Wintermute's private key was "brute-forced," resulting in a loss of $160 million, with suspected causes having been warned about earlier
Author: Loopy Lu, ODAILY Planet Daily
On September 20, Wintermute was hacked.
This attack not only caused losses for Wintermute but also exposed a risk that is easily overlooked. The hackers used a relatively rare attack method—"cracking private keys," which serves as a warning for all cryptocurrency holders. However, there is no need for excessive concern; this private key cracking does not threaten the elliptic curve encryption algorithm but rather indicates a security vulnerability in a private key generation tool. If investors have not used tools with similar risks, they will not face the same threat.
Wintermute is a well-known cryptocurrency market maker dedicated to creating liquid and efficient markets in cryptocurrency. This afternoon, its founder Evgeny Gaevoy posted on social media that Wintermute lost $160 million in a DeFi hacking attack.
Unusual Attack Method: Hackers Obtained Wallet Private Keys
Unlike the common attack methods such as "vulnerabilities," "flash loans," and "price manipulation," the method used by the hackers this time was more obscure—brute force cracking.
The Beosin security team discovered that the attacker frequently used the address 0x0000000fe6a… to call the 0x178979ae function of the 0x00000000ae34… contract to transfer funds to the 0x0248 address (the attacker's contract). By decompiling the contract, it was found that calling the 0x178979ae function requires permission verification. Through function queries, it was confirmed that the 0x0000000fe6a address had setCommonAdmin permission, and this address had normal interactions with the contract before the attack, confirming that the private key of 0x0000000fe6a was leaked.
Multiple security teams have publicly stated that the smart contracts and EOA wallets owned by Wintermute were stolen by the attackers. Observing the stolen wallet address, it is not difficult to find that the address is very "regular," starting with seven zeros. The theft of this wallet may be related to Wintermute's use of Profanity.
Profanity is an EVM vanity address generation tool that allows users to generate wallet addresses, including custom character combinations.
In the comments on Profanity's GitHub, we can also see previous discussions by developers about this project.
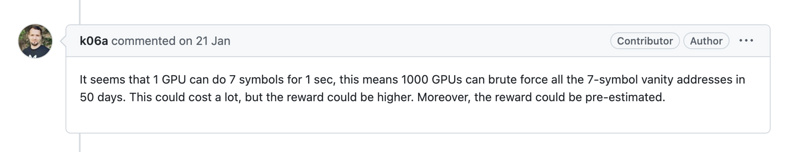
The co-founder of 1inch pointed out as early as January this year that there were security flaws in this tool: "1 GPU can compute 7 symbols per second, and it only takes 1000 GPUs running for 50 days to crack all addresses generated by this tool." Subsequently, the developers added a security warning in the project's readme, advising users "not to continue using this tool under the current circumstances."
Despite such prior warnings, it is clear that some people did not take them seriously.
Risk Warnings Were Issued Early but Did Not Attract Attention
Just days before the Wintermute incident, the security risks of Profanity had already been noted by the industry.
On September 15, the official blog of 1inch Network published an article pointing out the security risks of Profanity. "If your wallet address was generated using the Profanity tool, your assets are no longer safe. Please transfer all your assets to another wallet as soon as possible!"
1inch's research found that hackers exploited the Profanity vulnerability in the following way:
- Obtain the public key from a fake address (recover from the transfer signature).
- Deterministically expand it to 2 million public keys.
- Repeatedly narrow down the range until the seed public key is obtained.
Through this method, hackers can obtain the private keys of any address generated using Profanity.
A subsequent investigation by blockchain researcher ZachXBT showed that the assets stolen by hackers through this vulnerability had exceeded $3.3 million.
