Frequent visitor to Web3 hackathons? A quick overview of the Web3 email track
Author: WhoKnows DAO
01 Intro
This article is purely the author's ramblings and does not constitute any investment advice. The author does not hold any FT/NFT of the projects mentioned in the text.
In the past two years, we have seen many projects claiming to offer decentralized email services, and it can even be said that Web3 email has almost become a regular feature of Web3 hackathons. As a critic who comments daily, it is hard not to ponder what these products are truly useful for, why so many people are eager to create them, and what can actually be achieved. Thus, this article was born.
Traditional email, as a design prototype for Web3 email, can be considered one of the longest-surviving communication methods on the internet today: the main protocol standards still in use date back to the 1980s, and the prototype of email can even be traced back to 1972. According to Statista, as of 2020, there were over 4 billion email users worldwide, accounting for more than 50% of the global population, and it continues to maintain a 3% annual growth rate.
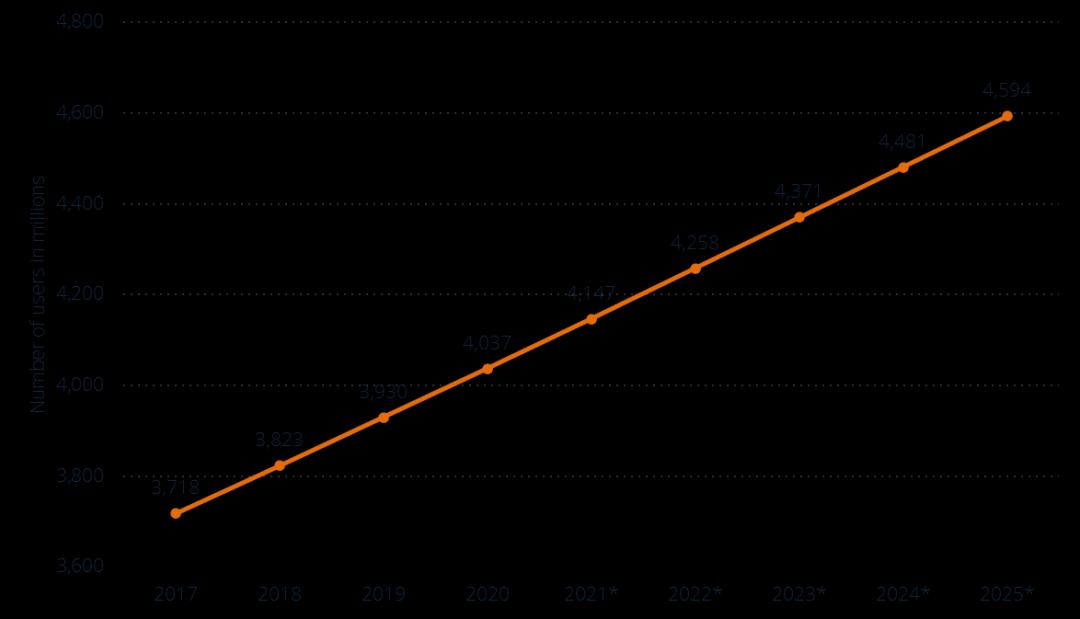
(Data source: Statista)
Thus, the frequent emergence of Web3 email projects is not coincidental. We attempt to broaden the vision: if we can successfully integrate the needs of Web2 and Web3 scenarios, this product could potentially become a key to bridging the gap between Web2 and 3D worlds, devouring the market share of traditional email giants, ushering in a new era of the internet, and becoming one of the leaders of this new era.
We will not discuss whether the so-called vision will be realized here, but rather whether there is an "if." The key lies in whether users in both Web2 and Web3 scenarios will truly be willing to pay for the so-called Web3 email. In this article, we will analyze the necessity of Web3 email from both off-chain and on-chain demand perspectives, as well as the pros and cons of existing products.
