Yuanwang Capital's Tian Hongfei: The Collapse of Decentralized Belief? Let's Take a Look at the BEC Architecture
Author: Yuanwang Capital
In the recent Russia-Ukraine war, the United States, in conjunction with the European Union, dropped a "financial nuclear weapon" on Russia, not only freezing Russia's foreign exchange reserves and kicking it out of SWIFT but also demanding that major exchanges ensure that Russians sanctioned by the U.S. and the West cannot evade sanctions through cryptocurrencies.
Not only did Coinbase and other centralized exchanges respond quickly, but it was also surprising that blockchain infrastructure companies like MetaMask, OpenSea, DMarket, and Infra had to join the sanctions, either actively or passively.
The Ukrainian Deputy Prime Minister even called on the West to freeze not only the crypto addresses associated with Russian and Belarusian politicians but also the addresses of ordinary users. This series of actions not only caused short-term turmoil in the cryptocurrency industry but also raised doubts about the decentralized vision of blockchain, leaving believers in decentralization very disappointed.
What happened to decentralization? Didn't you, MetaMask and Infra, claim to be decentralized infrastructure before?
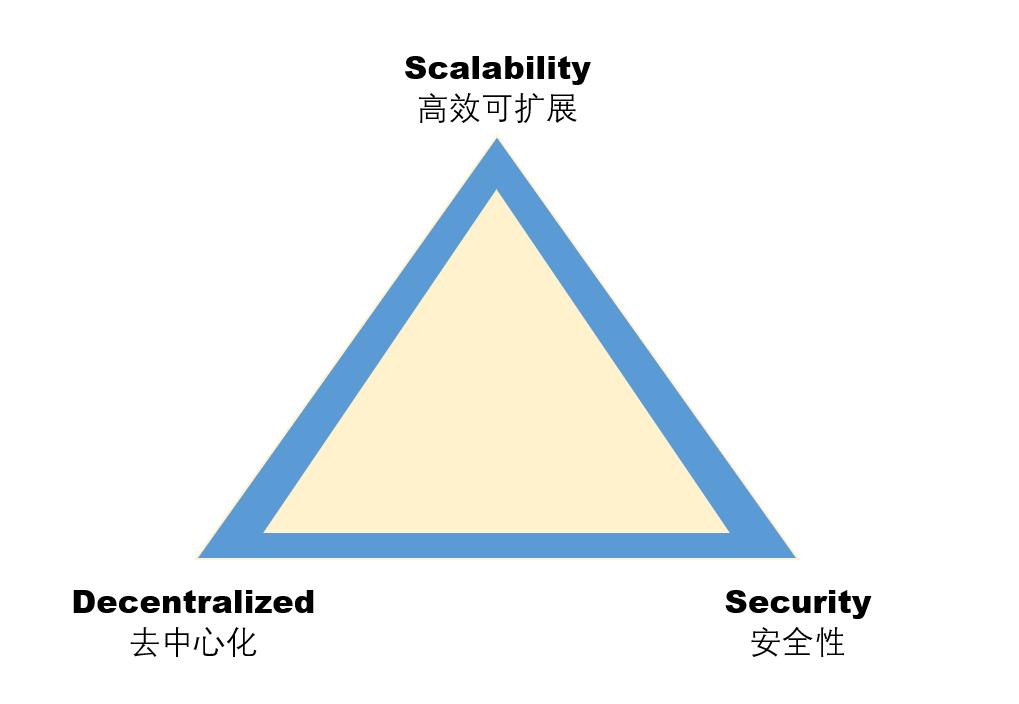
Compared to before 2020, the multi-chain architecture on blockchain has become increasingly evident today, with more than 10 public chains having a market capitalization exceeding $10 billion. The number of users and the Total Value Locked (TVL) of these public chains are quite substantial. However, among so many public chains, only Ethereum's Vitalik has prioritized anti-censorship and decentralization as the first priority in the "impossible triangle" of blockchain design (the so-called "impossible triangle" refers to the difficulty of achieving good "decentralization," strong "security," and high "transaction processing performance" simultaneously in public blockchain design). Other blockchains are promoting themselves as faster and better experiences compared to Ethereum, but the cost of this is the decentralization of the public chain.
Before 2015, there were only Bitcoin and "other coins" in the world. All Bitcoin wallets were designed to protect privacy by following the principle of changing addresses for each transaction and randomly changing connection nodes for security. After 2015, as the volume of blockchain data grew larger, users in the crypto space became increasingly detached from the core users of encryption, and the ICO boom led many grassroots users to move from centralized exchanges to decentralized wallets. The design of blockchain infrastructure began to tilt towards centralization on the decentralization scale, as such designs were easier to enhance user experience.
