Don't expect CeFi to protect the Ethereum network
Author: @0xTodd, Partner at Nothing Research
Nothing is absolute. The pros and cons of ETH's PoS vs PoW must be analyzed from different dimensions to draw conclusions about their advantages and disadvantages. If we confuse security and decentralization in our discussions, it becomes a case of "talking past each other," and the discussion loses its meaning.
Resistance to censorship can be viewed from at least two angles:
- If censorship is to occur, how long can your transaction be prevented from being added to the blockchain?
- If censorship is to occur, can you ensure that your transaction will still be added to the blockchain?
Resistance to 51% attacks can also be viewed from two angles:
- If an attack is to occur, what is the cost to the attacker?
- If an attack is to occur, what is the likelihood of being able to "rent" the necessary power?
Regarding ETH's transition to PoS, decentralization and security cannot simply be discussed as "increasing" or "decreasing," because their scopes are too broad. Therefore, we will discuss them one by one. The article was actually written last week, but unfortunately, I fell ill recently and only have the energy to publish it today.
First, let's talk about security. There is no doubt that the cost of an attack has increased. This has been discussed many times, so I will keep it brief. When you attack a PoW network with powerful computing power, your actual cost is only the electricity bill; your computing power will not be damaged by your attack, especially considering the high proportion of GPU miners in ETH. After an attack, the worst-case scenario is that you dismantle the mining rig and sell the GPUs.
However, PoS is different. If you attack the ETH PoS network, your staked ETH will be lost. This raises the cost of an attack by hundreds of times. It is important to note that attacking PoW is a temporary investment, while attacking PoS is a permanent expense.
However, from the perspective of "renting," it is slightly worse. Renting 51% of ETH's computing power is a "herculean task." This is not a cost issue, but rather a binary issue. This is mainly due to the physical properties of PoW, as miners are distributed around the world.
But PoS is different. The circulating supply of ETH is 120 million, while currently, over 13 million are staked on the beacon chain. Theoretically, if you can "borrow" just 5% of the circulating ETH, you could execute a 51% attack on the network. Of course, I am not saying this is easy; it is still "very difficult," but it is no longer "impossible."
Moreover, in a centralized world, borrowing may require collateral, or it may be based on credit or even power, such as regulation, which introduces our second issue.
Resistance to transaction censorship is part of the decentralization characteristic. This discussion began here:
In simple terms, he believes that currently, 2/3 of the nodes on the ETH beacon chain are under U.S. jurisdiction, which could lead to censorship. The post is lengthy, so take your time to read it.
Let's take Tornado as an example. If U.S. regulators require the 2/3 of mining pools to block a Tornado transaction, this would significantly increase the time it takes for the transaction to be added to the blockchain. In the past, your transaction could go live in 12 seconds; in the future, it might easily take over 30 seconds, or even one to two minutes if luck is not on your side.
I calculated a curve (see below), and the probability of being banned continuously for one minute is about 10%, which is quite unpleasant.
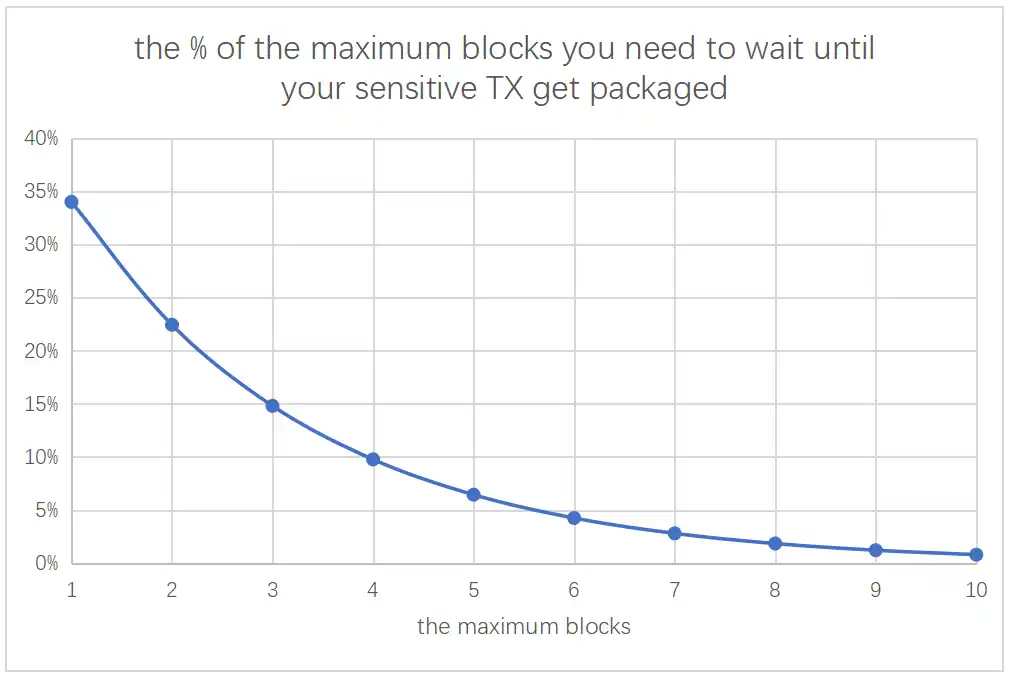
However, this is not a problem with the PoS consensus; it is actually an issue of the U.S.-China switch. In the past, the top PoW mining pools also had a high market share, with the top 10 accounting for about 78%. If they unite to censor your transaction and prevent it from being added to the blockchain, they can do so. https://etherscan.io/stat/miner?range=7\&blocktype=blocks
However, many of these mining pools with Chinese backgrounds have many mining farms in Russia and Central Asia. China and Russia can be said to be among the few regions where the U.S. finds it difficult to directly regulate. All of this is not related to technology but to the participants involved.
