Exploring Web3 Security Guidelines from a Case of a Stolen Wallet
Original Title: "Technology | Exploring Web3 Security Guidelines Through a Case of a Stolen Wallet"
Original Source: Alpha Rabbit Research Notes
Original Author: Chris Alpha Rabbit
Incident
One morning during the New Year's holiday in 2022, Xiao C was preparing to write code and continue testing on-chain contract transactions with Web3js. Suddenly, he discovered that his test account (on the Bsc chain) had been drained to zero in MetaMask, even though there had been 100 USD in the account the night before. After checking the transactions, he found:
The money was gone. Where did it go?
Background
Xiao C, who comes from a technical background, has recently been learning blockchain development. As a professional developer, he has always been cautious and usually runs tests on a test network before deploying to the main network. However, he did not realize that the entire industry is still in a relatively chaotic phase, and his complacency and habitual actions led to the loss.
How was the loss incurred?
On the last day of 2021, Xiao C stumbled upon an interesting account (which had many active transactions) and started tracking some of its on-chain transactions. He then came across a very interesting project (which promised high annual returns) and, without thinking, connected it to his MetaMask and approved the transaction, as this is the usual process for Web3 projects: approve and then transfer.
But then something shocking happened: after clicking approve, the entire website suddenly froze (during this freeze, the thief transferred the money away), and there was no response. Xiao C didn't take it seriously, closed the site, and went on to do other things.
About a day later, when Xiao C returned to develop, he found that all the money in his account was gone. After checking the transaction history, he discovered that the entire balance had been transferred away.
Review of the Process
How did the thief transfer all the money from Xiao C's account?
Phenomenon: As long as you approve, theoretically, you can transfer the corresponding money without needing a private key.
Xiao C traced back and found that the issue originated from an approve action on a phishing website, so he traced the transaction record.
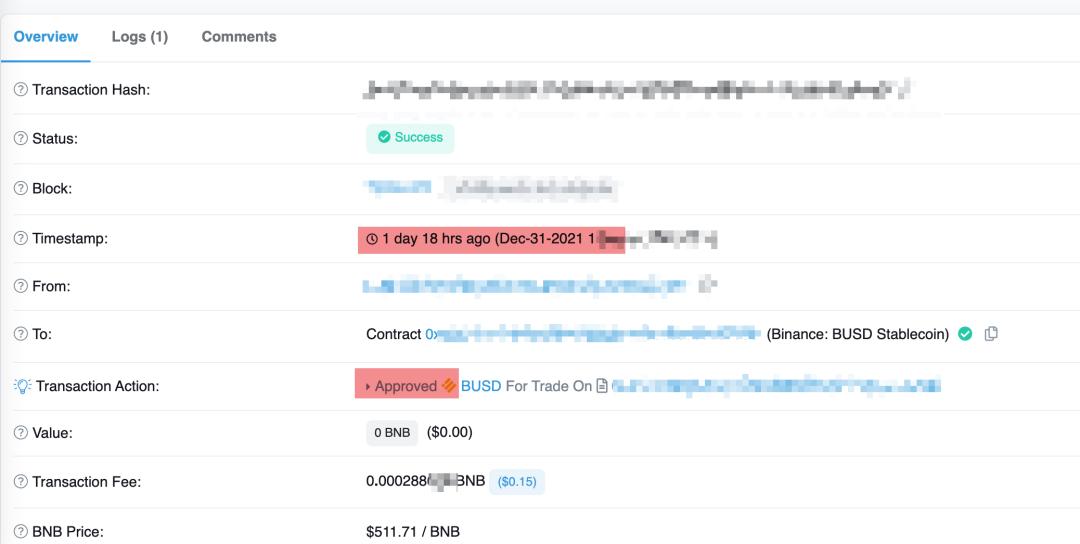
As shown in the image, he first approved a contract, allowing the phishing contract to operate on the BUSD in his account, and there was no limit on the amount.
