The Ultimate Guide to Web3 Social: A Thriving Field Full of Identity Crises
Original Author: lingchenjaneliu
Original Compilation: Block unicorn
Summary:
Existing web2 social network platforms have caused issues such as data and security breaches, manipulation of public opinion, and the spread of false information.
Digital assets created based on interoperability standards on public blockchains are portable and transferable, so user history does not remain on any specific platform.
A core philosophical principle of Web3 is that there are more ways to provide value to the ecosystem beyond just providing value through capital—value should be earned, not just bought.
An open social stack includes data infrastructure (decentralized storage and data layers), middleware (digital identity, social graphs, and credential protocols), and social applications.
Social network platforms often face cold start problems; with an open social stack, new platforms can leverage middleware to develop products and quickly test product-market fit.
The most important issue that decentralized social needs to address is the decentralized storage of dynamic data. Protocols like Ceramic Network and Tableland are tackling this challenge.
Every social network relies on a social graph. Leading protocols for building an open social graph with a strong ecosystem are Lens Protocol and CyberConnect.
The challenges faced by web3 accounts and identities arise from the unclear definitions of wallets, accounts, and identities in web3, and the implementation of digital identity projects often mixes these three concepts together.
There should be an identity framework to help users access web3 applications. The identity framework includes identities used in different scenarios: public identity, agent identity, and master identity.
The challenges we see: 1) Economically incentive-driven social; 2) Data composability is not as simple as we imagine; 3) Poor user experience and small user base; 4) Not solving pain points, not creating value for users.
Web3 social can only succeed if the existing address-based identity shifts to a person-based identity, focusing not only on contract status (showing assets owned by an address) but also on relational status, which is the social status a person gains through relationships with others.
What is Web3?
Web3 is a term that does not have a fully defined characterization. This term encompasses decentralized ideas and visions driven by community and user ownership. An article about web3.0 written by Him Gajria puts it best:
Web1 is read-only: 1) The web hosts content, 2) People can consume content but cannot share it.
Web2 is read-write (creation): A web that supports user participation (like today's TikTok, YouTube, WeChat, Twitter).
Web3 will be read-write-own: 1) Built on peer-to-peer networks, 2) Achieving interoperability, allowing different applications to connect and communicate in a coordinated manner.
In the Web2 world, the dominant category of networks is social networks, such as Facebook and YouTube. Social networks allow users to interact with the network, not just consume its content. In the web3 social ecosystem, a large number of web3 social startups have emerged. Although web3 has yet to see a platform equivalent to Twitter or Facebook, many believe that the narrative of data ownership and the financial incentives of networks, NFTs, and tokens will solve the cold start problem and ultimately bring enough creators and audiences to the platform.
The Demand for Web3 Social
Web3 presents a different value proposition, fundamentally different from the centralized platform-dominated web2. Chris Dixon explains the inherent problems of centralized platforms in this article. The model followed by centralized platforms is that once the usage rates of the platform's users and creators reach strong network effects, the participants in the network become victims of the platform's growth. The growth power in the later stages of the platform comes from extracting user data to increase advertising revenue, leading to data breaches and security vulnerabilities.
In addition to data and security breaches, social network platforms also cause psychological and social problems, including addiction, mental illness, manipulation of public opinion, and the spread of false information.
Recent condemnations of social network platforms have come not only from authorities and users but also from developers who once worked for well-known social network platforms. In the documentary "The Social Dilemma," developers revealed how social network platforms exploit user data to develop their products, creating a positive intermittent reinforcement effect in users' minds.
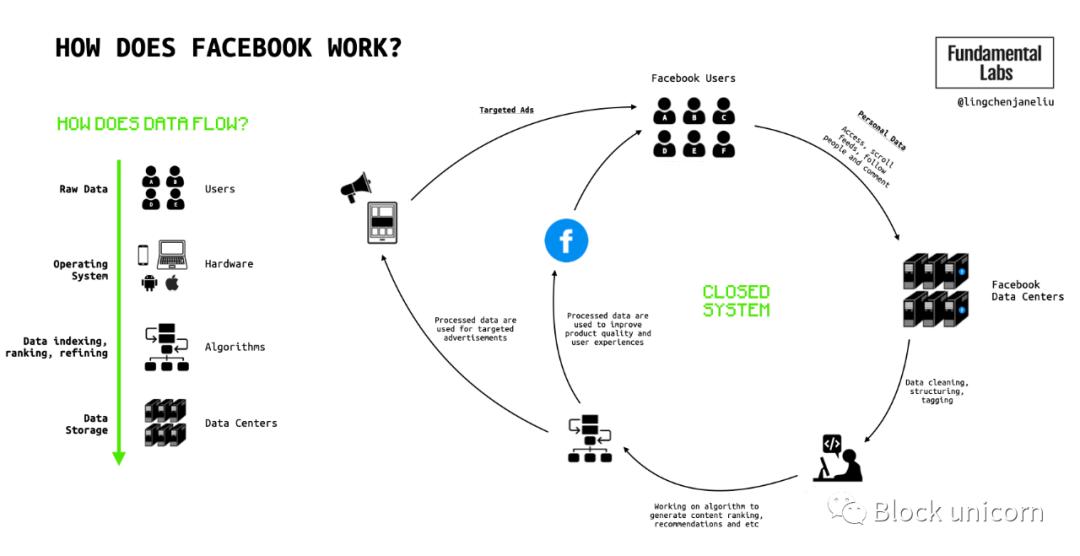
Figure 1: How does Facebook work?