02 Off-chain Demand: Convenience, Low Cost, and Identity Verification
As mentioned at the beginning of the article, email as a commercial service aimed at the public began in the 1980s, making it over forty years old. Regarding off-chain demand, we can break it down into two parts: the inherent underlying needs that have remained unchanged for forty years, and the new unmet needs that have emerged alongside the progress of the times and the development of civilization. The performance required to meet the former needs must be maintained, while for the latter, we can consider whether these pain points can be addressed through on-chain email solutions.
Before the invention of email, people who could not or were unwilling to meet typically communicated via telephone, letters, and faxes. In the following two tables, we compare these types of information transmission methods from the perspectives of users and service providers. 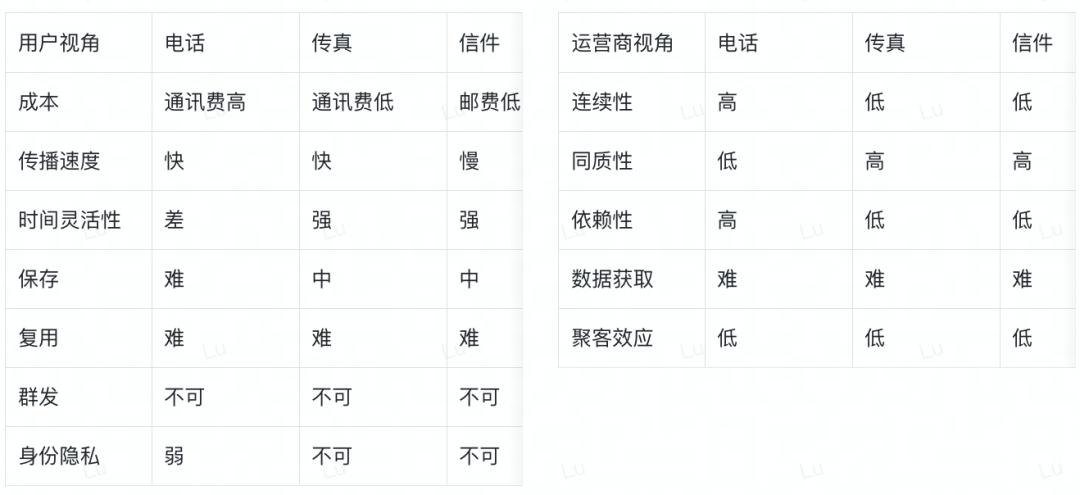
It can be seen that the global popularity of email is mainly due to:
- Zero cost: Telephone and fax require communication fees, letters require postage, while standardized emails can be used for free;
- Speed and flexibility: Letter delivery takes a long time, and phone calls require significant time from both parties, while emails can be sent and received instantly, with flexible viewing times;
- Easy storage and reuse: The content of phone calls, faxes, and letters must be preserved in the form of recordings and paper documents, which require higher storage conditions and are difficult to reuse, while email content exists as data, meaning it does not require physical storage conditions and can be easily searched and reused;
- Support for mass mailing: Emails can be sent to multiple recipients in one operation, a feature that other services do not possess;
- Identity privacy: Emails can serve as ports connecting to different services, allowing users to avoid remembering IDs and passwords for each platform, simply needing to "log in with an email." Additionally, compared to phones, which can also serve as interfaces, emails allow users to register multiple accounts without exposing personal information, providing stronger privacy and better adaptation to internet services.
