Stanford researchers conceive reversible transactions on Ethereum: ERC-20R and ERC-721R
Written by: Kaili Wang, Stanford University Blockchain Researcher
Compiled by: 0x11, Foresight News
The irreversibility of blockchain transactions is both a blessing and a curse. In 2021 alone, there were $14 billion worth of cryptocurrency stolen due to incidents like BAYC phishing, PolyNetwork attacks, Harmony Bridge compromises, and Ronin hacks. With so many "undeniable" thefts occurring frequently, there is no "undo button" (like credit card payment reversals) to cancel transactions, and not everyone is as lucky as Wormhole, having Jump Crypto to back them up when needed.
But what if there was a fair way to reverse these thefts?
This is the question that a few of us at Stanford University (Dan Boneh, Qinchen Wang, and I) have been working to answer over the past few months. We designed token standards that support reversible transactions for ERC-20 and ERC-721 (when there is sufficient evidence), wrote a paper about them, and implemented a code prototype. We refer to these token standards as ERC-20R and ERC-721R.
Now, you might be thinking: reversible tokens? Doesn't that contradict the purpose of blockchain? In fact, it does not. This proposal does not remove transactions from the blockchain; it simply allows funds to be returned to their rightful owners through a decentralized judicial voting process after the fact.
How It Works
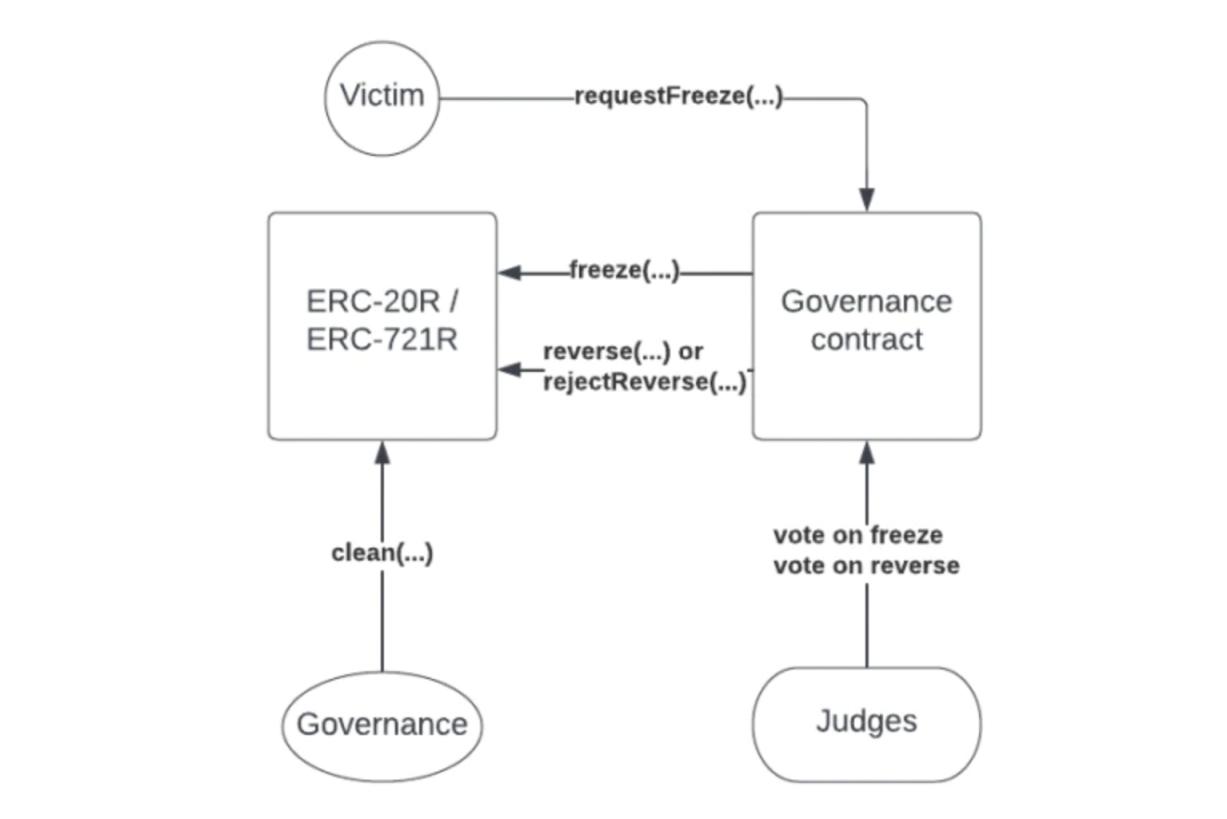
Process of reversing a transaction
Suppose an attacker steals funds from a victim. The funds may be further transferred to other addresses, as shown in Figure 1, and the following occurs:
- The victim requests to freeze the stolen funds. The victim submits a freeze request to the governance contract along with relevant evidence and some collateral assets. The disputed transaction must have occurred recently (there is a fixed reversible time window).
