What can decentralized digital identity (DID) bring to DeFi in creating trust in blockchain?
Author: Karim Halabi, Messari
Compiled by: 8btc
The mutual recognition of identity is crucial for almost all human interactions. It signifies authenticity and is a prerequisite for trust. Most interactions that occur within a specific community are based on the participants' ability to identify themselves to some extent.
In fact, early human communes relied on members' ability to recognize each other to function. The change today is that we live in groups that exceed Dunbar's number (the 150 rule: the number of stable social relationships that human intelligence allows is about 150), which means we cannot possibly recognize and connect with everyone we live with.
The semi-fixed identity recognition method is one of the key reasons humans have become the only vertebrates capable of living in larger societies.
The rise of digital networks that are not geographically constrained has led to the emergence of new types of identifiers. Today, the most commonly used identifiers for most people are email addresses and passwords, which allow us to create accounts on websites and applications to establish relationships. This creates our digital identity that we use to interact in the virtual world.
The problem with our digital identity and the accompanying data is that they are organized and aggregated to create a fairly accurate digital representation of ourselves. This in itself is not a problem; the issue lies in how trusted intermediaries manage this data, often with little transparency. Unfortunately, events like the Cambridge Analytica scandal indicate that this data can sometimes be used for nefarious purposes, undermining our trust in these intermediaries.
This means that without needing to trust any potentially negligent/malicious third parties using our Personally Identifiable Information (PII), our identity could be managed by ourselves. This enables us to manage and leverage our reputation and identity to obtain services in a trustless manner, such as obtaining under-collateralized loans from MakerDAO or Compound.
What is Decentralized Identity (DID)?
On-chain identity is the attachment of a blockchain public key to a real-world identity. This can belong to a person, an object, or even something more abstract, such as a data model.
When completed on a public, decentralized blockchain, this grants the owner custodianship and complete sovereignty over their digital identity and how it is used, just as having your private key allows you to fully own your cryptocurrency. This is referred to as Decentralized Identity (DID).
DIDs can also contain different personal information and identifiers stored in the same location, just as a wallet can hold different standards of cryptocurrency tokens.
Individuals can have a digital identity that contains all this information and is managed independently, rather than having multiple digital identities managed by various centralized providers (for example, a driver's license managed by the DMV, a Google account managed by Google, a bank account managed by a bank, etc.). Since there is no need to trust a third party to safeguard it, these identities cannot be used for any purpose without the explicit consent of the owner.
Having a decentralized on-chain identity has many implications, including:
- Validating information and identity
- Preventing fraud and identity theft
- Establishing on-chain reputation (i.e., credit, events, actions)
The Importance of DID
DID has the potential to selectively authorize third-party services (online accounts, financial services, etc.) to access information. For example, when integrating a Google Sheets plugin, the following permissions are required to add the application.
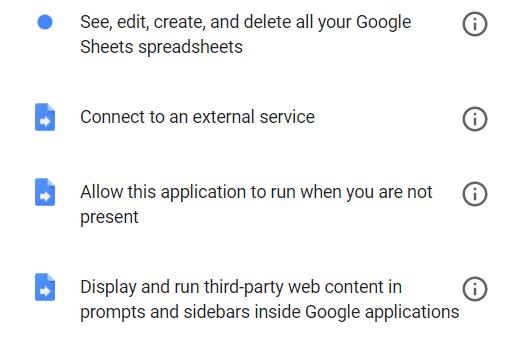
Source: Plugin Installation
Its function is merely to connect and import data from the API into the spreadsheet. Granting Google's API the ability to edit or delete all spreadsheets and run when they do not exist seems unnecessary, even intrusive. Not all of these permissions are relevant, but they are all required, and we must control our "digital self" and property to use the add-on.
As mentioned earlier, having a sovereign, decentralized identity allows the owner to freely share only what is needed.
This is because we can have multiple independent digital identities at the appropriate times; there is no need to share a bunch of aggregated identifiers that may contain strictly unrelated information that we may not want to share. This enables individuals to limit and control what information can be known about them in interactions with society, institutions, and government services (for example, you can log into a social media account while retaining complete ownership of your PII).