Based on this premise, beyond monetizing user data to create platform stickiness, the web3 social stack is dedicated to building an open platform where users can own any content they create, the digital objects they acquire, and even their social graphs. Digital assets created based on interoperability standards on public blockchains are portable and transferable, so users are not trapped on specific platforms.
What is a Social Graph?
A social graph is a representation of the relationships and connections between people, groups, and organizations within a social network. Existing social network companies like Instagram, Facebook, and LinkedIn are composed of such social relationship graphs between individuals.
Existing mainstream internet platforms are built on aggregating users and user data. As these platforms evolve, their ability to provide value also increases. The platform's network effects keep dominant platforms ahead. User behavior data from mainstream social network platforms helps them optimize algorithms, making their content supply and ad targeting significantly better than competitors. Amazon gains comprehensive data by analyzing profit margins and consumer demand to understand customer needs, thereby optimizing delivery logistics and developing its product lines.
In the business model of traditional internet platforms, users and their data are key sources of competitive advantage. Therefore, platforms typically do not share data. As a result, if users decide to leave the platform, they find it difficult to take their social graphs and content with them.
Why is Identity Isolated?
The internet companies we interact with all have their own databases. Because the data between these companies is disconnected, the data is isolated. In contrast, databases in web3 can interconnect in an open and accessible manner.
In web3, users do not access a centralized infrastructure (IaaS) provider or a closed centralized network, but rather a public network independently operated by thousands of nodes that adhere to strict rules defined by network code. Users and businesses can build and contribute to decentralized web3 applications, communities (decentralized autonomous organizations), and the infrastructure that drives these applications (node infrastructure). This means that no single entity can control access to data on the network, and any attempt to do so will be rejected by other nodes on the network (see Figure 2).
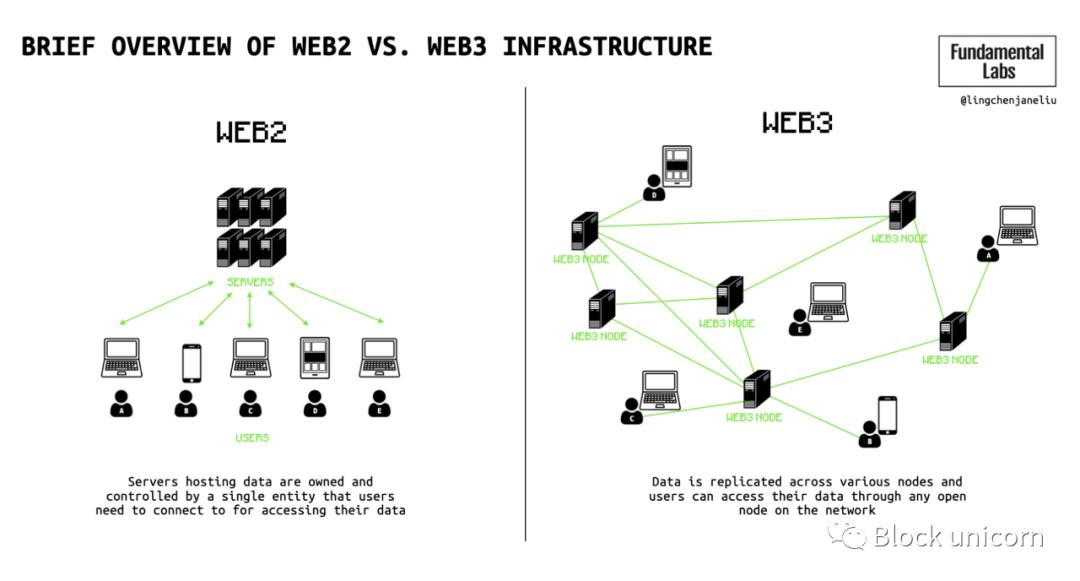
Figure 2: A brief overview of Web2 vs. Web3 infrastructure
Essentially, data is stored on a network composed of independent nodes, each ensuring that only data owners can decide how their data is handled. This contrasts sharply with centralized servers controlled by web2 cloud service providers.
A core philosophical principle of web3 is that there are more ways to provide value to the ecosystem than just capital—additionally, value should be earnable, not just purchasable. This is a fundamental difference from existing structures, where those who own capital earn more income through investment than through work, leading to an ever-widening wealth gap over time.
Allocating ownership to participants is also a significant shift; existing platforms are built by employees and investors, where meaningful ownership belongs to employees and investors. In this traditional web2 model, the content and contributions of these users make these platforms valuable, but ownership does not belong to the users.
Open Social Stack: Current Market Landscape
After carefully studying existing projects building open social stacks in web3, I have mapped out a market landscape that includes multiple components and layers (see Figure 2). In addition to the underlying layers, including data infrastructure and decentralized storage, middleware such as decentralized identity, social graphs, and credential protocols are key layers in the entire open social stack. Any application can build on top of them and use existing user networks without having to build their own user network from scratch.