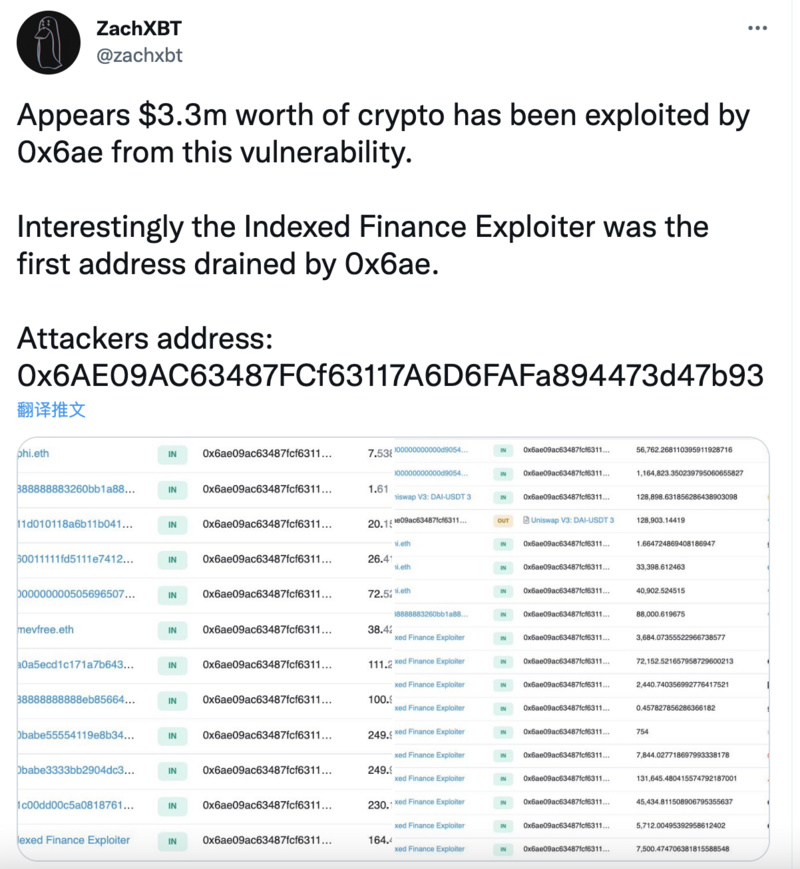
Although this research article was published five days before the theft (discussions on the project's GitHub can be traced back to January), the security risk still did not attract attention. Ultimately, Wintermute paid the price of $160 million, making the Profanity security vulnerability well-known to us.
Wintermute States That This Incident Will Not Impact the Market
After confirmation from multiple security agencies, the attacker's address has been locked as "0xe74b28c2eAe8679e3cCc3a94d5d0dE83CCB84705." The attacker's smart contract is "0x0248f752802b2cfb4373cc0c3bc3964429385c26."
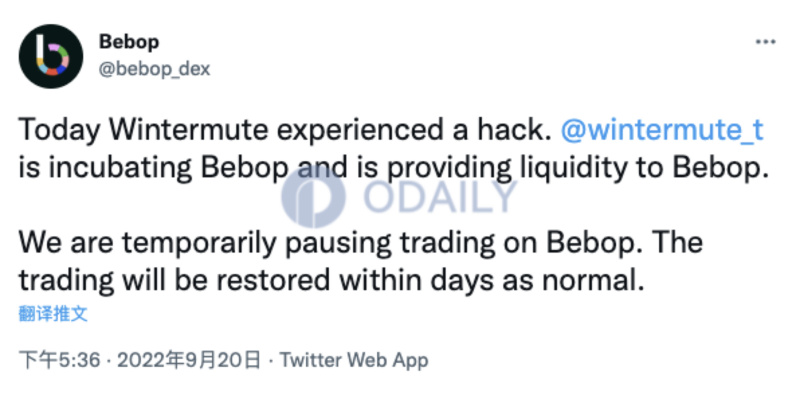
Following this attack, in addition to the affected wallets, the decentralized exchange Bebop launched by Wintermute was also impacted. Bebop's official Twitter announced that the platform has suspended trading and will resume in a few days; it stated that its contracts are unaffected and that users' funds and private keys are secure.
Wintermute stated that among the 90 assets hacked, only two had a nominal value exceeding $1 million (not exceeding $2.5 million), so it is expected that there will not be significant selling pressure on the market. Additionally, its CeFi and OTC businesses were not affected.
At the same time, Evgeny Gaevoy stated that Wintermute's current solvency is twice the remaining equity, and Wintermute's services may be interrupted today and in the coming days, but will return to normal afterward.
Currently, Wintermute still wishes to regard the attackers as "white hat hackers" and calls on them to contact Wintermute proactively.