From the service provider's perspective, several benefits of email are complementary, all pointing towards the reuse of user data, which is precisely why operators are willing to provide standardized email services for free:
- High continuity: Communication via email is usually reciprocal. When a user sends an email from their Gmail address to another user, the recipient will most likely reply to that Gmail address. Compared to phone and fax, email service providers have a lower difficulty in scraping user behavior and social data;
- High homogeneity: Initially, users could only communicate with others using the same service provider. As the demand for cross-provider communication expanded, email services evolved from being unable to communicate across providers to supporting non-standardized cross-provider communication, eventually developing a standardized communication protocol that is still in use today: UUCP for Unix-based inter-computer communication, SMTP for operation over TCP/IP, and protocols POP and IMAP for reading emails. Although there are countless email service providers, standardized email itself is highly homogeneous. A highly homogeneous and free service makes it difficult for users to switch providers based on service quality alone;
- High dependency: The dependency on email services arises from the extremely high switching costs, which stem from the role of email as an identity verification tool. Once a user fills in an email in their personal information or registers for services on certain platforms using that email, switching to a new email means they must find and update all the services they wish to keep in the future. Given the high homogeneity of email services, this usually results in more disadvantages than advantages for users;
- Acquisition of user data: Analyzing user behavior patterns through email sending and receiving records and the behavioral data obtained when using email as a login interface;
- Customer aggregation effect: Using email as an entry point to promote the entire ecosystem to users, such as Google, Yahoo, Tencent ecosystems, etc.;
At this point, we have a general understanding of the advantages of email at its inception compared to similar solutions: convenience, identity verification, and no cost. Next, let's examine how email, as a product of the previous era, survives in the cracks of the rapid proliferation of instant messaging software in today's society.
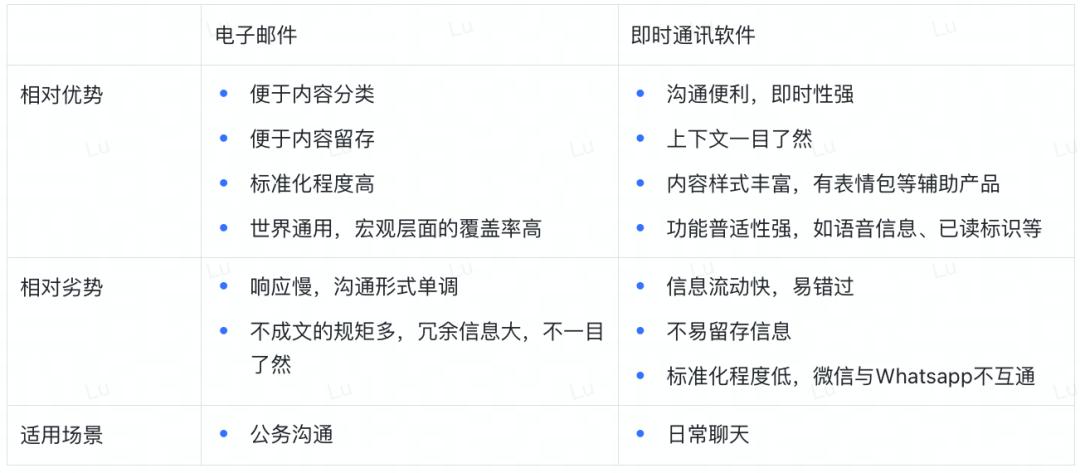
In instant messaging software, information is categorized by chat partners and displayed in chat rooms with each friend, emphasizing "the communication partner"; whereas email separates each message, displaying individual titles, focusing more on "the content of communication." Instant messaging software cares more about the quantity of information, while email emphasizes the quality of information. Thus, the division of labor between email and instant messaging software is now very clear: email is suitable for important and serious matters, while instant messaging software is more appropriate for everyday communication.