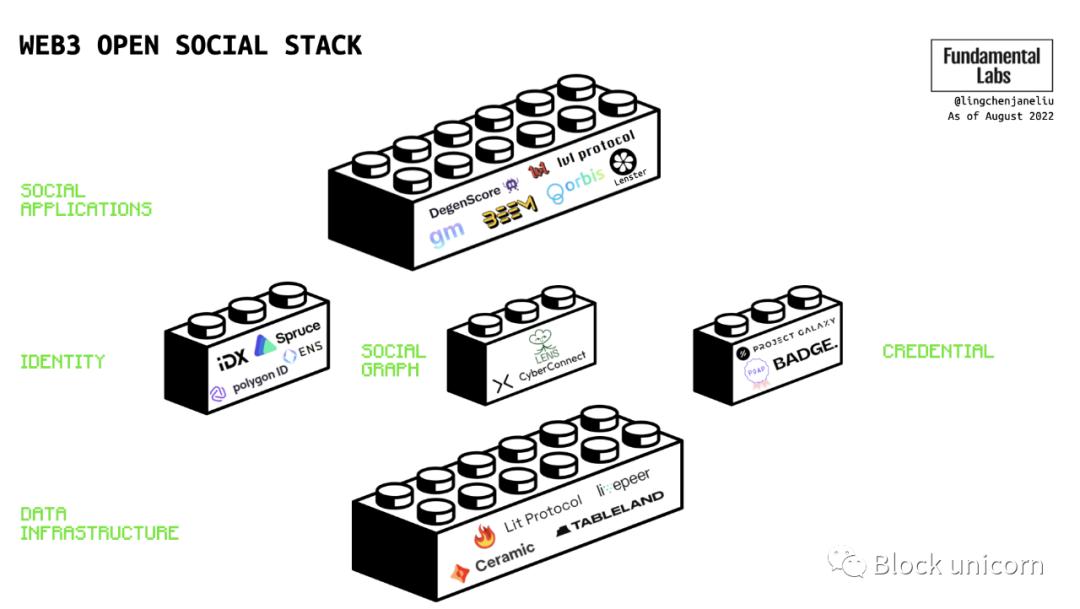
Figure 3: Market landscape of the open social stack
Overview of the Open Social Stack
- Data Infrastructure: Data infrastructure includes decentralized storage (research on data can be found here or in the original text) and data layers built for dynamic data, catering to the needs of social applications that generate large amounts of underlying data value.
- Middleware: Middleware is computer software that provides services to software applications. Middleware accelerates the development of decentralized applications by simplifying the connections between applications, application components, and backend data sources. Common middleware in the open social stack includes digital identity, social graphs, and credential protocols.
- Social Applications: Social applications are software applications that facilitate the creation and sharing of information, ideas, interests, and other forms of expression through virtual social interactions and networks. In Web2, there are Facebook, Instagram, YouTube, and TikTok. In Web3, there are Orbis, Lenster, lvl protocol, and Cent.
The open social stack creates a paradigm shift with very strong portability and connectable/disconnectable identities that exist in users' encrypted wallets. Think about it: our web2 online activities are a form of our identity. The photos we post on Facebook and Instagram, as well as the profiles we create on Twitter and LinkedIn, are all part of our identity. The challenge we face here is that our identities only exist on the platforms where our actions/activities take place, and identities are isolated. With the walled gardens built by web2 giants, we cannot simply integrate our Instagram identity and connect it to YouTube to fine-tune content recommendations to align with our interests.
Social network platforms often face what is known as the cold start problem: new platforms struggle to acquire new users and onboard them, which is why hackers play a very important and prominent role in the traditional internet industry. With the open social stack of web3, new platforms can leverage middleware, such as social graphs and credentials, to develop products and quickly test product-market fit. Because data is transparent, competitors can view mainstream platform data and offer relevant incentives to high network value users to attract them to their platforms. However, since users can easily transplant their digital assets to different platforms with zero switching costs, platforms need to compete with better user experiences and build closer ties with communities to keep their missions and values aligned.
Let’s take a look at each layer of the open social stack.
Data Infrastructure
The most important issue that decentralized social needs to address is the decentralized storage of dynamic data; protocols need to support dynamic data storage before they can support streaming, social media, and other related applications.
Due to social network applications often generating large-scale but low-value transactions, such as sharing, liking, or following, it is economically unfeasible to conduct these transactions on Ethereum. Therefore, finding a scalable solution that facilitates transaction settlement becomes particularly important.
Due to the immutability of on-chain data, it is challenging to build social applications on top of the data layer. However, some protocols are attempting to address this issue, such as Ceramic, Livepeer, Lit Protocol, and Tableland. These protocols aim to manage and store dynamic data, such as images, videos, and text.
Ceramic Network
Web2 applications run on code, with their functionalities, content, and product recommendations driven by complex algorithms fed by user data. The information filling the websites that users see, whether user data or application data, is typically driven and determined by algorithms designed by the platform. In contrast, so far, the web3 stack and dApps environment lack these data-driven functionalities. The root cause lies in the immutability of on-chain data. Ceramic Network is trying to solve this problem by providing a data layer on top of IPFS to manage and track state transitions and associate data with data structures, making data easy to read and write. The protocol implements mutable data tables bound to users, allowing data-driven applications to be built on top of it.
