Nomad cross-chain bridge hacked: The most chaotic "decentralized" robbery in DeFi history?
Author: Gu Yu, Chain Catcher
On August 2, another tragic incident occurred in the history of cross-chain bridges, with the Nomad cross-chain bridge being hacked for over $190 million, evolving into the largest and most chaotic "decentralized" robbery in DeFi history.
According to official information, Nomad is a security-first cross-chain messaging protocol aimed at providing a connective tissue that allows end users to interact securely across blockchains and developers to build cross-chain applications, such as token bridges, native cross-chain assets, cross-chain governance applications, and more.
As a newly launched cross-chain bridge this year, Nomad gained favor from venture capital firms such as Coinbase Ventures, OpenSea, and Polychain with popular concepts like cross-chain communication. In April, it completed a $22 million seed round financing at a valuation of $225 million and quickly became the official cross-chain bridge for EVM public chains like EVMOS, Moonbeam, and Milkomeda, with its locked value rapidly rising to nearly $200 million.
However, no amount of endorsement can guarantee security. Just a week after announcing a new batch of investment institutions, hackers targeted Nomad, causing its total locked value to plummet from $1.9 million to less than $2,000 in just a few hours.
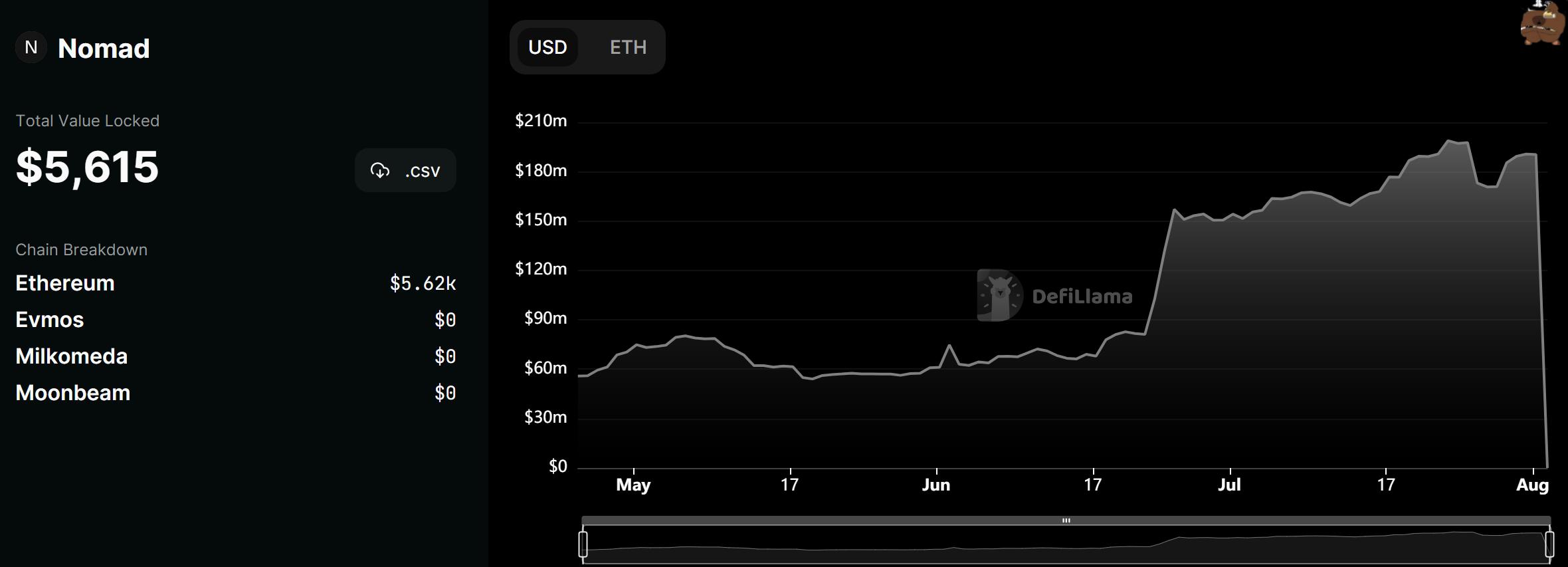
Why did Nomad suffer such a severe attack? According to Slow Mist Analysis, the attack occurred because the trusted root of the Nomad bridge Replica contract was set to 0x0 during initialization, and the old root was not invalidated during the trusted root modification, allowing attackers to construct arbitrary messages to steal funds from the bridge.