At this point, we have recognized the survival strategy of email. So, where are the pain points for users? The product design of email seems very perfect, and in fact, it is quite close to perfection, which is why it has endured for decades. However, there are still three main pain points:
- Information leakage: Email content can be monitored/viewed by service providers. To address this issue, many scholars and institutions have conducted extensive research on quantum communication-based email transmission systems, and there are now clear solutions;
- Information loss: Service providers may stop providing services at any time. As mentioned earlier, operators attempt to exchange free email services for user data and ecosystem promotion. Since users do not need many email accounts, this business model has a clear first-mover advantage, leading over 70% of email service providers to choose to shut down during operations. Additionally, there are numerous cases where accounts are suddenly deactivated without users violating any regulations. Since mainstream email service providers typically retain control over user email accounts, users cannot restore services through email address migration and can only passively accept the situation;
- Spam: The low transmission threshold of email has led to a proliferation of spam. Users need to spend a lot of time receiving and processing spam, easily missing important information, and may even fall victim to phishing emails. Data shows that in 2021, approximately 8.5 billion spam emails were generated daily in China;
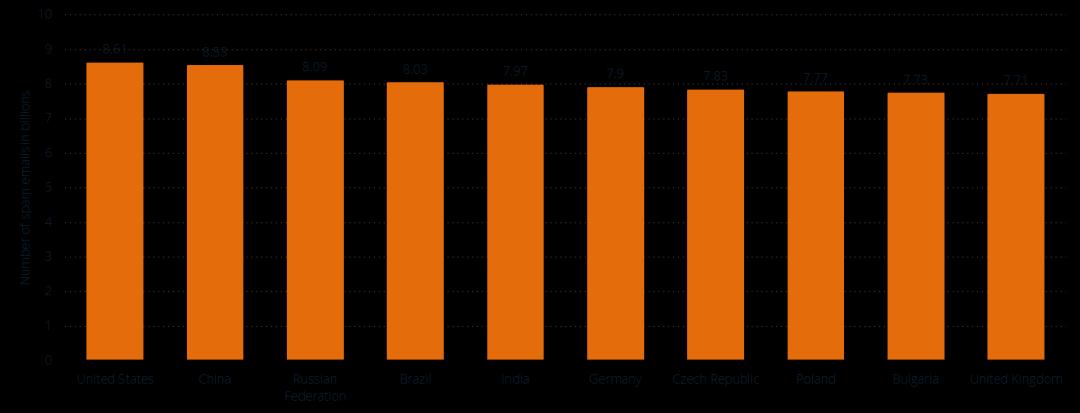
(Data source: Statista)
At this point, we understand the unresolved issues of traditional email services. These issues may not be very significant for C-end users; not many people are constantly worrying about what to do if Google shuts down their email service. In the email service market, the C-end is the majority, so if one hopes to capture market share from traditional email services by solving these issues, it is essentially equivalent to chasing a pipe dream at this stage. So, are there suitable on-chain demands that require email solutions?
03 On-chain Demand: Personal Sovereignty and Encrypted Communication
Based on the Web3 narrative, the roles of email-like products mainly include the following points:
- Cost-free communication: Cost-free communication includes two aspects: first, the platform has no barriers and does not charge fees; second, it enables encrypted conversations between private keys without paying Gas Fees;
- Integration of communication channels: As mentioned earlier, one of the most powerful aspects of email is the interoperability brought by high standardization across different platforms. Therefore, whether Web3 email can achieve standardization while supporting information transmission between private key-private key, private key-email address, and email address-email address is very important;
- Identity proof: Similar to how traditional email can serve as a login interface, Web3 email can also be used as a DID. To ensure personal information is accurate and immutable, the uniqueness, non-transferability, and high combinability of email addresses must be guaranteed;
Asset transfer: Supporting on-chain asset transfer via email; - Targeted dissemination: Filtering email addresses with specific characteristics (such as holding certain assets) through on-chain and off-chain data, and conducting mass email sending.
When considering these demands, we must think about two points:
- How to choose suitable encrypted transmission technology solutions
- How to balance privacy, efficiency, and cost
With this in mind, let's compare several email-like products that have begun to emerge in the current market.
04 Project Comparison
Dmail
Main features:
- NFT email address = Paid
- NFT emails
- Web2+3 email sending and receiving
- Mass mailing
- On-chain asset transfer
- Email address (NFT) used for login

Technical solutions:
- Network: Chose Dfinity ICP (Internet Computer) instead of mainstream public chains/L2. The reasons are that it does not require Gas fees and has confidence in ICP's scalability and interoperability.
- Contract: Written in Rust, based on RFC8555 protocol, establishing its own standard protocol.
- Virtual machine: Uses WASM coding standard, supports multiple languages, enhancing data security and performance while reducing costs.
- Sending: SMTP = Plain text
- Connecting on-chain and off-chain: A new standard based on MIME is under development.
