Decrypting the "Everest Project": A treasure hunt to crack 7,002 Bitcoin wallets worth $235 million
Written by: Andy Greenberg, Wired
Translated by: Felix, PANews
In late September this year, a hacker who claimed to be named Tom Smith sent Andy Greenberg a nonsensical text message: "query voltage recurrence."
But these three words proved to be an extraordinary feat and potentially very valuable. Just days earlier, Andy Greenberg had randomly generated these words and set them as the password for a certain model of encrypted USB drive (IronKey S200), which he then handed over to Tom Smith and his startup Unphered based in Seattle.

Employees at Unciphered's Seattle lab
Smith told Andy Greenberg that cracking the password might take a few days. In fact, guessing the password should be impossible, because the design of IronKeys is such that after 10 incorrect password attempts, the contents are permanently deleted. However, the hackers at Unphered developed a password-cracking technique that allows for unlimited attempts (they refused to describe this technique in detail to Andy Greenberg or anyone outside the company). Therefore, the morning after Andy Greenberg's wallet arrived at the Unphered lab, he was astonished to find that the three-word password had already been sent. Smith informed Andy Greenberg that, with the help of a high-performance computer, the process had only taken 200 trillion attempts.
Smith's demonstration was not a simple hacking technique; it was something he and his team had spent nearly eight months developing to crack this specific and decade-old IronKey model. The reason for the development was also very special: in a Swiss bank vault 5,000 miles east of the Seattle lab, there is a wallet containing 7,002 bitcoins, which is also an IronKey model hard drive, valued at nearly $235 million at current exchange rates.
The owner of this wallet is Swiss crypto entrepreneur Stefan Thomas, who lives in San Francisco. Due to Thomas losing the password, the nine-digit fortune contained within is inaccessible. According to Thomas in an interview, he has guessed incorrectly eight times, leaving only two attempts remaining. If he fails, the IronKey will delete the keys stored on it, making his bitcoins forever inaccessible. Therefore, for years, hackers at Unphered and many in the crypto community have been keeping an eye on Thomas.
 Screenshots from Unciphered's lab showing a microscopic image of the IronKey controller chip layout (left) and a CT scan of the drive
Screenshots from Unciphered's lab showing a microscopic image of the IronKey controller chip layout (left) and a CT scan of the drive
After months of effort, the hackers at Unphered stated they were ready to use their secret cracking technique to unlock this wallet. "We hesitated to contact him until we had a complete, provable, and reliable method," Smith said. Due to the sensitivity of using secret hacking techniques and the large amount of cryptocurrency involved, Smith requested not to disclose his real name in an interview with Wired.
Capable of Wallet Decryption but Beaten to the Punch
Earlier this month, shortly after proving their decryption capabilities to Andy Greenberg, Unphered contacted Thomas through a mutual friend who could vouch for Unphered's IronKey unlocking abilities and offer assistance. However, Thomas politely declined, and they didn't even discuss Unphered's commission over the phone.
In response, Thomas explained that he had already reached a "cooperation agreement" with two other excellent teams a year ago. To prevent competition between the two teams, he proposed that if one party could unlock the hard drive, they could share a portion of the proceeds. Even a year later, he still promised to give these teams more time to solve the problem before inviting others to decrypt it. Although neither of the two teams has shown any signs of progress, Unphered has already proven its decryption capabilities.
This has put Unphered in an awkward position: Unphered possesses what may be one of the most valuable "unlocking" tools in the crypto world, but there is no lock to open. Unphered's operations director, Nick Fedoroff, stated, "We cracked IronKey, but now we have to crack Stefan Thomas. It turns out that's the hardest part."
Thomas confirmed in an email to Wired that he rejected Unphered's offer to decrypt for him. Thomas wrote: "I have already worked with different experts, so I can't just casually collaborate with others. If the current team believes that collaborating with others is the best option, they may decide to subcontract the decryption work, but for now, we must wait."
The "Everest Project" Initiated by Thomas
In past interviews, Thomas revealed that the 7,002 bitcoins were received when he filmed a video titled "What is Bitcoin?" in early 2011, when a single bitcoin was worth less than $1. However, later that year, Thomas accidentally deleted two backup copies of the wallet and lost the password for the third copy stored on IronKey, resulting in a loss of nearly $140,000 in tokens. "I spent a week trying to recover it, and it was very painful."
In the 12 years since then, the value of the bitcoins in Thomas's wallet has at one point soared to nearly $500 million. In January 2021, as bitcoin approached its peak price, Thomas described the anxiety caused by the long-lost password in an interview with The New York Times. "I would lie in bed thinking about it, and then I would come up with new strategies on the computer, but none of them worked, and I would feel hopeless."
Around the same time in 2021, a group of cryptographers and white-hat hackers founded Unphered, aiming to unlock wallets for cryptocurrency holders like Thomas. When Unphered was officially established, cryptocurrency tracking company Chainalysis estimated that the total value of wallets with lost passwords was $140 billion. Unphered stated that since then, the company has successfully helped clients unlock wallets worth "millions of dollars"—usually by discovering vulnerabilities or software flaws in crypto wallets—though the amounts are far less than Thomas's IronKey wallet.