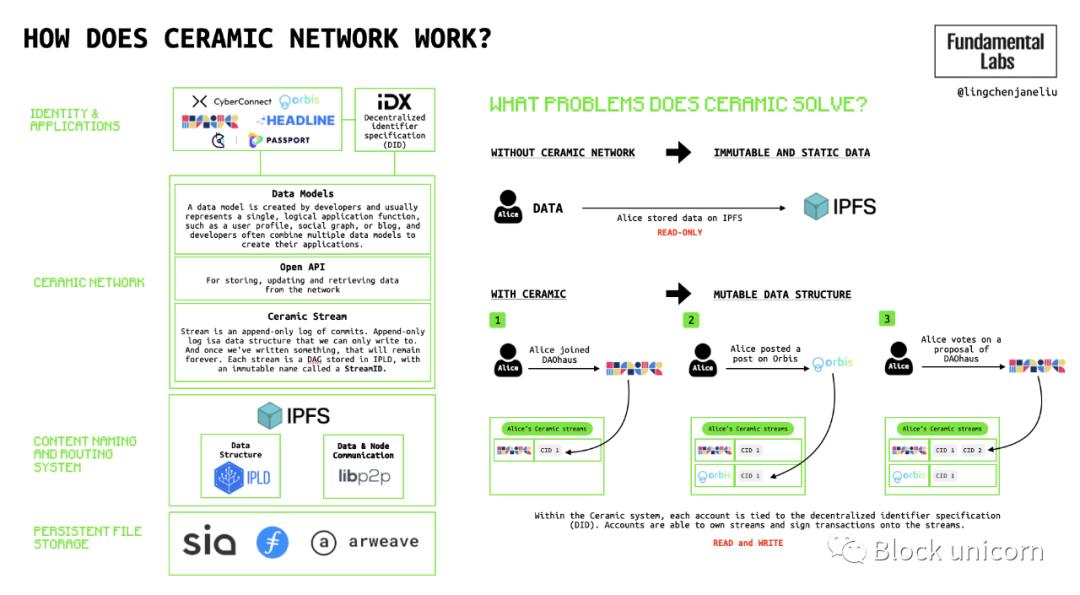
Figure 4: How does Ceramic Network work?
Advantages of Ceramic Network
- Users: When data is stored on IPFS, it is difficult for users to track data over time. However, with Ceramic, data is stored with users associated with keys, along with their identities tied to any blockchain wallet. Each time a user arrives at an application, the data is recorded in Ceramic on IPFS. This data corresponds to the data model created by application developers, allowing users to migrate their portable data to any platform when they go to another application.
- Developers: For developers, Ceramic provides a shared database to construct data and establish data-driven functionalities. Ceramic has a data model marketplace for developers to create their own data models corresponding to specific functionalities they desire.
Tableland
Similar to Ceramic Network, Tableland attempts to address the limitations of the Ethereum Virtual Machine (EVM), which has limited storage space in its smart contracts and high costs for updating, writing, and storing data on-chain.
Existing web3 applications often use hybrid methods to store application data. Taking NFT projects as an example, NFTs in these projects exist in two parts: smart contracts and the metadata of the artwork. Smart contracts exist on the blockchain, usually Ethereum, and contain a set of rules to facilitate transactions. Smart contracts also include a link to a server that stores the digital artwork. In other words, the digital artwork may not exist on the blockchain and may be stored off-chain. NFT projects often utilize centralized databases like AWS or Google Cloud to store structured data.
However, using decentralized storage providers to host their metadata is relatively safer because if a centralized server goes offline, the digital artwork may be lost. In contrast, with decentralized storage providers, if a storage location (node) fails, the digital artwork may be found at another storage location. The downside of the current decentralized storage approach is that the metadata itself cannot be changed and is difficult to query or compose. In contrast, centralized storage providers can make metadata dynamic and support query functions. However, data stored in centralized storage providers is neither open nor composable.
Tableland provides a technical solution to address the limitations of on-chain data—immutability, expensive storage costs, non-composability, and difficulty in querying. Tableland establishes a data layer that allows users to store, read, and write data more cheaply, with more storage space compared to a pure EVM environment. Tableland achieves this through two components: an on-chain registry with access control logic (ACL) and off-chain tables. Each table in Tableland is minted as an ERC721 token on the EVM-compatible layer. This means that the access control logic that grants data writing rights exists in the EVM, and users hold this right through NFTs stored in their Ethereum wallets. The protocol has two main components: the on-chain registry owner and the off-chain Tableland Network. The link between on-chain and off-chain is handled at the smart contract layer, which possesses immutable qualities.
▲ On-chain table owner: Sets ACL permissions for a registry.
▲ Off-chain (decentralized) Tableland Network: Manages the creation and subsequent changes of the tables themselves.
In short, Tableland is like IPFS with an SQL layer on top, providing more flexibility and adaptability.
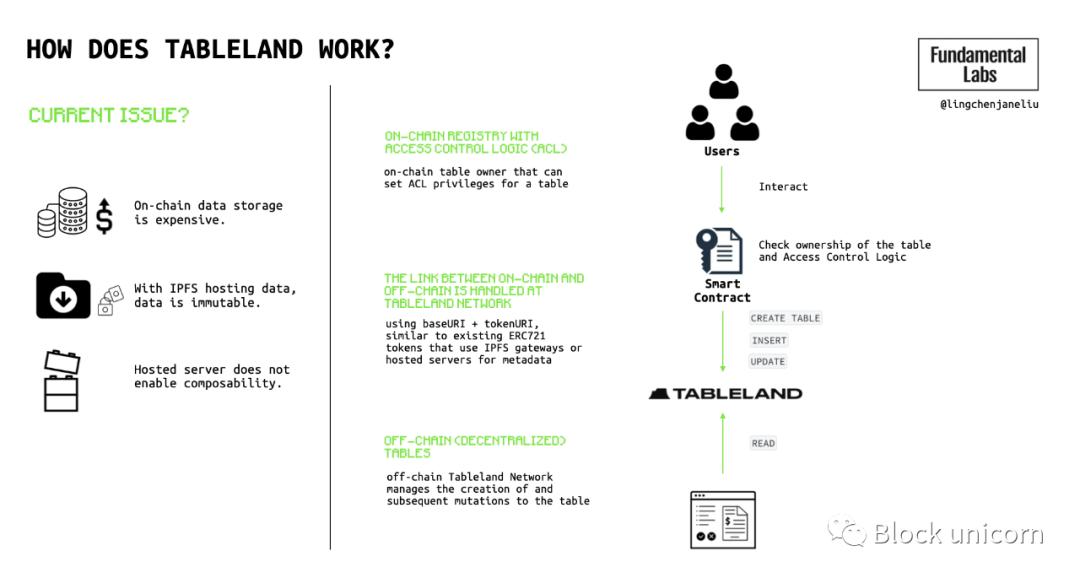
Figure 5: How does Tableland work?