In addition to professional analyses, many industry insiders have explained the incident in layman's terms. For example, @0x_Todd from Nothing Research stated that there was a basic error when upgrading the Nomad cross-chain bridge contract, allowing ordinary people to participate in the hack by finding past successful transactions, changing the address, and rebroadcasting. However, the amount could not be changed, so the hacker had to steal it transaction by transaction, giving others the opportunity to rush in and grab Nomad's remaining assets, with some even using ENS to do so, such as a person with ???.eth who stole over $3 million in assets.
Paradigm partner Samczsun remarked that this was the most chaotic hacking attack he had ever seen; you didn't need to understand Solidity, Merkle Trees, or similar concepts. All you had to do was find a valid transaction, replace the counterpart's address with your own, and then rebroadcast.
From these statements, it can be seen that compared to other theft cases in the past, this theft is particularly unique in that it may be the largest and most chaotic decentralized robbery in DeFi history. It was not initiated by a single hacker or a few hackers, but after the initial attacker launched the attack, hundreds of different accounts discovered this method and replicated it to obtain the stolen funds. On-chain fund records also reflect this situation. Currently, multiple WeChat groups have shared screenshots of users profiting significantly using the aforementioned method.
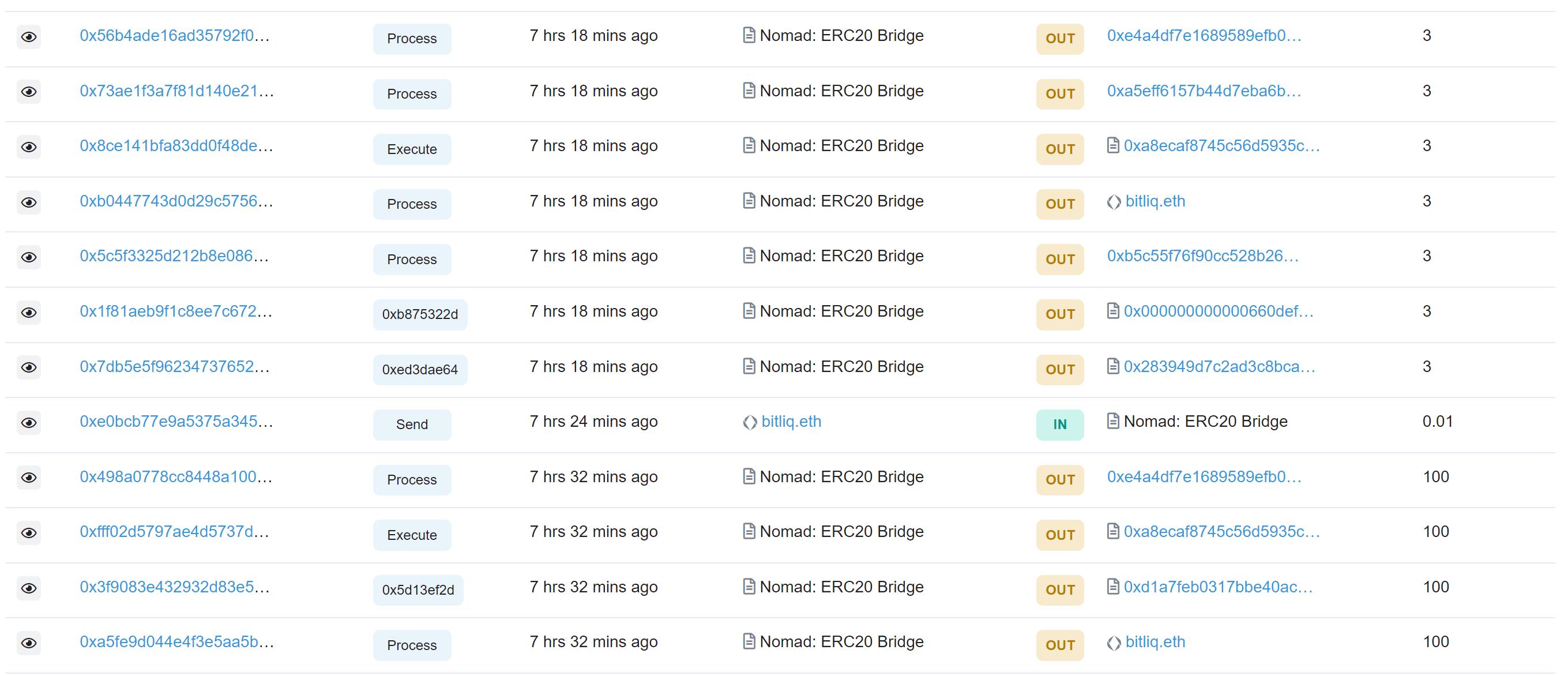
As a result of this incident, Nomad-issued wrapped assets on EVM chains like EVMOS and Moonbeam have been heavily sold off by users, with prices plummeting significantly. For example, currently on the Moonbeam decentralized exchange Stellaswap, one Nomad version of WBTC can only be sold for 2875 GLMR, equivalent to $1871. Some users have traded wrapped assets extensively for on-chain native assets, which has also led to a significant rise in the prices of native tokens like EVMOS, with the EVMOS token price once rising from $1.5 to $2.2, although it has now largely retraced.
However, since many participating addresses are associated with exchange addresses, and some even have ENS domain names, it is expected that the authorities will likely trace some addresses and demand the return of funds. Currently, Nomad has tweeted that impersonators are posing as Nomad and providing fraudulent addresses to collect funds, but the team has not yet provided an explanation for the return of bridge funds.