Do not confuse DID with Single Sign-On (SSO), which allows entities to log into different websites and applications using a set of credentials. These SSO solutions include OAuth, but Google and Facebook are also pushing these standards.
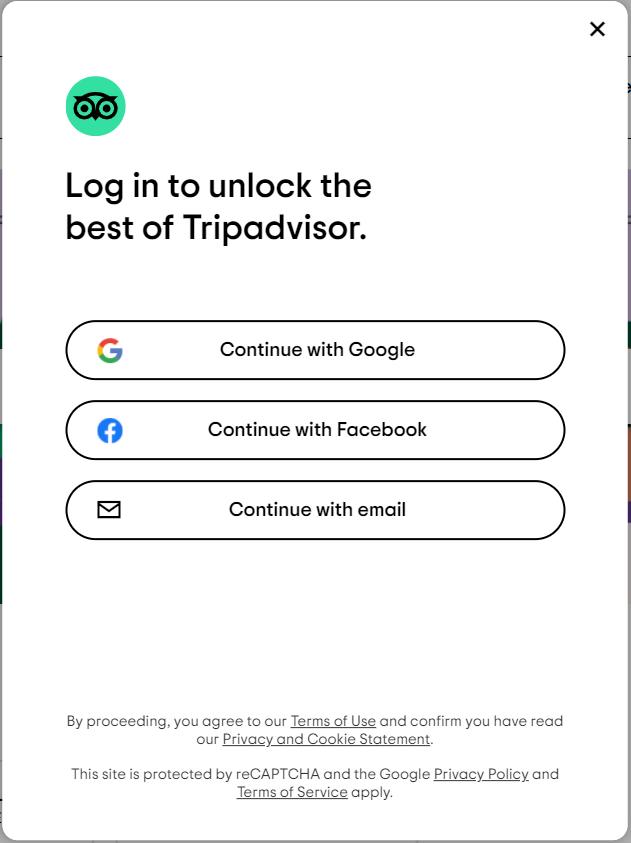
Source: Tripadvisor Login
The fundamental difference between SSO and decentralized identity is that third parties still retain custody of the identity, and it is not truly sovereign.
Using DID solutions means that information about important documents/identities can be stored without actually holding the documents/identities themselves. As mentioned earlier, the significance of DID to identity is akin to the significance of cryptocurrencies like Bitcoin to money: complete ownership.
An Identity Solution for Everyone?
One billion people worldwide cannot claim ownership of their identity, preventing them from owning property, voting, applying for social security, or finding formally protected work.
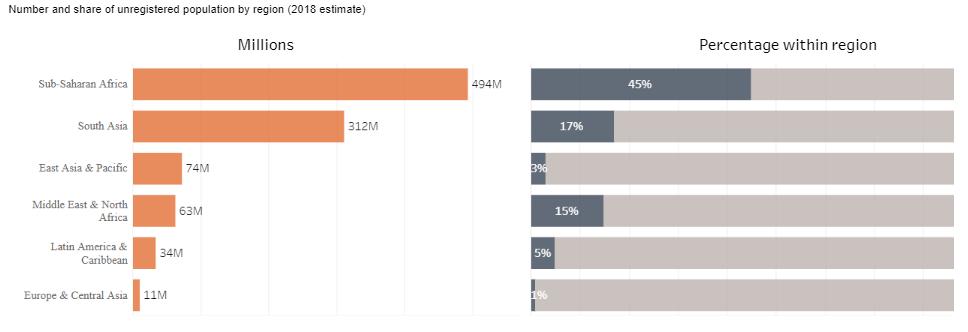
Source: World Bank
Due to a lack of official services and infrastructure for identity registration, hundreds of millions of individuals cannot obtain this ownership. Many people cannot even obtain birth certificates and registrations. For those who have identification, their information is stored in central repositories, which can sometimes be lost in natural and political disasters.
DID enables those without legal identity to control their identity and represent themselves in a verifiable manner. Additionally, facial recognition or iris scanning can be used alongside public and private keys to create and claim an undeniable decentralized identity that is not controlled by any third party.
Although official agencies in the off-chain world may not recognize this, the immutable history on-chain can create reputations, allowing owners to participate in the crypto economy and granting access only to those with specific histories.