What is Access Control Logic?
Access control logic is an automated system that controls an individual's ability to access one or more computer system resources, such as networks, applications, or databases. Access control logic systems require some mechanism (such as a PIN, card, biometrics, or other tokens) to verify an individual's identity.
What is SQL?
SQL stands for Structured Query Language, a language used by databases. This language allows for the use of tables to process information and provides a way to query these tables and other related objects (views, functions, procedures, etc.). Most databases, such as SQL Server, Oracle, PostgreSQL, MySQL, and MariaDB, use this language (with some extensions and variations) to handle data. Through SQL, users can insert, delete, and update data. Users can also create, delete, or modify database objects.
Middleware
Social Graph: Every social network relies on a social graph. Social graphs are crucial for all communications, from posts and likes to direct messages. Without a company or entity responsible for storing data, a shared public social graph cannot exist, and some protocols are attempting to achieve this.
Lens Protocol
Lens Protocol is a composable and decentralized social graph. Social applications include user profiles, followers, posts, comments, shares, and likes. These components define the basic data layout and the relationships between data, such as who follows whom or who posted what content.
On Lens Protocol, key functionalities of social media are provided by NFTs and owned by users. User profiles are also NFTs, each follower is a unique NFT, and each post represents an NFT.
NFTs on Lens Protocol
- Profile NFT: The Profile NFT contains user-generated posts, retweets, comments, and replies. A single address can own its profile NFT, and one address can contain multiple profile NFTs, while a profile NFT can be owned and operated by a DAO through a Multisig wallet.
- Follow NFT: Each time a user follows another user, the other user receives a follow NFT with a unique token ID.
- Post NFT: Content created or shared can be a posting NFT, similar to posts on traditional social media.
- Mirror NFT: Similar to the retweet function on Twitter. Users use the Mirror function to reshare a post. It is possible that, due to sharing by individuals, users can earn a share from anyone who collects the original content.
- Collect NFT: Users can collect (purchase) published NFTs from users they follow and create their own NFT collections.
- Comment NFT: Similar to the comment function on traditional social media.
Figure 6: Lens Protocol ecosystem
The social graph designed by Lens Protocol cannot be easily forked because all data is stored in the form of NFTs in users' wallets. Lens Protocol has a strong ecosystem, with various applications built on its foundation. The ecosystem of Lens Protocol creates a strong position relative to competitors, and as the user base of Lens Protocol grows with its ecosystem, more data will be fed back into the social graph protocol.
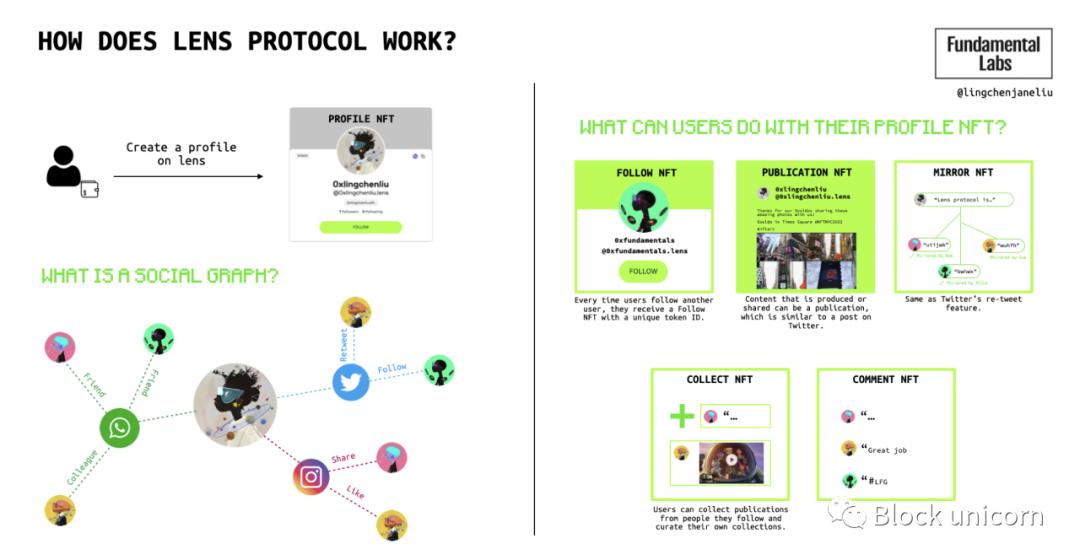
Figure 7: How does Lens Protocol work?
CyberConnect
CyberConnect is a social graph protocol that allows dApps to access and use user-provided social graph data. The CyberConnect ecosystem is very robust, integrating many web3 applications, including Project Galaxy, Mask Network, Light.so, Grape.art, NFTGo, Metaforo, zklink, and more.
CyberConnect's social graph is divided into two parts: 1) Follow button; 2) Follow and follower lists. Web3 applications can directly insert CyberConnect's social graph module to develop their applications, which can help solve cold start problems and return data ownership to users. Thus, users can switch between different applications using their social graphs. CyberConnect's solution allows users to have a more comprehensive identity across all applications.