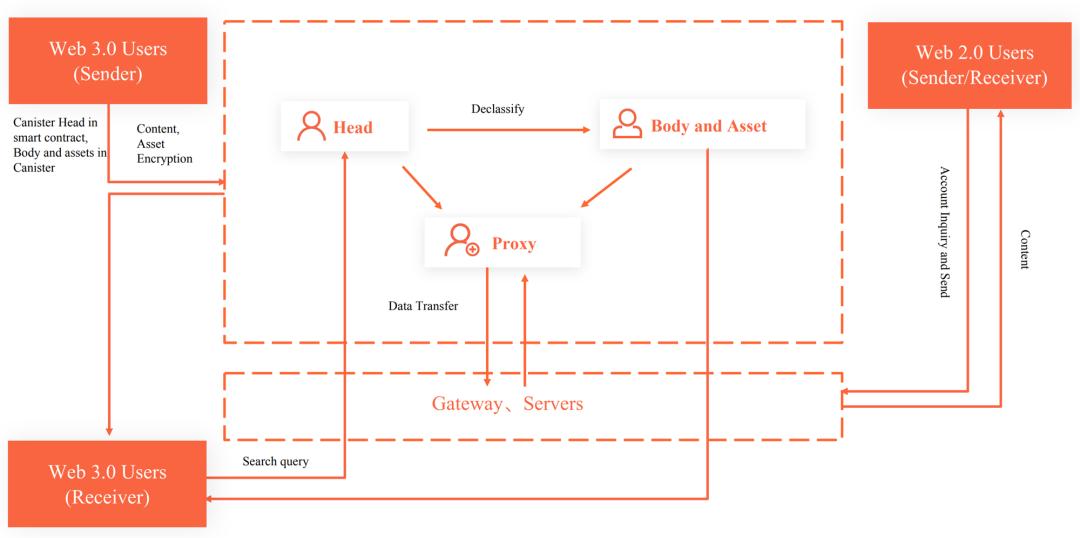
Demand trade-offs:
- Introduced DAO governance model to achieve decentralized management (ensuring service continuity).
- Core technologies of ICP, VRF and BLS, can ensure speed and data security; additionally, Dmail has segmented user information management to enhance scalability, as shown in the diagram:
- Titles are stored on-chain in hash form.
- Content and attachments are split into several parts, stored in dedicated storage jars assigned to each user when obtaining their email account.
- Privacy = Efficiency > Cost
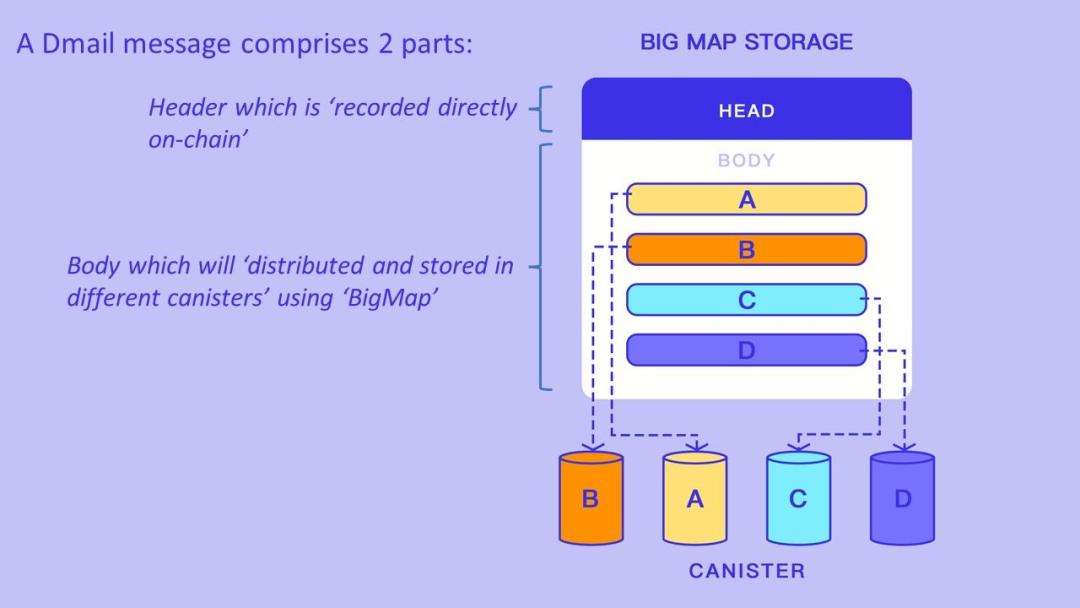
Main pain points:
- Compared to Web3 email competitors, the requirement to purchase an email address NFT results in a higher entry cost.
