A Brief Analysis of zkPass's Paradigm Shift in Web3.0 Authentication
Author: Ethan, zkPass
In the era of the internet, we shape our identities through domain names, usernames, email addresses, and store information such as social relationships, reputation, and education in the centralized Web2 network world. At the same time, centralized Web2 entities can control how we access the external world and hold our credential data, which often becomes a lure for cybercrime.
In contrast, in the Web3 world, apart from on-chain addresses and corresponding on-chain activities, there is no way to grasp the true identity of others. If Web2 identity information could be integrated into Web3, Web3 users would have more "soul." However, the blockchain itself is isolated from real-world data, and 99.99% of social capital data resides in the internet of the real world. How can we bring this into Web3 to enrich the "soul" of Web3 users?
Decentralized Society, Privacy, Soul, zkPass
When introducing Web2 social identities into Web3, we also face issues of trust and privacy. The paper "Decentralized Society: Finding the Soul of Web3" mentions, "Privacy is a key challenge for DeSoc. On one hand, too many public SBTs may leak excessive information about the soul, putting it at risk of social control.
On the other hand, an excess of purely private SBTs may allow private communication channels to evade governance and the devaluation of social collaboration, leading to significant issues of incentive compatibility. Closely related to privacy issues is the problem of deception: souls may falsely represent their social connections while collaborating through private or sidestepped channels."
Based on this, zkPass explores using Multi-Party Computation (MPC) and Zero-Knowledge Proofs (ZKP) to address the privacy and cheating behaviors encountered in decentralized communities. Zero-Knowledge Proofs prove the characteristics of the soul by computing SBTs, while introducing multi-party computation technology (obfuscated circuits) for further expansion, making such tests doubly private: the prover does not need to reveal who they are to the verifier, and the verifier does not disclose their verification mechanism to the prover. Both parties compute together, only knowing the output result.
Current State of Traditional Identity Verification
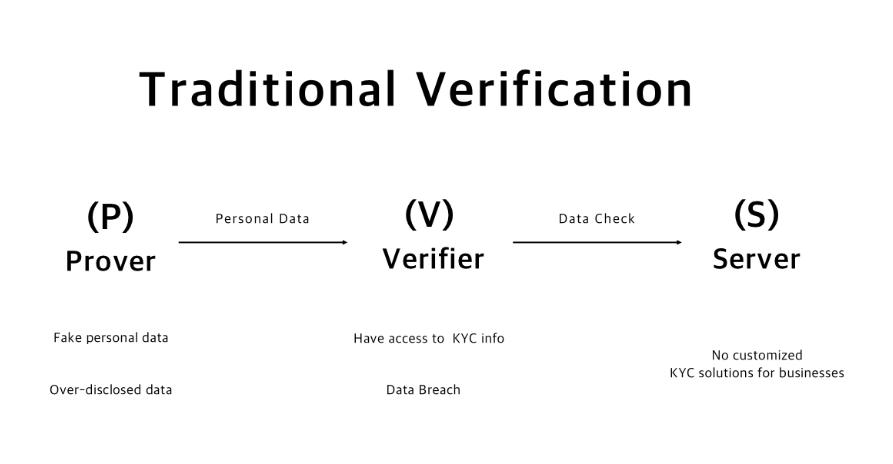
We can see that traditional identity verification generally involves a three-party relationship: Prover, the party proving their identity, typically understood as the ordinary user; Verifier, the party verifying the Prover's identity, which we can imagine as project teams, trading platforms, or KYC service platforms; and Server, the trusted data source used by the Verifier in the process of verifying the Prover's identity, which we can simply understand as Web2 data sources.
In the verification process, all three parties have certain issues to varying degrees. For example, user-side data falsification or excessive disclosure, the verifier holding all data may lead to data leaks or private sales of data, and Web2 data sources lack customizable services. How should we provide an ideal identity verification solution?
zkPass Identity Verification Protocol
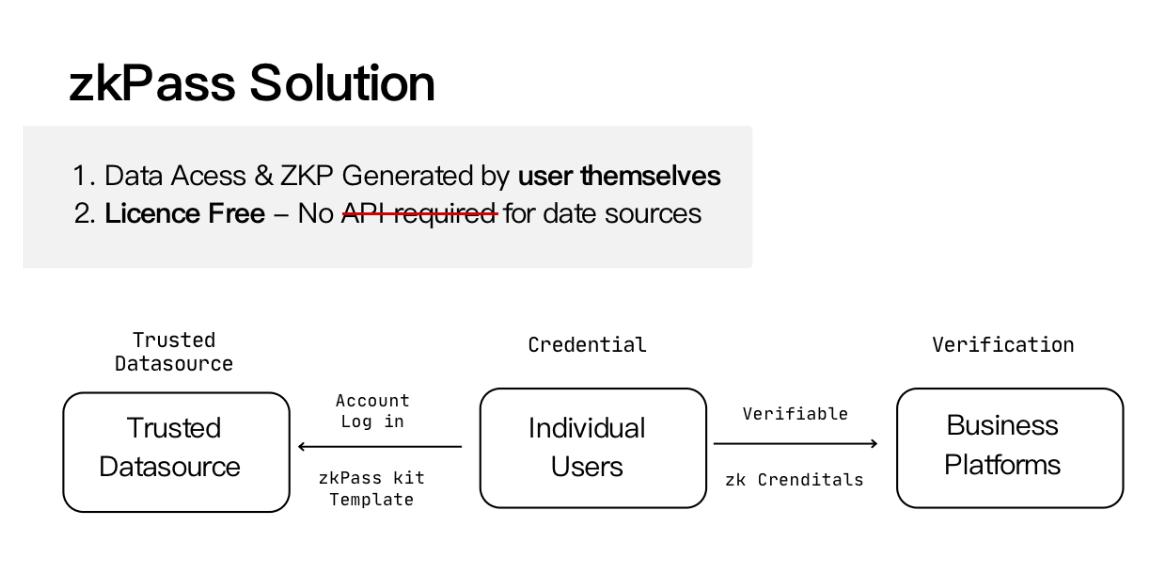
In zkPass, we rearrange the positions of the three parties, placing the user at the center of verification, and combine multi-party privacy computation with zero-knowledge proof technology to reconstruct the TLS protocol, introducing zk-SBT to rebalance privacy security and trust issues. Users do not need to trust any intermediary and can perform identity verification without access restrictions.