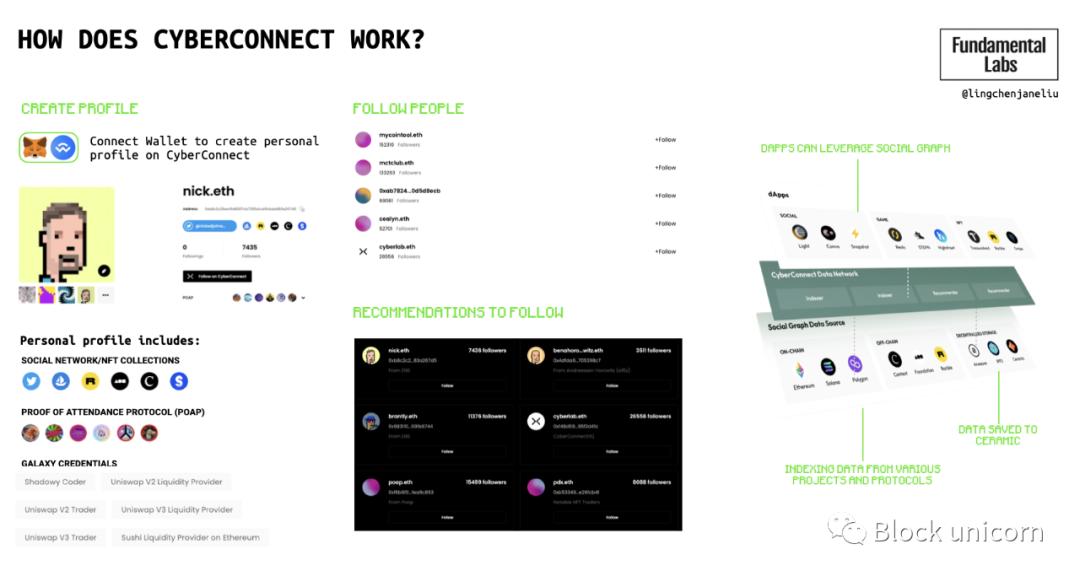
How CyberConnect Works ⬆
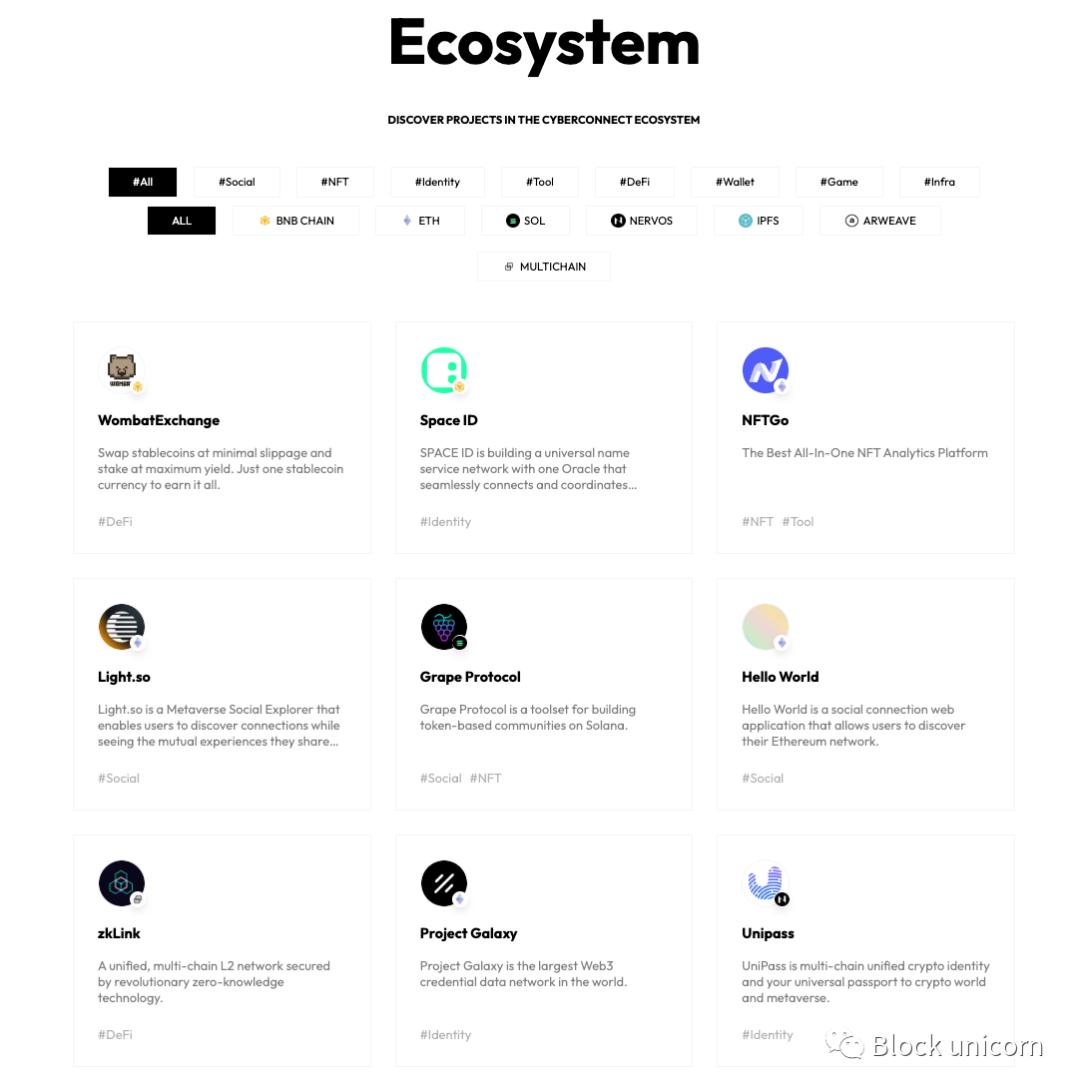
Figure 9: CyberConnect ecosystem
Traditionally, a social network application builds its moat not only through good product design and user experience but also through user data-driven network effects. Therefore, newcomers find it difficult to shake the status of mainstream social network platforms because users cannot simply take their data to another platform and enjoy the same experience without building a new profile, connecting with people, and generating enough data to provide better recommendations and content curation for the platform. The cold start problem is one of the biggest challenges that social network platforms need to overcome. Without initial data, it is challenging to elevate a new social network.
