users to easily switch nodes and use different routes and servers simultaneously.
Many dVPN projects are at different stages of development, with varying network architectures, services, features, and reward mechanisms. However, the biggest distinction between dVPNs lies in their type: hardware or software.
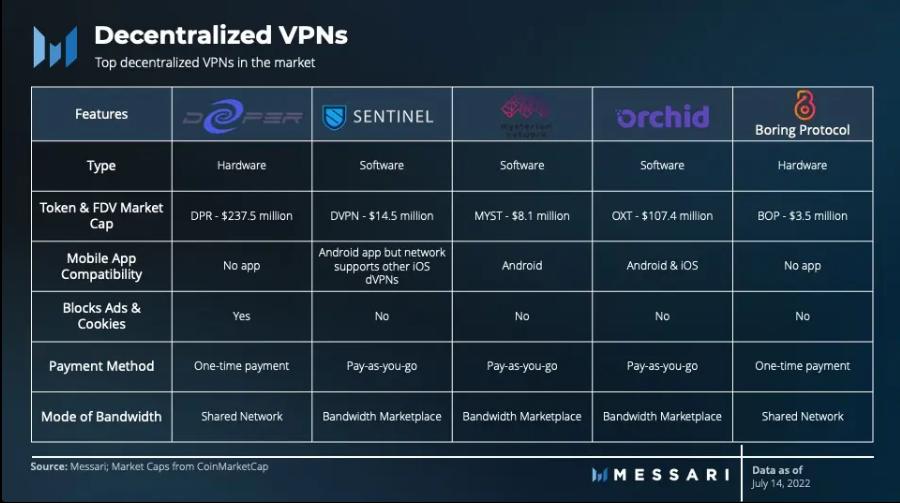
Hardware dVPN vs. Software dVPN
The hardware and software infrastructure of dVPNs each has its pros and cons. With hardware dVPNs, users can purchase integrated devices that allow them to operate nodes and use dVPNs. The downside is that using dVPN requires hardware devices. In contrast, software dVPNs allow anyone to pay only for the service.
Due to physical requirements, hardware dVPNs may face scalability challenges. The initial requirement for new users to purchase hardware devices raises the entry barrier and slows network expansion. However, software dVPNs allow anyone with a network and a computer to act as a node. The software model also enables dVPNs to release mobile application versions, enhancing network accessibility. Additionally, software dVPNs like Sentinel can serve as frameworks for other dVPNs to build upon, allowing for rapid network launches and increased overall scalability.
The main difference between the two types of dVPNs lies in the model of shared bandwidth. Hardware dVPNs typically use shared networks where all node operators provide bandwidth for the network. In contrast, software dVPNs often function similarly to bandwidth markets.
From a security perspective, both hardware and software are robust, but there are clear differences between the two, and variations exist among specific projects. For example, hardware dVPNs can provide firewalls, deep packet inspection, and anti-tracking features for the entire network to prevent attacks and intrusions.
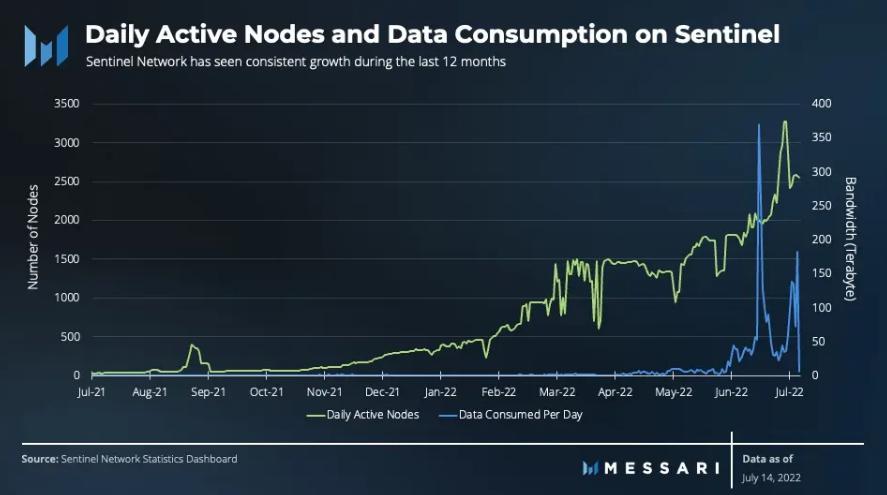
Most of the dVPNs listed in the image above have not released detailed network statistics. However, one of the leading software dVPNs, Sentinel, has a public network statistics dashboard showcasing key metrics. From the dashboard, it can be seen that there were 55,537 active nodes in June 2022, a 21% increase from May 2022, and a 5,859% increase from only 932 active nodes in July 2021. Additionally, the network consumes an average of 7.81 TB of data daily. From May 2022 to June 2022, data consumption increased by 781%, with a total of 1.73 PB of data consumed in June. Over the past year, key metrics of the network (active nodes, session counts, data consumed, and average session duration) have significantly increased, indicating growth in the Sentinel network and other dVPN markets.
Concerns and Risks
Are dVPNs really private and secure, or are there other risks? Hardware dVPN Deeper Network claims that due to its seven-layer firewall, bandwidth cannot be used for illegal activities. However, in relay networks like dVPNs, there are inherent risks associated with connecting entry and exit nodes. The risk is highest at the exit nodes, as technically, the IP address of the exit node is required to connect to external websites. If the firewall is bypassed, the IP address of the exit node operator may be associated with potential illegal activities.
Despite many people valuing data privacy, dVPNs still face some ethical controversies. Some argue that privacy facilitates illegal activities stemming from the negative impacts of anonymity. The line between private and illegal can become blurred. Regardless, dVPNs are not designed for illegal activities. Instead, dVPNs implement protections and firewalls to safeguard users and operators from malicious attacks.
Conclusion
Both types of dVPNs require significant promotion to achieve success. Hardware dVPNs face the dilemma of distributing physical devices to build networks. Software dVPNs offer ease of use for users, making any dVPN compatible with iOS, Android, Windows, or macOS more appealing to users.
While dVPNs may still represent a small part of the rapidly growing Web3 infrastructure, we should note their similarities with larger projects like Helium and Filecoin. Their common goal is to contribute to decentralized networks while incentivizing operators to build networks and communities. The growth of the VPN industry, combined with the user demand for decentralized solutions and the commercialization goals of enterprises, provides a solid foundation for the future success of decentralized VPNs.





























