Allowing arbitrage bots to attack Transit Swap, can technological neutrality exempt liability?
On the early morning of October 2, 2022, the on-chain swap protocol Transit Swap was attacked by hackers, resulting in the illegal theft of cryptocurrencies worth over $25 million from numerous user accounts to multiple hacker addresses, causing widespread panic in the crypto community. The Bitrace team intervened immediately and collaborated with the official investigation. It was found that the theft was due to a core code vulnerability in Transit Swap being exploited by hackers to gain unlimited authorization to user address assets, leading to the mass aggregation and transfer of user assets.
In addition to the large scale of victims and the amount of funds lost, some of the addresses directly involved in the attack were quite special. According to the Slow Mist security team, it was revealed for the first time that among the illegal beneficiaries, there were multiple frontrunners and attack imitators. How to characterize such special attack behaviors is clearly worth serious discussion.
1. What is a Frontrunning Bot?
Frontrunning is the act of getting ahead of a known future transaction before it occurs in the execution queue.
On the blockchain, frontrunning can be understood as the act of paying higher transaction fees to allow nodes to prioritize packaging their submitted transactions in order to seize a unique profit opportunity. For example, if someone discovers an obvious arbitrage opportunity for a token in a DEX liquidity pool, when they submit the arbitrage transaction to the blockchain network, it may be monitored by arbitrageurs, who can submit the same transaction with a higher fee, thereby achieving frontrunning. The result is that the arbitrageur takes the profit, while the original transaction submitter fails and wastes their transaction fee.
Currently, on-chain arbitrageurs have established many smart contracts (arbitrage bots) in the blockchain network to identify profitable transactions and automatically execute frontrunning.
2. Is On-Chain Frontrunning Illegal?
Lawyer Cao Shiyong from Beijing Yingke (Wuhan) Law Firm believes: Utilizing the public and transparent nature of blockchain networks, smart contracts that automatically execute frontrunning transactions can, to some extent, be considered a purely neutral technology. Many technology developers or providers believe that it is impossible to violate criminal law. However, the notion of "technology is innocent" is merely a wishful thinking of the technology side. Once technology is indiscriminately used for wrongdoing, the technology providers deploying it will also face significant criminal legal risks.
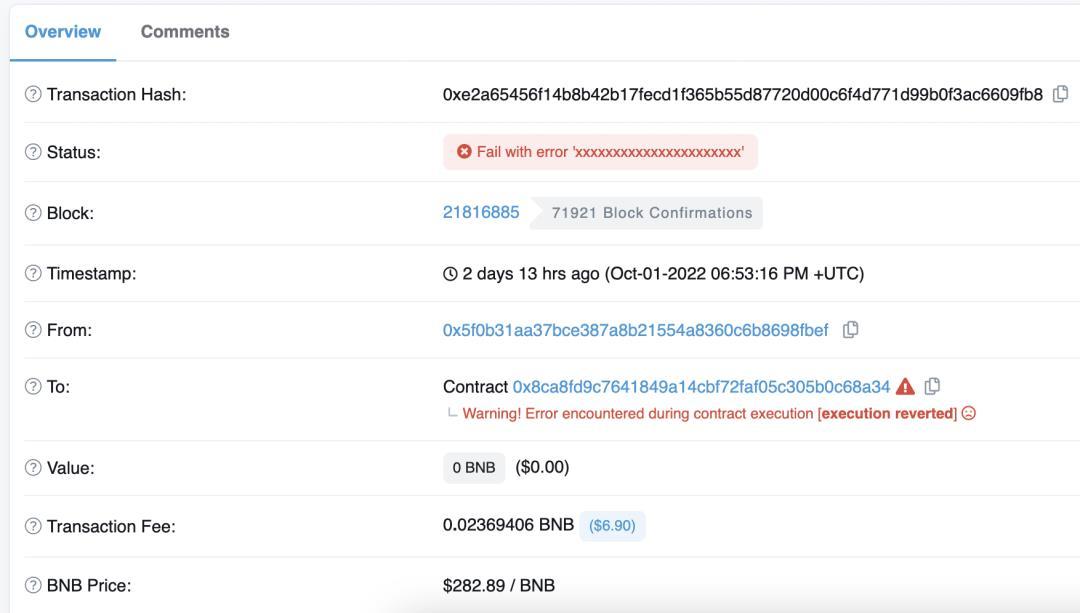
The failed theft transaction due to frontrunning
In this incident, a transaction initiated by the main attacker, intending to illegally acquire someone else's crypto assets, was automatically identified and executed in advance by the arbitrage program, resulting in over one million dollars' worth of $BUSD being transferred to the wallet address of the arbitrageur who deployed the arbitrage program.