What is the Cold Start Problem?
User or visitor cold start simply means that the recommendation engine encounters a new visitor for the first time. Without user history, the system does not know the user's personal preferences. Understanding visitors is key to creating a good user experience for them.
Identity Recognition
Identity is a person's self-awareness, established by their unique characteristics, relationships, and social roles. Moreover, identity has continuity, as people feel they are the same person over time despite many changes in their environment. So far, identities in Web3 consist of low-dimensional data, often emphasizing their decentralized nature; thus, decentralized identifiers (DIDs) are the most common solution for identity recognition in Web3.
What is a Decentralized Identifier (DID)?
According to W3C (World Wide Web Consortium), a Decentralized Identifier (DID) is a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (such as an individual, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID.
Figure 10: On-chain identity vs. real-world identity
Why Do We Need DIDs?
- DIDs allow for unique, private, and secure peer-to-peer connections to be established between parties.
- The decentralized nature can always use credentials for verification.
- Each party—individual or organization—can create different DIDs at their discretion. Using separate DIDs for different digital relationships and contexts can prevent data correlation.
- DIDs are fully controlled by the identity owner, and the decentralized identity system is independent of centralized registries, authorities, or identity providers.
Transitioning Authentication Methods to Passwordless Approaches
If we learn from the authentication processes of web2 or the physical world, in the early days, most web2 applications used account + password as the authentication method. Users often set the same account and password for different websites and platforms, which is very insecure.
As mobile devices and applications emerged and occupied most of users' time, applications began to adopt a new authentication method—phone numbers and verification codes. To facilitate users, many applications adopted one-click verification based on Google/Apple/WeChat/Alipay, leading to a decrease in applications that only supported account ID + password.
Account Separation and Identity Aggregation
In China, internet giants like Tencent and Alibaba own multiple applications spanning financial, social, entertainment, and e-commerce services. They have developed a comprehensive credit system based on users' historical transaction data, social behaviors, and identity verification.
Most applications in China support one-click login and have credit systems and credit scores from WeChat (a messaging, social media, and mobile payment app in China) and Alipay (a payment app and digital wallet under Alibaba). For example, when users borrow shared bikes, they can unlock the bike by scanning the QR code with WeChat or Alipay without registering and creating a new account. The user experience becomes smooth and seamlessly linked, requiring only one authorization, which is a perfect example of account separation and identity aggregation. The aforementioned credit system/credit score is our aggregated identity in the digital world, a system that includes user identity data and credit ratings. Applications can simply integrate the credit system into their applications to request authorization to read users' identities and create temporary accounts; such identity and account experiences are needed in web3. Users should be able to easily participate in DeFi, play games, and interact on social applications with different accounts while having an interoperable identity across different accounts.
From Wallet Address to Identity
A web3 user typically has multiple wallet addresses across different blockchains due to security and privacy issues, as well as the near-zero cost of creating a new wallet address. In addition, a typical internet user also has accounts and social profiles in various web2 applications, such as Twitter, Facebook, and Google. Currently, there are multiple DID projects being established to address different aspects of the issues surrounding web3 identity and accounts. The concepts and implementations of DIDs are mixed with wallets, accounts, and identities, and the definitions of these three concepts in web3 remain vague and undefined. Many times, we view wallets as accounts and accounts as identities. Therefore, it is necessary to propose an identity framework to better assist users in accessing web3 applications. Identities used in different scenarios include public identity, agent identity, and master identity.
Public Identity:
- Purpose: The main role of public identity is to facilitate external relationships, to identify the user's identity, and to make identity clearer in social relationships.
- Use Case: Public identity is a collection of credentials, identifiers, behaviors, relationships, and reputations. Public identity can actually be unified with agent identity and share the same account address based on user needs. For example, if some users are more concerned about security and privacy, their public identity can be a separate account specifically for external display and relationship building.
- Examples: ENS, Lens, and Nametag.
Agent Identity:
- Purpose: The purpose of agent identity is to disconnect the wallet address from the account, thus creating a firewall between the wallet and the application.
- Use Case: Users can create a series of accounts with exclusive functionalities, such as social accounts, gaming accounts, trading accounts, and anonymous accounts. All agent accounts can be controlled by the master identity and can be used to reset keys.
- Examples: Unipass, Spruce ID, Web3Auth, and IDX.
Master Identity:
- Purpose: To separate account authorization from account access.
- Use Case: When an agent identity is created, the master identity is used to authorize the agent identity. Users can manage their wallet accounts just like in web2 applications. When risks or key losses are detected, the keys of the wallet account can be retrieved and reset.
- Examples: Web3Auth, ERC-4337 abstract accounts.