Using a form of identification allows us to participate in formal and informal networks, as well as social structures like markets. Using a decentralized form of identification enables us to do this without sacrificing a certain degree of privacy or security.
The Future of Digital Identity
Currently, there are several different DID or on-chain identity solutions that operate in various ways and are optimized for different use cases.
Civic
An app-based solution where users can store different identifiers and credentials. It provides entities with a simple way to manage different identities and permissions on how they are used. Civic stores information on the Ethereum blockchain to avoid the risks of being stored in a central database.
The roadmap outlines the "Civic Compliance" released in Q3 2021, aimed at improving user compliance with on-chain identity and DeFi protocols.

Source: Civic Compliance
ION
Identity Overlay Network (ION) is developed by Microsoft and built on the Bitcoin blockchain using the Sidetree protocol. ION has been piloted in the UK National Health Service for healthcare professionals to effectively share professional credentials, reducing the time spent on verification.
SelfKey
SelfKey enables users to create self-sovereign identities on the blockchain. The project aims to create a native marketplace where individual DIDs can be used to directly access services such as opening bank accounts, setting up cryptocurrency exchange accounts compliant with Know Your Customer (KYC) rules, or even applying for passports.
Source: SelfKey
Litentry
Litentry acts as an identity aggregator, allowing users to manage their cross-chain identities. Thus, when users interact with DApps on another chain, they can use quantifiable past activities (reputation) from different chains as proof.
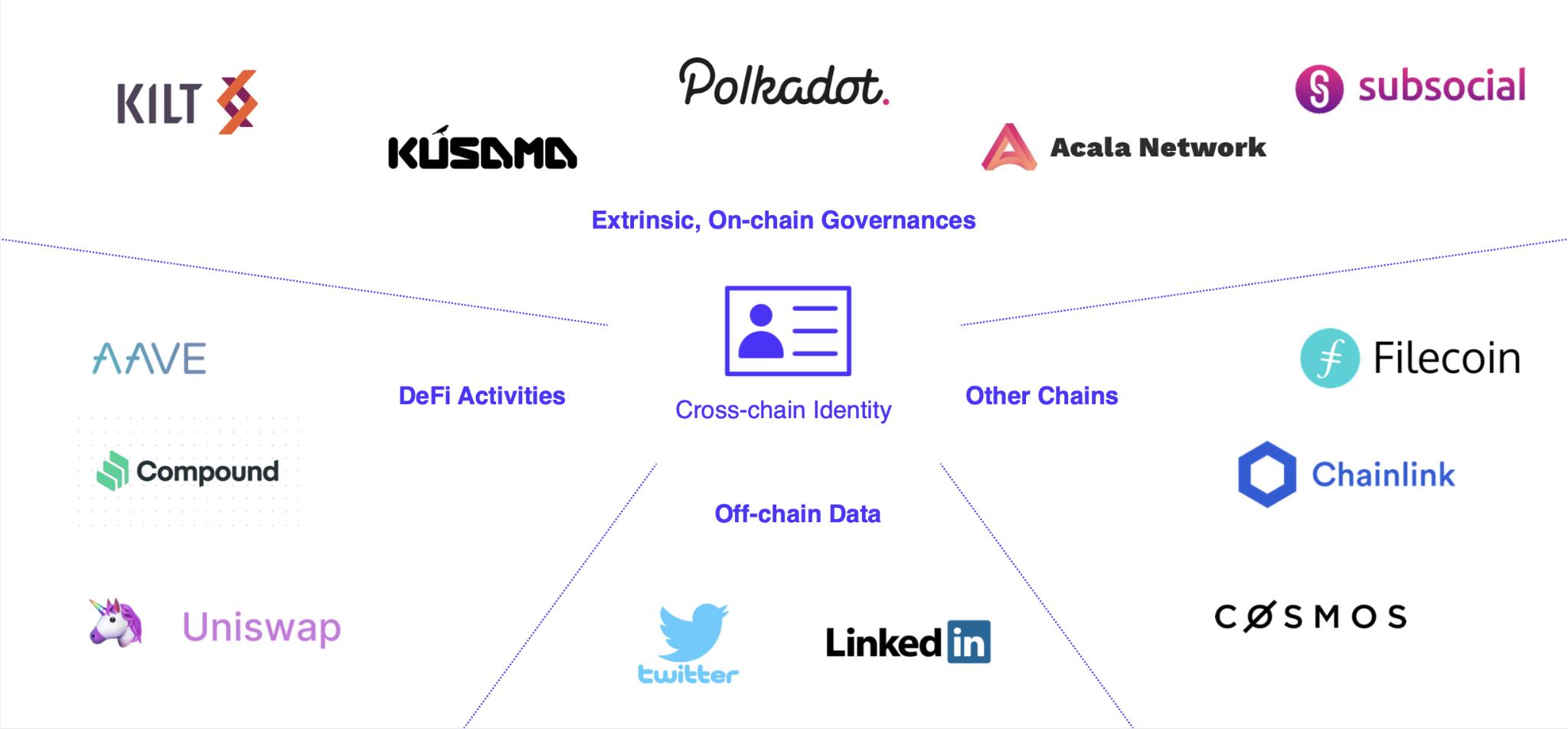
Source: Litentry Blog
LTO Network
A Blockchain as a Service (BaaS) model that organizations can integrate into their existing systems to gain the advantages of blockchain architecture. This also provides the infrastructure for nodes and participants on these networks to share and verify digital identities.
DID (public address of identity) on the LTO blockchain.

Source: LTO Identity File
Additionally, LTO uses Chainlink oracles to create cross-chain decentralized identities. Therefore, identities on other chains can also be represented on the LTO network.
An LTO DID address based on an Ethereum public key.

Source: LTO Identity File
Similar to Litentry, LTO aims to facilitate the interoperability of DIDs and smart contracts.
Although different approaches have been adopted, ultimately, all these solutions (including many others) contribute to entities claiming ownership of their identity and how it is used, as mentioned at the beginning of this article.