- Judges accept or reject the freeze request. A certain number of judges decide whether to freeze the assets through decentralized voting, which may take one or two days. If they reject the request, the reversal process stops, and the victim loses their collateral assets. If they accept the request, the governance contract will call the freeze function in the ERC-20R/ERC-721R contract.
- Execute the freeze. For NFTs, freezing simply prevents the NFT from being transferred. For ERC-20R, it tracks the stolen funds and prohibits the transfer of those funds. Note that as long as the account owner's balance is above the frozen amount, the account owner can still transact with others. This process can become complex, which I will explain in the next section.
- Trial. Both parties can present evidence to a decentralized court, and ultimately the judges make a ruling, at which point they instruct the governance contract to call the reverse or rejectReverse function of the affected ERC-20R/ERC-721R contract. If the rejectReverse function is called, the freeze on the disputed assets is lifted. The trial process may take a long time, potentially several weeks.
- Reverse the transaction. Calling the reverse function sends the frozen assets back to the victim.
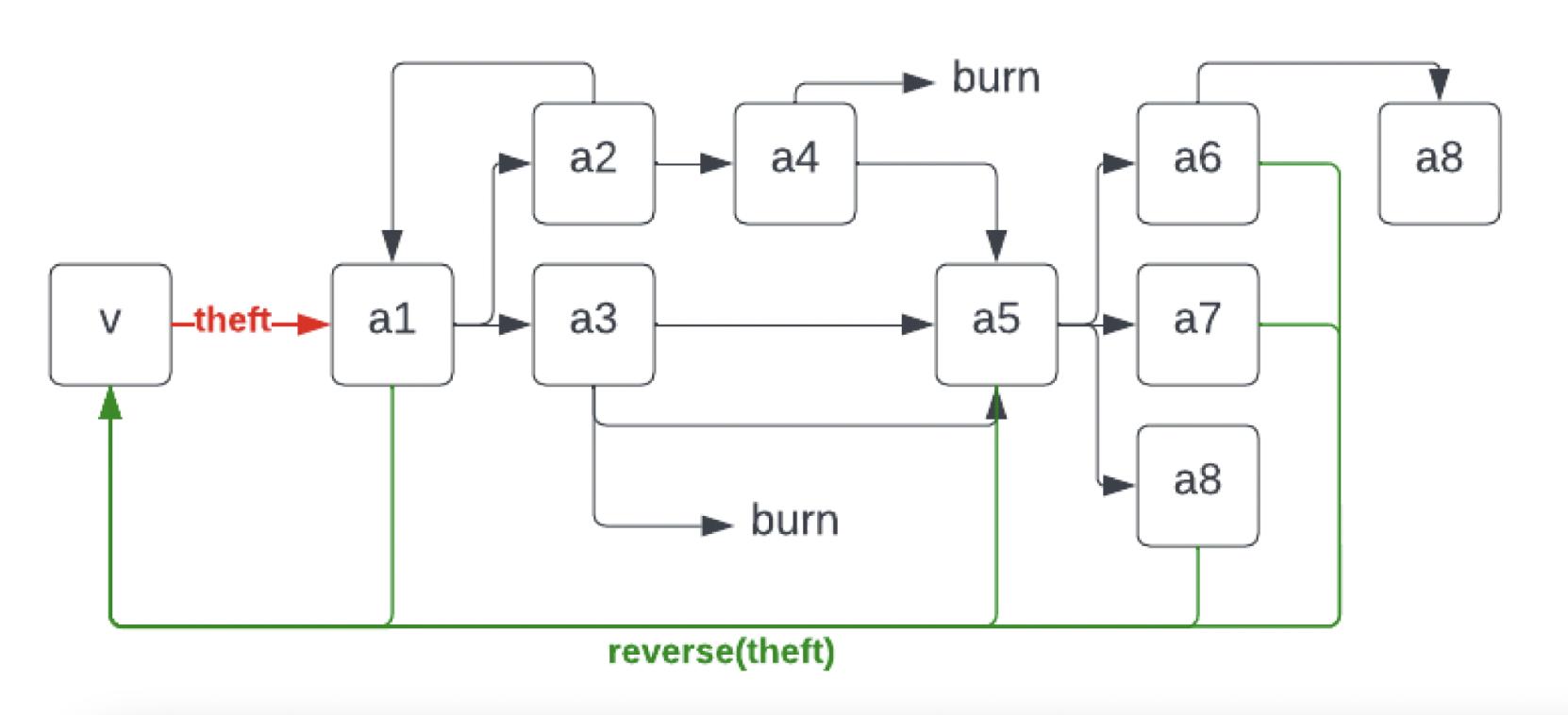
Figure 1: Transaction Graph
Tracking Stolen Funds
Stolen assets are rarely just left in one place. Attackers often transfer assets from one account to another in some manner. In this case, attackers can even monitor the mempool and transfer assets into front-running trades upon seeing a freeze request submitted. A solution to avoid this is to perform the entire freeze on-chain in a single transaction, so attackers cannot "escape" the freeze.
But we cannot simply disable the accounts of all related assets, so how do we decide what to freeze and whose accounts to freeze? If it is an NFT, freezing is straightforward: just look at who currently owns the NFT and freeze that account. However, if it is an ERC-20 asset, the fungibility of the currency makes freezing very complex. These funds can be distributed across dozens of accounts, put into anonymous mixers like Tornado, or exchanged for another cryptocurrency. If it goes through many accounts, at least some of them will be associated with the hacker, but some are likely innocent. It is not always possible to correctly identify the guilt of each account. Therefore, we provide a default freezing process for tracking and locking stolen funds. Our algorithm ensures:
- Assuming no destruction, enough assets are frozen to cover the theft amount (subtracting destroyed assets from the returned amount),
- Account funds are only frozen if there is a direct transaction flow with the stolen assets,
- The algorithm runs with reasonable runtime complexity relative to the transaction graph (Figure 1).
We discuss more details about the algorithm in the paper.
Reversibility is Contagious
In transactions, exchanging two different reversible tokens is safe as usual; if one party requests a freeze, it is possible to recover funds from the other party. However, exchanging reversible tokens for irreversible tokens can be dangerous; to protect themselves from reversals, trades may only be completed after the reversible time window has passed. This means that reversible → irreversible trades will have a long delay. Therefore, once several major tokens become reversible, other tokens face tremendous pressure to become reversible as well.
Decentralized Judicial System
The more ambiguous part of this dilemma involves the "quorum of judges." Who are these judges? How do they vote? How do they get rewarded?
These tasks ultimately depend on governance, specifically the individuals creating the ERC-20R/ERC-721R instances. However, in general, judges must randomly select cases from the transaction pool (using Ethereum's random beacon), and their rewards are independent of their voting decisions. Rewards come from the initial stake submitted by the victim along with the freeze request. The election of judges is best conducted secretly, not disclosed before ballots are submitted, to ensure judges can vote independently. Similarly, see the paper for further discussion.
Want to Learn More?
In our paper, we discuss more details, such as how to reduce the risk of dishonest judges, the impact on exchanges and mixers, related work, and in-depth explanations of the algorithms and implementations. If interested, we encourage you to take a look. We hope this will spark discussions about token reversibility, and some of you may find better reversible solutions to help reduce losses in the ecosystem.


