Why BUSD? Xiao C recalled that upon entering the phishing site, BUSD was selected by default. It is likely that after the thief linked the wallet, they filtered out the token with the most money in the account.
Then, when Xiao C thought this was a new swap contract with high annual returns and was ready to try it out, he followed the usual process and approved it. After the approval, the website froze.
Later, upon tracing back, he found that just seconds after the approval, the contract directly triggered a transfer operation, transferring the BUSD tokens away.
He then checked the authorization information.
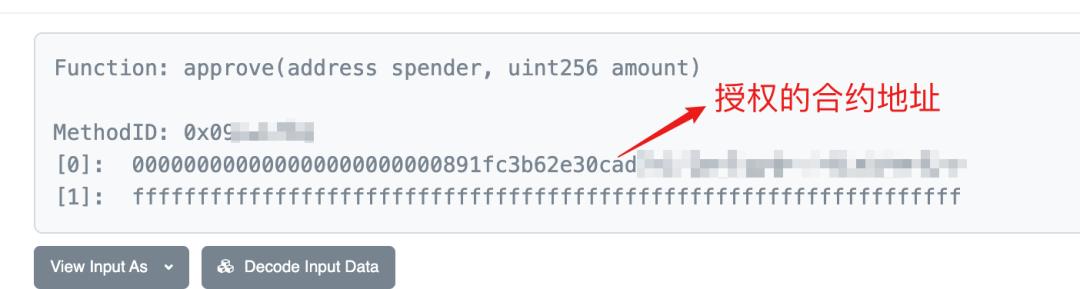
Basically, when MetaMask authorizes by default, it converts to a number we recognize as 1.157920892373162 multiplied by 10 to the power of 59. This can essentially be understood as an unlimited transfer, meaning this authorization allows the contract to manipulate the tokens in his account without limit. At this point, Xiao C felt a chill down his spine because he had previously clicked approve many times without checking.
Then the hacker controlled a wallet address that could execute this contract method and initiated the contract transfer method to take the money away. So, friends should definitely be careful when clicking on MetaMask authorizations.
Xiao C checked and found that the thief's account now had about 30,000 USD worth of tokens, and there were still continuous victims transferring money. However, in the face of blockchain, there is no way to find out who this hacker is.
Where the Problem Occurred
Where did the problem lie?
Since he had been learning about blockchain recently, Xiao C roughly sorted out the logic of this phishing scheme. One should never have malicious intent, but always be on guard against others. If anyone is interested, they can learn more about:
Normal Transfer
Case 1: Direct transfer between users, User A transfers BUSD to User B.
The contract normally checks the following logic:
1) Whether User A has enough balance; 2) Whether the transfer was initiated by User A.
The process is shown in the diagram below.
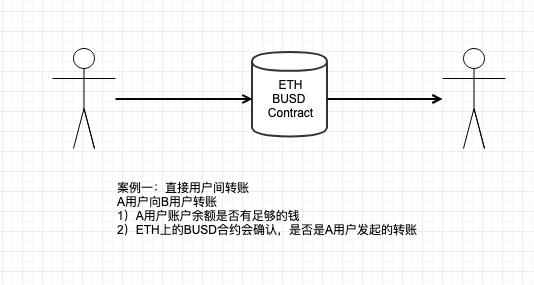
Normal Contract Exchange
This is the process we usually use when exchanging on PancakeSwap, Uniswap, etc.
Case 2: Token exchange through swap, User A exchanges tokens (BUSD for WBNB). The contract checks:
1) Whether User A has enough BUSD (assuming the swap contract has been authorized to operate User A's BUSD tokens).
2) The swap contract takes 500 BUSD from User A's account and puts it into the swap contract pool (assuming the exchange rate is 1:500).
3) After success, the contract transfers 1 BNB back to User A's account.
Note that points 2 and 3 are controlled by the contract to operate the tokens. This means that the contract can bypass directly initiating operations on the tokens in our account.