The arbitrageur subjectively had indirect intent regarding the losses to others' crypto assets caused by the arbitrage program, and objectively allowed the bot's frontrunning behavior, ultimately leading to the secret transfer of others' assets to their own address. Its illegality is evident and may even violate our country's criminal law.
3. What Legal Interests are Infringed by Theft?
Lawyer Cao Shiyong believes: Cryptocurrencies are essentially a form of computer data, and they also possess certain property attributes. Illegally obtaining someone else's cryptocurrency infringes upon the security management order of computer information systems and property legal interests, constituting the crime of illegally obtaining computer information system data, as well as the crime of theft.
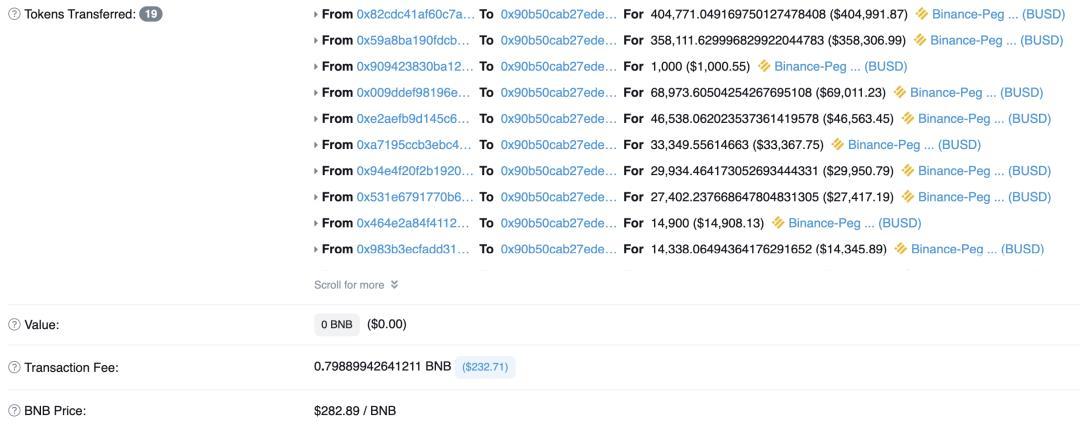
Damage caused by arbitrageurs' frontrunning
In the Transit Swap attack incident:
1) The computer data attributes and property attributes of the stolen cryptocurrency are indisputable; 2) Arbitrageurs/hackers/imitators intruded into others' computer information systems and modified the data stored in the systems; 3) Arbitrageurs/hackers/imitators repeatedly stole cryptocurrencies from unspecified targets, with serious circumstances.
It is clear that the elements of the crime of illegally obtaining computer information system data and theft have basically been met. Hackers, imitators, and arbitrageurs who illegally obtain others' crypto assets under direct or indirect subjective intent and refuse to return them afterwards are very likely to be regulated and punished by our country's criminal law.
Conclusion
The official announcement from Transit Swap stated that they hope all hackers, attack imitators, and frontrunning arbitrageurs involved in the incident can negotiate amicably based on the vulnerability bounty and refund rewards (5% of the related amount) and that addresses returning user assets by October 8 will not be regarded as attackers and will be exempt from legal regulation.
As of now, the hacker who stole the largest amount of funds has returned over $18.9 million of the stolen funds, accounting for over 80% of the amount they stole and about 65% of the total stolen amount. The Bitrace team also urges all good-faith acquirers to contact Transit Swap via email at service@transit.finance or through the on-chain address to jointly maintain blockchain security and trust.