Social Applications
Frontend applications are user-facing, with use cases including social media, video streaming, and community tools. Social applications can utilize middleware projects, such as open algorithms, public social graphs, and open digital identities, to customize and optimize their products. Through the middleware of the open social stack, multiple applications can exist on the same user data and infrastructure components, changing the competitive landscape. Applications will find it difficult to resist competition and establish competitive advantages because users can seamlessly switch between different applications. Therefore, web3 applications need to explore ways to acquire users, retain them, and develop profitable models.
Web3 Social: All Talk and No Action?
The web3 social space has become hot with the influx of developers and capital, but currently, no protocol dominates the market. Why is that? We will explain these challenges in the following paragraphs and discuss where we can explore to accelerate growth in this area.
Challenges of Web3 Social
From Economically Incentive-Driven Social to Relationship-Driven Social
True social refers to users forming connections with others based on shared interests, topics, and backgrounds, while on-chain social is still far from reality. The reasons behind this are:
- Speculative and Financially Incentive-Driven Behavior: Currently, on-chain social behavior is driven by speculation and economic incentives; on-chain social data is not based on users attempting to establish natural and effective connections with others.
- Social itself is about interaction and connection between people; now in web3, users interact through addresses. The current technological reality is that addresses only store data such as transaction history and assets. Since this data cannot help identify real and valid target users, connections are established very inefficiently and ineffectively.
Data Composability is Not as Simple as We Imagine
Although web3 has the potential for composability, and applications should use different data models generated from various protocols, the reality is that protocols define their own data and business metrics based on their business logic and operational needs. It is unrealistic and impractical for applications to simply acquire and use any data models and algorithms created by other protocols (see Figure 11).
Figure 11: How does data drive the operation of the internet industry?
From factual data, such as browsing duration, ticket size, and purchased items, to analytical data at the business level, such as retention rates and conversion rates, multiple steps are involved. The data models and business metrics used to profile users and design social recommendations, content supply, targeted marketing, and algorithms are truly valuable, as they help optimize products and operations, driving business and user growth.
Better User Experience Can Accelerate User Adoption
Poor User Experience Leads to a Small User Base:
- Too Many Industry Jargon: Airdrop, cold wallet, DeFi, diamond hands, fiat currency, hard fork, gas, hash rate, private key, proof of stake, seed phrase, stablecoin, and smart contract are just a few terms. In a foreign field filled with research, content, and applications full of abbreviations and industry jargon, it is very difficult to engage new users.
- Poor user experience is a major barrier to mass adoption: User experience is not just about how the product looks, but also how it works, whether installation is easy, whether it is easy to use, the scalability of the solution, whether costs are high, how fast transactions are, and so on. For non-geek users, knowing how to add networks to their MetaMask wallet, the differences between different chains, and how to transfer tokens to different networks is very challenging. Traditional web development has focused on providing user-friendly solutions for decades, and when the older generation can intuitively use the web, it is difficult to convince users to switch to web3 when the user experience of web3 is generally inferior to that of web2.
Web3 Should Solve Real User Pain Points and Bring Unprecedented Value to Users
- Great narrative, but the business model is still unclear: The decentralization of data and information and user ownership of data and content is a great narrative, but when decentralization brings higher costs for users to use these protocols, decentralization itself does not have immediate practical significance or urgency for most users. In contrast, centralized platforms absorb transaction and platform support costs, including storage, bandwidth, computing power, product development, and operations, and profit from the data they collect to support platform development and maintenance. Web3 still needs time to find its native business model, which should differ from existing web2 models. So far, we have not seen the occurrence of business model innovation.
Where Can We Explore?
Before social applications thrive, digital identity is a key cryptographic issue that needs to be addressed.
Web2 Digital Identities are Isolated and Not Fully Defined by Users:
- Existing digital identities on web2 are isolated, closed, and exist on each independent platform. Moreover, as traditional social network platforms have been building business models, platforms create user tags based on user behavior and design a series of algorithms that utilize these user tags to recommend content, increasing user retention and dwell time, optimizing paid advertising revenue. Therefore, users' digital identities are fragmented, scattered across multiple social network platforms, partially defined by these platforms (user tags). In the current model, users do not truly own online accounts. The fact is that they rent accounts from companies and centralized organizations. As a result, users are exposed to the risk of their digital identities being hacked, manipulated, regulated, or lost.
Web3 Identity Should Be Bound to Individuals Rather Than Addresses
Markets based on scarcity, reputation, or authenticity need identities connected to individuals. The term identity has multiple meanings: first, it represents the subject, the concept of a person being different from another person, corresponding to "identity" on a person's ID; second, it represents status, a description of the relationship between one person and another, corresponding to "status" in society. So far, address-based identities focus only on status, particularly contract status, which shows the assets owned by an address. To establish richer social applications, having relational identities that display social relationships between humans is essential; relational status can only occur when people interact with each other.
▲ Contractual Status: The social status a person gains through executing contracts.
▲ Relational Status: The social status a person gains through relationships with others.
While there are many projects in this field, it is still in its infancy, and developers are experimenting with how to integrate these building blocks into the open social stack without sacrificing user experience and the vision of web3 while establishing sustainable business models. With the soulbound tokens proposed by Vitalik, it becomes possible to map real-world relational status onto the chain. Thereafter, on-chain depth and human-based social interactions become possible.
Soulbound tokens (SBTs) are permanent, non-transferable NFTs, meaning they cannot be sent away or taken from a user's private blockchain wallet. Soulbound tokens are digital identity tokens that represent the traits, characteristics, and achievements that constitute a person or entity.