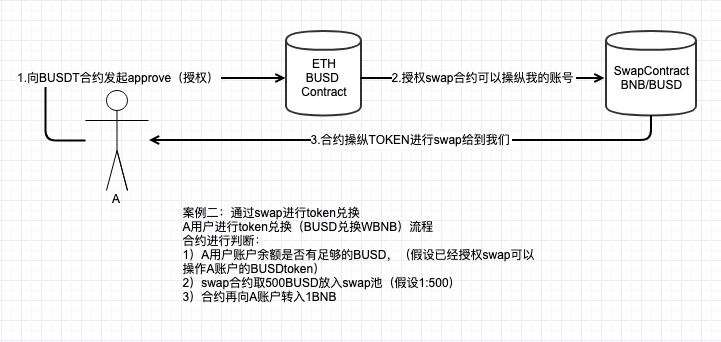
Phishing Contract
First, look at this tracing diagram.
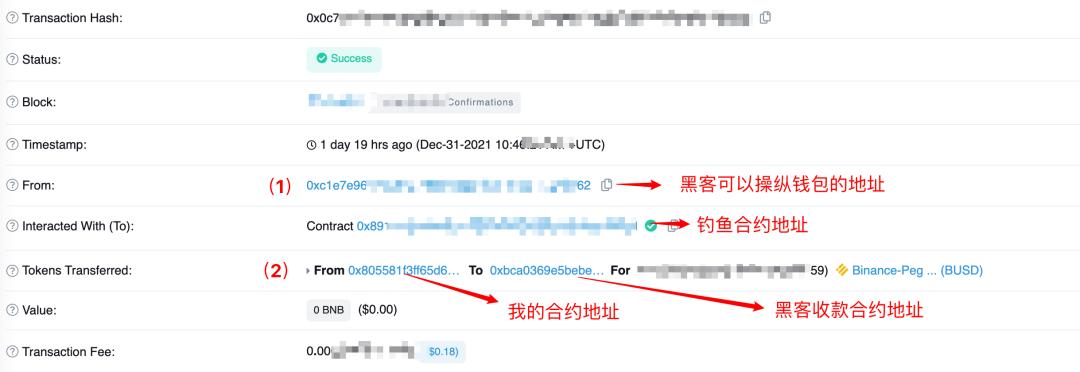
In a normal transfer, the transferring party and the contract executing the transfer should be the same person, meaning the addresses in the image (1) and (2) should be initiated by the same person. However, in the transaction where I was transferred, these two addresses are not the same. It is speculated that a wallet address capable of executing the phishing contract controlled the execution of the contract and transferred the BUSD that I authorized to the phishing contract.
Upon checking the phishing contract, unsurprisingly, it was an encrypted contract. However, it’s not difficult to understand; anyone who has slightly learned Solidity knows that when defining a contract, you can simply set multiple Admin or Owner addresses.
So, in the future, be sure to pay attention to the endorsements of project parties and do not authorize unknown projects casually!!!
Safety Recommendations
Due to this incident, Xiao C searched for some useful advice and methods and saw many bloody lessons.
Here are some methods that everyone can choose according to their needs.
1) Do not share keys
I have seen posts suggesting generating multiple accounts from one mnemonic phrase; I do not recommend this, as it could lead to a total loss.
2) Save keys offline
Many clipboard tools and input methods now upload your clipboard records to the cloud. If you copy your keys directly and the cloud leaks, your keys will be compromised.
My suggestion is to write them down immediately after generating them. Of course, when writing them down, you can also refer to my method of encrypting the keys with your own dictionary, for example, replacing a with 1, b with 2, and 1 with a, so that even if someone sees your physical keys, they cannot access your digital assets.
3) Separate development and testing (isolate airdrop and main accounts)
Install two browsers, one can be Chrome and the other Brave. One manages your main wallet, while the other can be used for airdrops and various on-chain operations.