As a "trusted third party" in the blockchain world, the design of blockchain infrastructure has undergone the following changes on the path to gradual centralization: from POW verification to DPOS verification; a large number of node service providers have emerged. These designs serve as short-term effective shortcuts, allowing blockchain infrastructure service providers to quickly offer excellent user experience services to meet the rapidly growing demands of blockchain data scale and user scale. However, the potential problems of these solutions have erupted during this Russia-Ukraine war.
I believe that the future technical architecture of Web3 should not be at the two extremes of complete decentralization (like POW full nodes) and centralization (like Infra centralized nodes), but rather a structure that starts from the user end, empowers the user end, and then extends to completely decentralized blockchains based on data and scenario needs, forming a layered network architecture. The specific implementation form is edge computing, from personal edge nodes to multi-layered, multi-regional edge nodes, and then linking to completely decentralized blockchains, allowing users and DApps to choose at which edge node level to achieve a certain degree of decentralization.
Let's deduce: since the birth of information technology, computer architecture has gone through the following stages:
In 1950, the server-terminal architecture composed of mainframes and thin clients, where data generation and computation were centralized in data centers;
In 1980, the server-client architecture began, where data generation and computation were jointly undertaken by servers in data centers and terminal computers;
In 2000, the server-browser (including apps) architecture emerged, where most data generation and computation were handled by servers in data centers, with a small portion handled by terminal computers or mobile phones.
The common feature of the above architectures is that data is centrally stored in large databases managed by data center servers, providing data storage and access services for distributed terminal computers.
The typical characteristics of the evolution from Web 2.0 to 3.0 include: evolving from a core focus on improving efficiency to a core focus on personal value control; evolving from eliminating information asymmetry to a core focus on value exchange. We believe that the core of the infrastructure of Web 3.0 is based on personal control of digital assets, supported by high-frequency massive value exchanges as communication protocols, and numerous user application scenarios. The core architecture of this implementation is the Blockchain-Edge-Client (BEC) architecture.
Next, we will identify the contradictions between typical user scenarios of Web3 and the current client-server architecture, and then deduce how BEC can better support the changes of the Web3 era.

Photo by imgix on Unsplash
1: The Basic Needs of the Web3 Era Include:
The premise of decentralization is the identification of personal identity (IDM), where traditional identity recognition is represented and controlled by government departments and user accounts on websites. From the anonymous era of the internet in 1996, where you could chat without knowing if the other party was a dog, to the real-name phase dominated by Facebook in 2004, internet applications have transitioned from gaming and information retrieval tools to e-commerce and enterprise SaaS. If the future internet transitions to a value internet, then user privacy and digital asset protection will become paramount, and the design of computer architecture will need to shift from high efficiency and high availability to high security and high privacy protection.
Today, the IDM in the blockchain industry resembles the internet before Facebook, using public key addresses as identity identifiers or bored ape NFTs as identity representatives, with anonymity as the only feature. If blockchain applications truly enter the socio-economic realm, decentralized identity management (DID) needs to transition to a real-name phase, supporting authorization, authentication, and a decentralized contact book (Decentralized Contact Book), which requires a new generation of DID protocols and more powerful wallets. Since users' clients (most often mobile phones) are often tied to real identity features, it is challenging to provide privacy protection for users; therefore, personal edge nodes will greatly enhance users' ability to manage their identities.
2: Decentralized Credit Score
Credit scores are a fundamental component of value exchange; without credit, exchanges can only be barter and over-collateralized lending, just like the popular DeFi in 2020, which operates on the basis of over-collateralization.
Future developments will be based on multi-source data (including blockchain transaction data and off-chain data), deriving personal credit scores through zero-knowledge proof algorithms running on edge nodes.
Personal credit scores will be applied in airdrops, unsecured lending, DAO governance, and even PoS staking.
3: DCB (Decentralized Contact Book)
A decentralized contact book is the foundation of user authorization and authentication, such as authorizing certain users to access their photos or authorizing certain applications to access their private data. The design of a decentralized contact book can refer to the historical Web-of-Trust or the transfer records of blockchain to form, and can provide user address lookup and mapping functions through the DCB protocol.
4: DIM (Decentralized Instant Messaging)
Since users' chat clients cannot remain online 24/7, all current chat software, including WeChat, WhatsApp, Telegram, and Discord, cannot avoid relying on centralized servers for storage, forwarding, or handshake support.
A completely decentralized chat software inevitably needs to rely on personal edge nodes to support always-online and message-pushing functions.