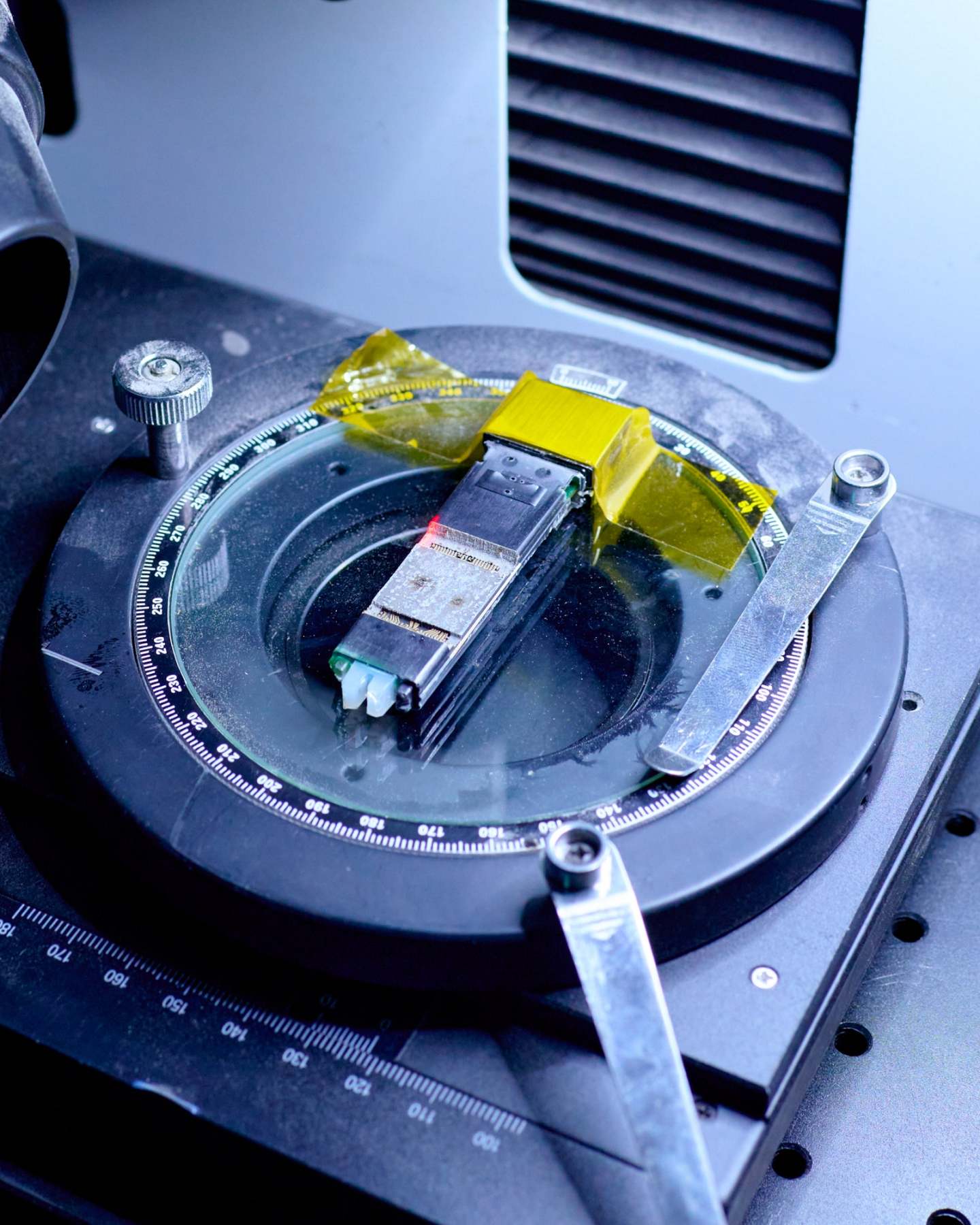
Unciphered laser-cut IronKey that has been deconstructed
It wasn't until early 2023 that Unciphered began looking for potential ways to unlock Thomas's IronKey. Smith said they quickly discovered that the manufacturer of IronKey (sold to storage hardware company iMation in 2011) had left them some potential opportunities.
Even a decade-old IronKey is a daunting target for hackers. The development of this USB drive was partially funded by the U.S. Department of Homeland Security and has passed FIPS-140-2 Level 3 certification, meaning it has tamper-resistant capabilities and encryption technology secure enough for classified information used by military and intelligence agencies. However, Unphered still found signs of some security vulnerabilities in the wallet, but Thomas's wallet remained uncracked, so Unphered decided to tackle the challenge, "If you're going to climb Mount Everest, this is it." Ultimately, Unphered became a team of about 10 employees and external consultants, some of whom have backgrounds working with the National Security Agency (NSA) or other Level 3 government agencies, and referred to the decryption of the IronKey wallet as the "Everest Project."