- The mechanism of allocating storage jars for each user will lead to linear increases in storage costs as the number of users grows.
- NFTs are transferable, meaning email addresses can be transferred.
Mail3
Main features:
- ENS as email address = Free
- Multi-chain interoperability
- Spam filtering
- Web2+3 email sending and receiving
- Mass mailing
- Email address as a foundational social protocol
Technical solutions:
- Network: DCN (Data Communication Network), an evolved version of IPFS, providing distributed data storage and access services, ensuring data availability.
- Sending: SMTP = Plain text
- Connecting on-chain and off-chain: Connects to traditional email systems via LMPS, with on-chain and off-chain users sharing an encryption structure based on OpenPGP and S/MIME.
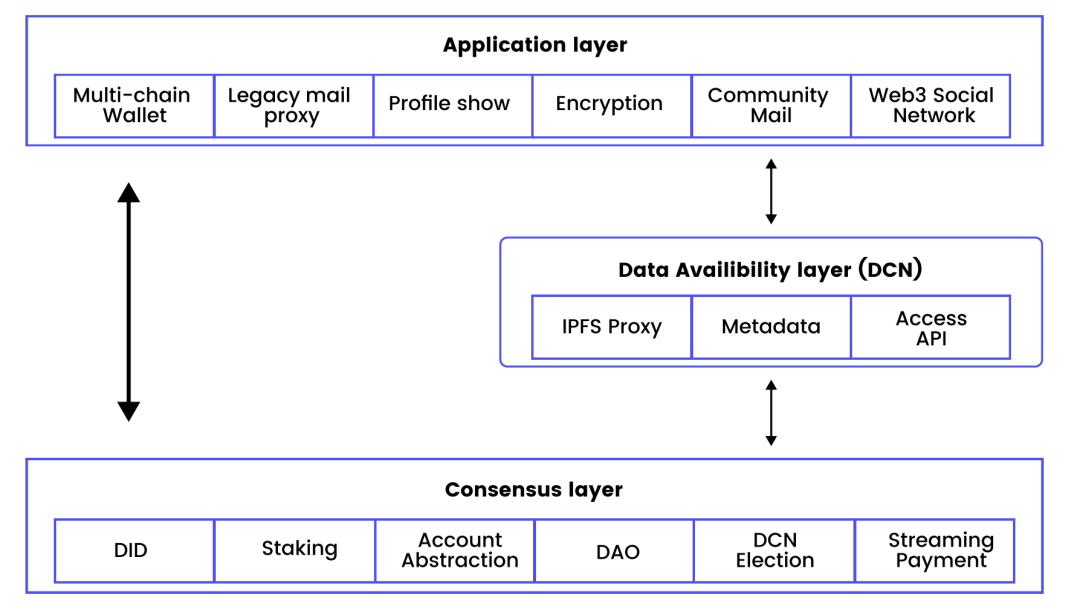
Demand trade-offs:
- Introduced DAO governance model to achieve decentralized management (ensuring service continuity).
- Semi-permanent storage based on IPFS.
- Efficiency = Cost > Privacy
Main pain points:
- Using ENS as an email address effectively turns the email address into a semi-permanent asset; once ENS expires, emails can no longer be received.