5: Personal Data Assetization
The widespread use of mobile phones and enhanced functionalities have led users to accumulate a large amount of personal data, intentionally or unintentionally. In the Web 2.0 era, this data became a gold mine for internet giants, forming the mainstream business model of users selling personal privacy for free services. The only way to break this model is for users to pay fees for using products and to keep their own data.
The prototype is that users need to pay running fees (gas) every time they run an Ethereum smart contract. The corresponding user data must be stored on their own edge nodes. If a third party needs to access and use this data, it must go through user authorization, using homomorphic encryption or downloading algorithms to edge nodes to compute and only share the results. This undoubtedly provides an excellent method for protecting creators' copyrights.
6: Decentralized DApp Store on Edge Nodes
Currently, various centralized apps on mobile phones are provided to users as a black box environment, where users cannot control the trusted operational status of their resources and applications. This environment often encounters bugs, leading to data loss and abnormal application operation.
On the other hand, there will be a decentralized DApp store on edge nodes, where different DApps for different blockchains can be installed on users' edge nodes. Since the data on these edge nodes is controlled by users themselves, and although this data is distributed, it can be synchronized. Edge node devices can also be contributed as basic resources for developers to use, allowing developers to create various functional DApps based on the computing power, storage, and network resources of edge nodes.
7: A Digital Asset Exchange Network Based on General Trading
Before the emergence of Web 3.0, all business models on the internet derived their revenue from satisfying user entertainment (gaming, pornography, and gambling), shopping (e-commerce), and improving work efficiency (SaaS), with advertising revenue becoming the main source of income for most internet companies, including search companies (Google and Baidu) and social companies (Meta and Twitter).
The essence of the advertising revenue model is exchanging user privacy data for free services. The core of Web 3.0 is that users control their digital assets and pay service usage fees (GAS).
Clearly, like today's DeFi, users need to authorize each contract, and the user process of signing every time a function is called cannot support the use of complex products. Moreover, with 500 exchanges listed on CoinMarketCap, there are 20,000 types of virtual currencies (for comparison, the total number of listed companies in the U.S. and China is only 10,000), and with hundreds of public chains, it is very complex and cumbersome for a user to perform cross-chain operations and exchange between different tokens.
To support any meaningful Web3 application scenarios, the future internet computing architecture should be based on a massive high-frequency value exchange network, where the invocation of one public chain contract to another and the payment of fees should be completely high-speed and automatic, without requiring active user awareness and participation. We call this a high-speed high-frequency automatic value exchange network, and to realize such a network, user-controlled edge nodes are fundamental. The main reasons include:
1. Web 3.0 Requires Online Link Capability of Edge Nodes
Since user devices do not need to remain online at all times, and Web 3.0 application scenarios often require users' digital assets to be online (including the delivery of chat messages and sharing of personal data), this contradiction needs to be resolved by user-controlled edge nodes.
2. Web 3.0 Edge Nodes' Storage Capability
Due to the decentralization of Web 3.0 and the requirement for personal control of data, users need storage space that they can control. Currently, blockchain storage projects face two major problems: they cannot meet the immediate access needs of any application, and the cost of using blockchain to store data is far higher than that of centralized storage solutions.
A better solution is to layer data storage. Just like modern computer architecture designs, storage and computation are layered into global long-term storage, partial computation, and temporary caching. The network computing architecture is also layered, with blockchain serving as the global computation and long-term storage layer for the entire network, while the edge serves as local computation and temporary caching services (like Infra). User nodes only store data necessary to protect user privacy and enhance user experience, with mobile devices serving only as data collection, user security verification, management, and user service interfaces; the intermediate edge may be divided into more layers, with user-facing edges responsible for storing user privacy data, while edges further away from users handle shared data caching.
3. Web 3.0 Requires Computing Power from Edge Nodes
Since users control their data assets, any computation based on user data needs to run within the user-controlled storage space, allowing personalized recommendation algorithms to share only computation results without sharing private data.
Additionally, representing users in value exchanges requires computing power to support high-frequency and high-speed exchanges between tokens and calls between contracts.
4. Edge Nodes Can Provide Users with Web 2.0 User Experience
Edge nodes decentralize computing services and bring them closer to data sources, reducing the amount of data transmitted and its propagation distance, while also caching a large amount of blockchain data, significantly reducing latency and providing users with more interactivity and better responsiveness. This ensures the delivery of DIM messages and the availability of user data for third parties. It can be imagined that in the future digital world, billions of edge nodes will support the operation and development of the world, with a vast invisible data network interwoven in every corner of the world, where each node is constantly exchanging data with one another. It is precisely because of the existence of edge computing that each node can form its own "thinking."
In the future, every user or terminal will be like the snowman in Frozen, with a cloud following them, providing personalized services. Perhaps we should call it snowman computing.