On the on-chain messaging platform Notifi.xyz, several addresses involved in the attack have proposed to return the funds in on-chain messages, such as "I contacted a Nomad team member and will return all funds, the FBI and the company. Please stay calm, thank you," "I want to protect some funds to safeguard the community, I want to return these funds: 150,000 Card, what should I do? We can't refer to the hacked contract," "We are white hats. Waiting for the rescue address to return," and "Hi, I am returning all funds, just want to help, please don't come after me, I'm not a thief :)"
The professionalism of the Nomad team has also faced some scrutiny during the theft process. At the onset of the incident, the Nomad team stated in their Discord community that they were investigating, at which point the Nomad contract address still had about $100 million in assets that had not been stolen. "The Nomad bridge is an upgradable proxy contract. When the hacker started the slow-motion attack, why didn't the multi-signature stop the transaction?" asked CrocSwap founder @0xdoug.
Additionally, it is worth noting that Nomad founder James Prestwich was previously accused of misconduct before founding the project earlier this year. In November of last year, the Celo public chain cross-chain bridge Optics was temporarily suspended due to its recovery mode being activated, overriding the original multi-signature mode, which allowed a specific address to control the entire cross-chain bridge protocol. James Prestwich, as an engineer for that cross-chain bridge, was held responsible for this.
cLabs CEO Tim Moreton stated that cLabs fired James Prestwich for misconduct, and the reason for the dismissal was not related to the Optics issue or his technical work, but rather because the recovery mode was activated 15 minutes later. In response, James Prestwich refuted this, claiming it was a lie to attack his reputation.
However, as Optics resumed operations, the incident faded away without further developments. Additionally, James Prestwich is also one of the co-founders of the decentralized storage project Storj and served as COO/CFO from 2014 to 2017.
Among well-known cross-chain bridges, currently only Stargate, Hop Protocol, and Connext have not been successfully attacked. How long can they hold out?