Now, PoS mining pools, whether Lido, Coinbase, or Kraken, are all based in the U.S., and thus are subject to various constraints. Although they are currently making positive statements, based on their tone, future censorship of illegal transactions is still not a low-probability event. Therefore, in terms of the ability to censor, PoS is indeed inferior to PoW.
However, there is another metric—discussing the worst-case scenario, which is whether you can ensure that your transaction will at least be added to the blockchain. Let's continue to calculate. If we still consider the 2/3 scenario, then in 98% of cases, your transaction will definitely be added to the blockchain within 10 blocks. There will always be mining pools that ignore U.S. regulatory demands; all you have to do is wait.
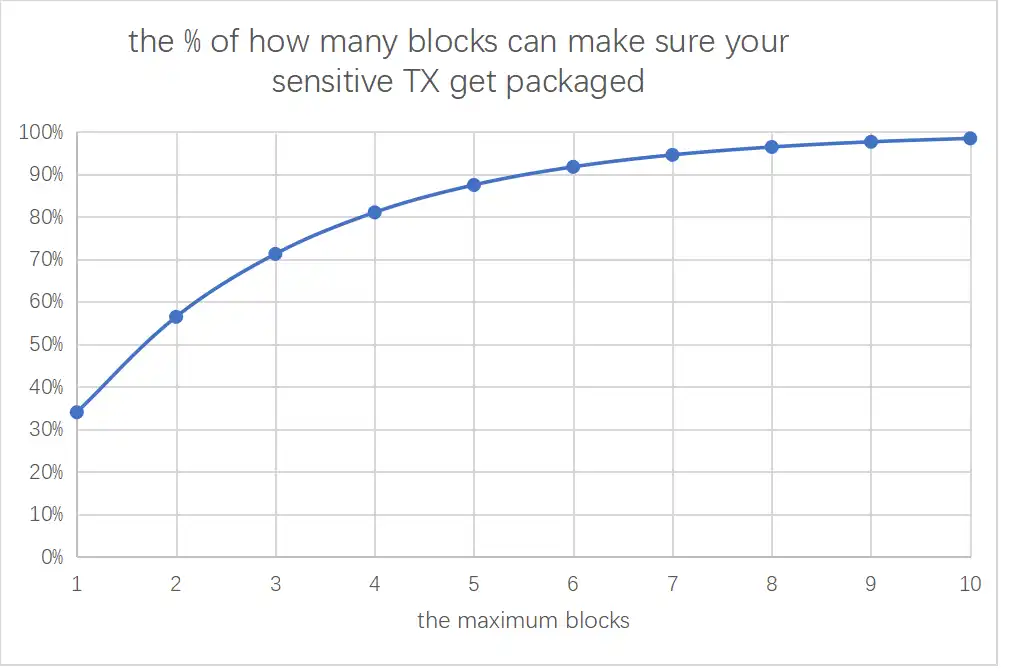
In other words, the U.S. can suppress your transaction for a few minutes, but it cannot suppress your transaction forever. This is completely different from AAVE blocking Sun Ge and Shen Yu. AAVE is a single point, while mining pools are multiple points.
Additionally, as long as a small portion of nodes stick to their principles and continuously switch their mining pools, your transaction can be added to the blockchain.
Of course, PoW can also switch mining pools at will, but PoS has slightly higher anonymity. In real life, many people know you run a mining farm, but very few know that you are secretly running a PoS node on a particular server. From this perspective, PoS is slightly superior to PoW, though not by much.
Many people will continue to speculate that if regulators discover that your privacy transaction, although slow, can ultimately evade sanctions, what would happen if they decide to roll back directly?
First of all, this has already gone beyond the scope of transaction censorship and can be equated to a direct attack on the network. The probability of such a situation occurring is very low, but it is still a risk.
For example, if a Tornado transaction of yours is finally added to the blockchain through a node not subject to U.S. regulation, the regulators controlling 2/3 of the large mining pools could issue a directive to directly fork the network and remove the block containing your transaction, making it impossible for your transaction to ever be added to the blockchain. If they cannot delete your transaction, they can simply reject your block. From the current PoS perspective, this could potentially be achieved in a single echo.
In response to such situations, some in the Ethereum community believe that social slashing should be implemented, directly confiscating the collateral of nodes that engage in such actions. However, this could lead to new forms of tyranny. Ethereum should not adopt rules that are not written on the blockchain. There is a article that organizes some good information on this topic.
Moreover, current mining pool nodes will connect to MEV tools like Flashbot, but Flashbot is also subject to regulation, which could lead to situations where non-compliant transactions simply do not appear in Flashbot's transaction list, and the nodes connected to it would also be affected. Therefore, more tools are also needed.
Today, Coinbase stated that it will never compromise with regulators and would rather abandon its business than comply with censorship. But to be honest, staking yields are enormous, with staking APR expected to reach 8%-10%, plus a commission of 10%-20%. Just in Coinbase's cold wallet, there are millions of ETH; if they do not stake, they would lose tens of thousands of ETH in a year.
This business is impossible not to engage in; however, regulation is also impossible to ignore.
Therefore, we cannot rely on CeFi, whether it is Coinbase, Lido (semi-CeFi), or Flashbot (centralized tool). We still need to make improvements and optimizations at the technical level, specifically regarding the blockchain itself, and this work is undoubtedly a long-term endeavor.
Only in this way can we protect our Ethereum network.











