Slow Fog: Analysis of the BonqDAO Hacking Incident
ChainCatcher message, regarding the hacker attack on the BonqDAO project this morning, the SlowMist security team analysis:
The oracle used by the BonqDAO platform is based on the ratio of TellorFlex self-reported prices to Chainlink prices. A major limitation for updating TellorFlex prices is that price reporters must first stake 10 TRB before they can submit price updates. In TellorFlex, the amount of TRB required for staking can be periodically updated based on the collateral price using the updateStakeAmount function.
Since the TRB staking amount for the TellorFlex oracle contract was initially set to 10 and was not updated through the updateStakeAmount function afterwards, the attacker only needed to stake 10 TRB to become a price reporter and could modify the price of the WALBT token in the oracle by calling the submitValue function.
After modifying the price, the attacker called the createTrove function of the Bonq contract to create a trove for the attack contract. The trove contract mainly records the user's collateral status, debt status, borrows from the market, liquidation, etc.
Following this, the attacker performed a collateral operation in the protocol and then called the borrow function to take out a loan. Due to the manipulated increase in the price of the WALBT token, the protocol minted a large amount of BEUR tokens for the attacker.
In another attack transaction, the attacker used the aforementioned method to modify the price of WALBT and then liquidated other users in debt in the market to obtain a large amount of WALBT tokens.
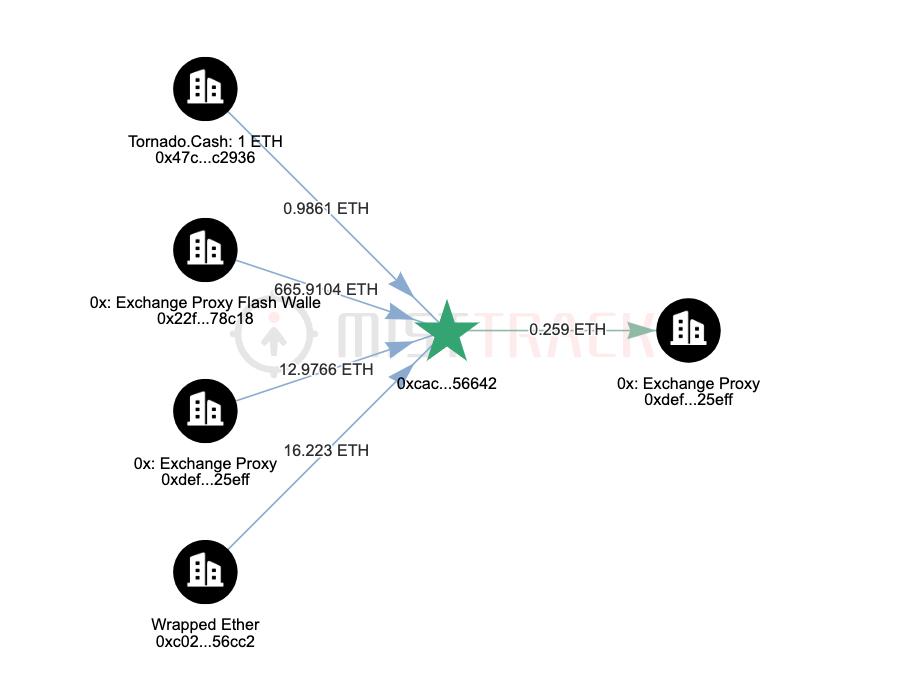
According to SlowMist's MistTrack analysis, 113 million WALBT have been burned on the Polygon chain and ALBT has been withdrawn from the ETH chain, with some ALBT exchanged for ETH through 0x; part of the BEUR has been exchanged by the attacker for USDC via Uniswap and then cross-chained to the ETH chain through Multichain and exchanged for DAI.
The SlowMist security team analysis believes that the root cause of this attack lies in the fact that the attacker exploited the cost of collateral required for oracle pricing, which is far lower than the profits gained from the attack, thereby manipulating the market through maliciously submitting incorrect prices and liquidating other users. As of now, 946,000 ALBT have been exchanged for 695 ETH, and 558,000 BEUR have been exchanged for 534,000 DAI. The hacker is still continuously exchanging ALBT for ETH, and no funds have been found to be transferred to exchanges or other platforms. MistTrack will continue to monitor the hacker's movements and follow up on blacklisting.