4) Do not download software from unknown sources
Avoid using Baidu or other sources to download unknown software. I have seen cases where downloading a pirated MetaMask led to bankruptcy. Always download from official addresses; if possible, refer to Google Play, Chrome Web Store, etc.
5) Immediately check your authorizations
Here are several websites to check: Debank is not open-source but has a good UI interaction; the others are open-source, and you can choose for yourself.
https://debank.com/
https://approved.zone/
https://tac.dappstar.io/
https://ethallowance.com/
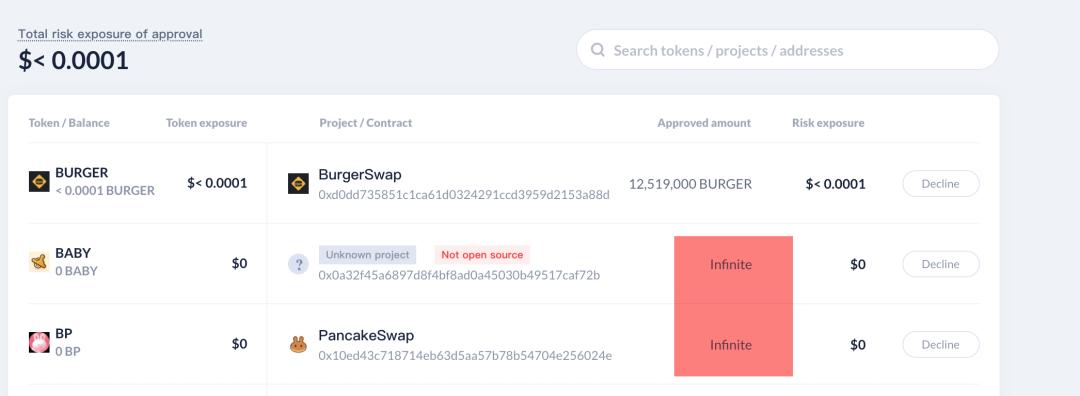
As shown in the image, it essentially indicates unlimited authorization.
Every time you invoke MetaMask, be sure to check the authorizations carefully; do not mindlessly click authorize and proceed like I did.
6) Confirm contract security before granting authorization
https://www.slowmist.com/service-smart-contract-security-audit.html
You can use SlowMist's contract auditing feature.
You can also check if the contract is open-source; if it is, confirm whether it is an upgradable contract, etc.
7) Be cautious about security when claiming airdrops and benefits
Use a secondary account to claim, and do not use your main account. You can set limits when authorizing!!!
8) Be wary of social engineering intrusions; be cautious of strangers messaging you on Discord
For example, on Discord or Telegram, if someone you’ve known for a few days says they want to help you make money through airdrops and asks you to install software they send you and log in, there is a 99.99% chance you will lose everything. Your account will be stolen.
In particular, on Discord, when entering the official NFT Discord, someone may message you, claiming you have received a whitelist and providing a mint link. Scammers will change their avatar and name to look official, actually pulling you into a group to execute the scam.
As long as you are not greedy, these scams are quite easy to spot. They usually tell you to mint within a few hours, with a quantity of 1-10. Many popular projects only allow one or two mints per whitelist, so if they come up with a limit of 10 with a time constraint, it’s suspicious.
Additionally, scammers may imitate the project’s official website to create a fake site and message people in the project server to get them to mint.
Some friends have bought fake NFTs on OpenSea, only to find out later that they were not official, and then a few days later, the NFT disappeared from their account, even after being charged… (How did they find out? By checking the blockchain and the official Discord that posted the official OpenSea URL).
There are also fake collab.land scams that steal wallet passwords, claiming to airdrop to big accounts and then saying that the big account bought that NFT/token.
As the new year arrives, everyone must pay attention to security. I hope that all readers of this article can stay safe and sound!
This article thanks the author Chris.