Skiff Mail
Main features:
- Supports email address/wallet registration = Free
- End-to-end encryption
- Web2+3 email sending and receiving
- Mass mailing
- Interoperability with Skiff ecosystem
- 2FA
- Document collaboration
Technical solutions:
- Introduces long-term signature public keys and mid-to-long-term encryption public keys, both corresponding to private keys generated using the Curve25519 protocol.
- Uses tweetnacl-js as the encryption library for public key encryption.
- When A sends an email/shares a file with B, a random symmetric key is automatically generated and encrypted using both A and B's encryption public keys.
- IPFS semi-permanent storage.
Demand trade-offs:
- Security > Efficiency = Cost
Main pain points:
- Increasing storage and editing history retention time requires payment.
MetaMail
Main features:
- No barriers to use = Free
- ENS can serve as an email address
- Encrypted transmission of email content
- Web2+3 email sending and receiving
- Mass mailing
Technical solutions:
- Sending: SMTP + private key encryption/public key end-to-end encryption (when the recipient is a MetaMail address).
Demand trade-offs:
- Administrators retain the private keys used for email encryption.
- Cost > Efficiency > Security
Main pain points:
- Does not support attachment encryption, leading to security issues.
- Platform can view emails, leading to security issues.
- High signature frequency, inconvenient.
EtherMail
Main features:
- Login with wallet = Free
- Rich ToB features, with a self-updating email list based on on-chain data and group sending system.
- Custom spam filtering = Watch ads to earn, subscribe to earn.
Technical solutions:
- Uses the Thor protocol, allowing users to choose whether to authorize the platform to access their private keys or not.
- Stores keys on the blockchain to ensure their security.
Demand trade-offs:
- Introduced DAO governance model to achieve decentralized management (ensuring service continuity).
- Security = Efficiency = Cost
Main pain points:
- Webpage response is very slow, with each action taking several minutes to process.
Project Comparison Summary
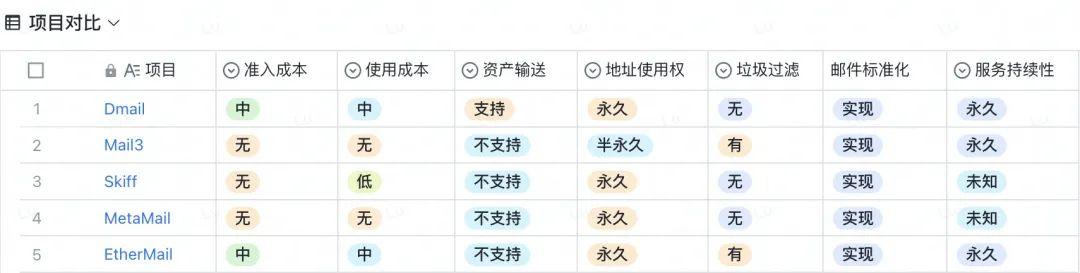
Each project has its strengths and weaknesses. Currently, the fastest progress and most aligned concepts with the Web3 narrative are Dmail and Mail3. It is not difficult to see that as a highly interactive social protocol, Web3 email is highly compatible with the DID concept, making it very suitable to serve as a bridge linking different protocols, just as traditional email serves as a login interface in the conventional internet. As a DID, it must first possess non-transferability and high functional diversity. We look forward to future projects introducing an SBT system based on current projects to ensure email addresses are non-transferable; at the same time, integrating the asset transfer system with wallets to create a social protocol that retains the basic functions of traditional email but is fully adapted to the Web3 context.
References
https://dmail.ai/Dmail_litepaper.pdf
https://www.dfinitycommunity.com/dmail-network-decentralized-email-for-the-web-3-generation/
https://mail3.me/mail3-litepaper.pdf
https://skiff-org.github.io/whitepaper/Skiff_Whitepaper_2022.pdf
https://mirror.xyz/suneal.eth/WbTmDLjY-Q9q1KMf15_nzse7M2Q84jCVq0vWNFefBtc











