Why is the future of cryptocurrency evolving towards asset custody?
Author: BART HILLERICH
Translator: Huo Huo / Baihua Blockchain
The evolution of crypto asset custody is an urgent issue that requires stringent audit controls and new-era key management to rebuild trust.
After the crypto market crash in 2022, concerns about counterparty risk have become a hot topic in crypto risk management discussions and will be one of the main driving forces shaping the future of custody in 2023 and beyond.
As this future becomes a reality, the regulatory framework surrounding custody is becoming clearer, and anything deemed operationally unwise or inappropriate will face strict scrutiny. The type of crypto approach previously adopted by FTX—storing assets in a single-key wallet on cloud servers, lacking a cybersecurity team, and failing to establish systematic key management—will no longer be accepted by clients and regulators.
Mick Horgan, Head of Custody at Bullish, said, "I remember browsing the FTX website, trying to figure out their custody, trying to understand their underlying custody system. I had read about their quick withdrawal times for large transactions while seemingly keeping most assets securely custodied. How did they do that? I couldn't figure it out. Of course, the answer is that FTX's operational model was completely opposite to Bullish's."
As the adoption of digital assets continues to grow, the failures of 2022 have become a thing of the past, and how third-party digital asset custodians ensure the safety of their funds will receive unprecedented attention, both from crypto participants and from regulators attempting to establish new, safer standards for the crypto industry.
The key to this evolution is the widespread implementation of a multi-layer custody system based on two fundamental pillars: key management and stringent audit controls. Doing so will raise the minimum acceptable security level for asset custodians, rebuild and enhance institutional trust, and prevent new black swan events, such as sudden trading platform collapses, to better facilitate the growth of crypto.
1. Keys are Paramount
It can be said that in crypto industry participation, nothing is more important than the secure custody of assets. So why are third-party custodians not required to meet higher key management standards? In the case of FTX, when the company finally implemented multi-signature wallets, they stored all three keys in the same online location, which contradicted the purpose of multi-signature wallets.
"This is akin to buying a secure high-end vault, putting all your valuables inside, and then walking away with the vault door wide open," said Mick Horgan, Head of Custody at Bullish.
To move forward with a wiser and stronger industry, prioritizing key management within a multi-layer custody system is a clear benchmark for third-party custodians. Here are the key features that Bullish recommends all custodians should implement.
2. Decentralized Private Key Storage
To ensure there is no single point of failure, private keys must never be stored in one location. Instead, they should be isolated from each other and stored offline.
In a well-designed multi-layer custody system, the custodian's key distribution will use a combination of cold wallets, warm wallets, and hot wallets to facilitate transfers while minimizing the risk of loss or theft. Following best practices, most assets will be securely stored in offline key-protected wallets.
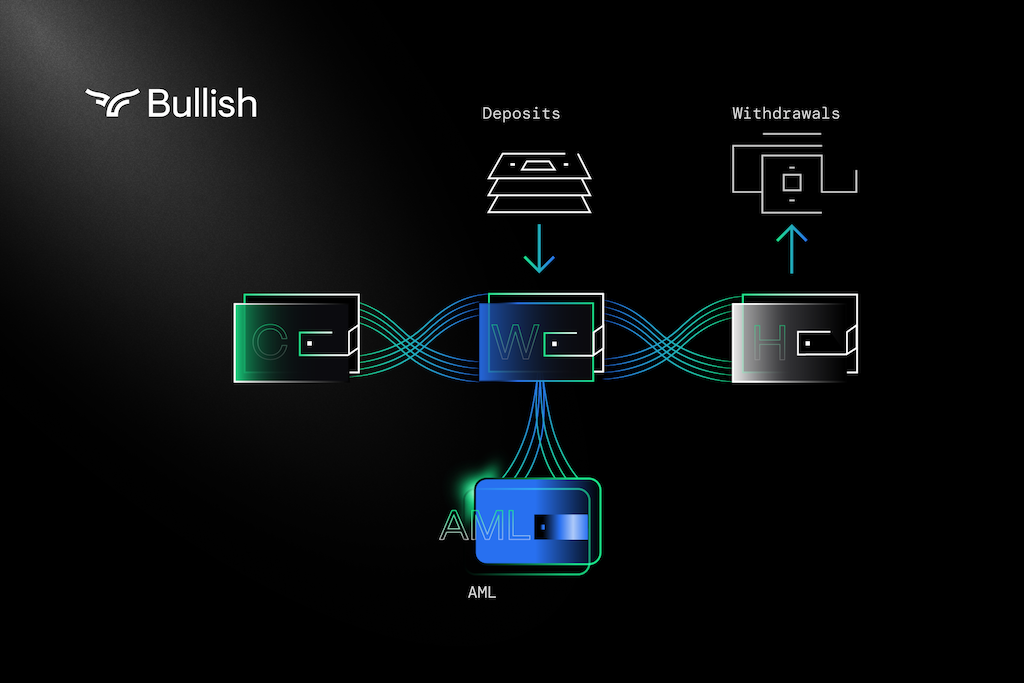
3. Ensuring Safeguards in Hardware, Software, and Operations
In terms of key management, establishing safeguards at every level of the custody system is crucial. Once established, they will provide the necessary confidence for institutions and individual crypto participants to engage in third-party custody options. Here are some best practices that should be implemented:
1) Hardware Safeguards
Isolate and store all offline private keys on secure storage devices.