Another very important aspect of DID is that they not only grant individuals sovereignty over their identity but also over the data they generate. Our data is often used to advance a certain agenda, whether to influence our consumption habits or for worse purposes. Our lack of control over our information leads to polarization, as we cannot choose how and whether our data is used. DID grants us control over this—if entities wish, they can choose to monetize their data. Only when they control the data can they have this choice.
DID in DeFi
With DID, DApps can offer different levels of service to different users. For example, an entity with a good repayment record could obtain a loan from a collateral-reduced lending platform, or new DeFi projects might prevent bots from exploiting their airdrops targeted at human users. Furthermore, there are many other use cases not limited to the new decentralized internet.
DeFi is attractive to many because it is completely permissionless and does not discriminate. A person's race, social status, beliefs, political views/environment, and net worth are not considered by the open protocols managing these financial products and services.
While DeFi is trustless, allowing anyone to use the new financial system, its lack of trust also has drawbacks. Loans using protocols like Maker, Compound, or Aave require over-collateralization because risks cannot be assessed based on individuals. While powerful, this limits functionalities like obtaining collateralized loans or large commercial loans using DeFi protocols. Ironically, more trust must be established within a trustless network.
DeFi will ultimately introduce globally compliant regulations, such as Know Your Customer (KYC) and Anti-Money Laundering (AML). Lending protocols like Compound and Aave are ahead of this curve, creating separate pools of funds like Compound Treasury or Aave Arc that are compliant with U.S. regulatory frameworks for institutional investors.
Rather than relying on traditional trust-based identification methods that have disappointed people in the past (see: large-scale data manipulation like Cambridge Analytica, data breaches like the Equifax breach), decentralized identity can be attempted as a replacement.
Final Thoughts on DID
DID is an important piece of the puzzle that can enhance trust in Web3 while maintaining individual privacy. Decentralized identity has been one of the most challenging applications of Web3, and the exact form of DID remains uncertain. Various attempts at regulatory-compliant and fully sovereign on-chain identities will continue to emerge.
Ultimately, unlocking the benefits of permissionless blockchain and decentralized finance will require sources of reputation, and DID is a potential pathway to create trust in such a trustless system.