Unphered's first step was to filter and determine the exact model of Thomas's IronKey based on time. To do this, they purchased all IronKey models that are over a decade old, accumulating hundreds in their lab.
To fully reverse engineer the device, Unphered scanned an IronKey with a CT scanner and began deconstruction. Using precise laser cutting tools, Unphered cut out the Atmel chip, which is the "secure area" of the IronKey used to store passwords. They then soaked the chip in nitric acid to remove the tamper-proof epoxy layer and polished the chip with a silica abrasive solution and rotating felt pads. For every micron of material removed from the chip's surface, they photographed each layer using an optical microscope or scanning electron microscope, continuously repeating this process until they could establish a complete 3D model of the processor.
Since the read-only memory (ROM) of the chip is built into its physical wiring, it enhances efficiency. Thus, Unphered's visualization model kept them ahead in cracking most of the logic of the IronKey encryption algorithm. But the team didn't stop there; they installed a tenth-of-a-millimeter wire at the connections of the secure element to "eavesdrop" on the communications in and out of that element. They even found engineers who had been involved in the development of the Atmel chip and another microcontroller for IronKey to inquire about hardware details. "It felt like a treasure hunt. You follow a faded, coffee-stained map, knowing there's a pot of gold at the end of the rainbow, but you don't know where the rainbow will take you," described Unciphered's operations director Nick Fedoroff.
The cracking process peaked in July of this year. At that time, the Unphered team gathered at an Airbnb in San Francisco, and a team member decrypted the contents of the IronKey for the first time.
However, Unphered did not disclose its complete research process, nor will it reveal any details about how it ultimately cracked IronKey and defeated the "counter" technology that limits password attempts. The company stated that the vulnerabilities they discovered might still be too dangerous to disclose. Because the models of IronKeys they cracked are too old to be patched with software updates, and some may still store classified information. If this information were to leak in some way, the impact on national security would be far greater than that of a crypto wallet.
Nevertheless, Unphered also revealed that their final method did not require any invasive or destructive strategies, and they had not caused any damage in over a thousand unlocks of the 2011 IronKeys.
Skeptical of Thomas's Collaborating Teams, Plans to Release Open Letter to Persuade
However, these achievements did not convince Thomas. Unphered's hackers stated that they learned from the intermediary representing them that Thomas had already contacted two other parties in the field of crypto and hardware hacking: the cybersecurity forensics and investigation company Naxo and independent security researcher Chris Tarnovsky.
Naxo declined to comment. However, renowned chip reverse engineer Chris Tarnovsky confirmed to Wired that he had a phone "meeting" with Thomas last May, during which Thomas told him that if he could successfully unlock the IronKeys, he would "generously" reward him, but did not specify any fees or commissions. Since then, he has done very little work on this project, as he has basically been waiting for Thomas to pay his initial research fees monthly. "I want Thomas to pay some money upfront; after all, I have a lot of work to do, and I have to worry about my mortgage and bills."
But Chris Tarnovsky also stated that he has not heard from Thomas since their first call, "No results, which is strange."
 Unciphered operations director Nick Fedoroff
Unciphered operations director Nick Fedoroff
The Unciphered team remains skeptical about Naxo's progress. They believe that only a few hardware hackers have the capability to perform the reverse engineering required to crack IronKey, and it seems that no one is collaborating with Naxo. Regarding Thomas's suggestion to subcontract the project to Naxo or other teams, Fedoroff stated, "It's not out of the question, but it doesn't make sense when Unciphered can crack IronKey on its own. From what we know, this option benefits no one."
Meanwhile, Thomas seems to exhibit an unusual lack of urgency regarding the $235 million unlocking issue. When asked for reasons, Thomas only gave vague hints, "When you're dealing with that much money, everything takes a long time." He stated in a Thinking Crypto podcast this summer: "Contracts need to be signed with collaborators, and they must be clear, because if anything goes wrong, hundreds of millions will be at stake."
To expedite the process, Unphered plans to release an open letter and a video addressed to Thomas in the coming days, aiming to persuade him to cooperate. However, Fedoroff also admitted that Thomas may not actually care about the money. An article published by The New York Times in 2021 stated that due to other crypto ventures, Thomas already possesses "wealth he doesn't know how to handle."
Fedoroff also pointed out that it is impossible to know exactly what is hidden in Thomas's IronKey. Perhaps the password for these 7,002 bitcoins is hidden elsewhere or has completely vanished.
While Unphered remains hopeful, the team is also prepared to move on if Thomas does not cooperate. After all, there are other wallets waiting for the company to crack. As for whether and how to unlock this particular USB drive, it will ultimately depend on its owner. Fedoroff said, "It's very frustrating; people are unpredictable beings, and dealing with them is always the most complicated, but the code doesn't change, and the circuits don't either, unless you make them change."