Store online keys in secure modules on protected cloud servers.
Ensure effective use of cold storage by keeping the majority of held digital assets in cold wallets offline.
2) Software Safeguards
All custody software components and operating systems should be cryptographically signed.
The signing process should be distributed among independent participants via multi-signature wallets to enhance collusion prevention.
Utilize blockchain-based oracles to verify the provenance of custody operations and prevent man-in-the-middle attacks.
3) Operational Safeguards
Protocols should specify which wallets interact, what keys are needed to sign transactions, and the limits on transaction size and speed.
Asset custodians can implement disaster recovery systems to back up keys, ensuring that not all keys are lost in the worst-case scenario.
Key backups can be stored in remote locations in secure facilities around the world to ensure maximum security.
4. World-Class Controls, or Nothing
Whether institutional or individual, participants have begun exploring the crypto space and face a question: "If I lose my keys, do I lose everything?"
This is a major bottleneck moment in today's crypto industry, where individuals either decide to rely on themselves or hesitate due to the fear of losing keys and their consequences. Most institutions do not want to manage their keys, but they are very concerned about how the custodians they choose manage these keys on their behalf; sufficient trust is crucial to their success in entering the crypto space.
"The failure of FTX underscores the importance of custody. Custody, simply put, is about the security of keys, and it can only be truly effective when there are strong internal controls, thorough record-keeping procedures, and an obsession with the safety of client assets," stated Mick Horgan, Head of Custody at Bullish.
Establishing strict, audited control measures is vital for helping institutions navigate challenges by instilling confidence in third-party custodians. These controls can take various forms, each an essential component of building a comprehensive security system.
1) Internal Controls
Internal controls help protect client assets; if implemented correctly, they should be able to detect, prevent, and limit potential issues with client wallets. Here are the controls Bullish has implemented internally, setting a clear example for other companies:
Separation of Duties - Responsibilities such as key generation, storage, and transaction approval should be separated to reduce the risk of fraud and theft arising from collusion.
Wallet Recovery - Companies should implement controls to securely recover wallets at any time to prevent any loss of key access.
Private Key Management - Most assets should be stored in a multi-signature cold storage wallet in an offline state to reduce the risk of online attacks.
Risk Assessment and Management - Companies should continuously conduct security assessments and key scenario analyses.
Asset Segregation - Client funds must be kept separate from company assets to ensure that there is no mixing on any account or blockchain address.
Monitoring - Real-time monitoring of wallets/transactions and reconciliation of all wallets and accounts should be implemented. Ideally, a dedicated cybersecurity team will lead this control.
Access Control - Over 80% of security vulnerabilities are related to passwords, so in an industry plagued by cyberattacks and fraud, passwords are no longer sufficient. Strict access controls and multi-factor authentication should be implemented for access to all privileged systems.
Employees - The cybersecurity team should implement comprehensive security training programs to ensure every level of the company is protected by contributors.
All internal controls and security policies should be regularly reviewed and audited by external auditors, which is the foundation of external controls.
2) External Controls
To supplement internal controls and better meet institutional needs, third-party crypto custodians need to elevate audits to at least meet traditional finance (TradFi) standards. To this end, each custodian needs to implement regular independent audits conducted by qualified auditors (e.g., the Big Four accounting firms).
These audits should assess the custodian's internal controls and overall security, ensure client assets are segregated from custodian assets, and analyze the custodian's solvency through completion of reserve proof audits.
Planning for a Secure Future in Crypto To ensure the crypto industry continues to move toward global adoption, past shortcomings must remain unchanged, especially in crypto custody. If there is one lesson to be learned from FTX, it is that crypto cannot fully rely on governments, auditors, and regulators to protect its participants. Instead, every participating institution and individual needs to do their part to hold asset custodians accountable. If everyone plays their role, the industry will elevate to a new standard, becoming a leader in transparency, risk management, and security in the global financial landscape.