Specifically, throughout the verification process, individual users only need to directly access Web2 data sources through their authorization tokens, generate Zero-Knowledge Proof zk-SBT, and then provide the locally generated Zero-Knowledge Proof to the enterprise platform for verification. Thus, even if the platform verifies successfully, it does not know any real identity information about the user other than the yes or no result. This can solve the risk of privacy leakage in a decentralized society while preventing users from falsely representing their social capital. The overall technical architecture is shown in the figure below:
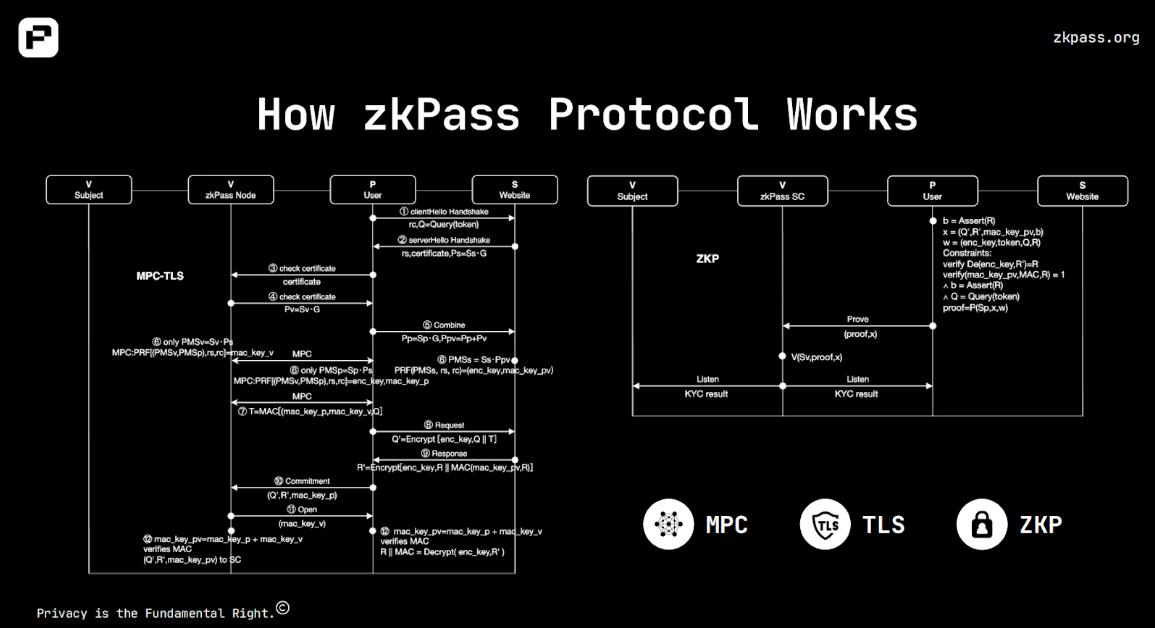
From the above content, we can summarize that zkPass has the following characteristics:
1) Privacy
Unlike traditional identity identification systems, users do not need to submit issued and regulated documents or identification to centralized third parties; the verification process is entirely cryptographically encrypted with no risk of information leakage.
2) Scalability
Traditional identity verification types are relatively singular; different verification needs require business dealings with different products. For example, every time a large KYC service provider adds a certification service, it must engage in lengthy business negotiations with Web2 data providers. zkPass reconstructs the TLS (Transport Layer Security) protocol, allowing 99.9% of Web2 and Web3 data sources to be accessed without entry, without API authorization and calls, thus completing data acquisition. It is widely adaptable to data sources, has strong protocol compatibility, and can provide one-stop customized services based on needs (such as verifying legal identity, educational credentials, and asset proof simultaneously).
3) Verifiability
Social capital such as personal educational certificates, work history, bank credit, affiliation, and asset balance can be traced back through verified zk credentials, ensuring their authenticity, and the credentials can be reused.
4) Anti-Fraud
Directly seek the required verification information corresponding to the fields from the data source and apply encryption algorithms. The user, as the prover, holds the confidentiality key and data integrity key shares, while the enterprise verifier holds the other half of the data integrity key. Here, the data confidentiality key is used to encrypt and decrypt information, which the enterprise verifier does not hold, so they cannot access user information. The data integrity key is held in halves by both parties, meaning the user knows the identity information that should belong to them but cannot tamper with it; otherwise, it will be detected, ensuring that users cannot commit data fraud.
zkPass Use Cases and Outlook
zkPass proposes a new Web3.0 verification solution based on multi-party secure computation and zero-knowledge proof, aiming to "Verify Everything." As infrastructure, zkPass addresses existing issues of online digital identity security, privacy, interoperability, and ownership while promoting better development of Web3 applications.
Unsecured Lending/Loan Rate Discounts
The traditional financial ecosystem supports various forms of unsecured loans but relies on centralized credit ratings to assess borrowers' creditworthiness, and these borrowers have little incentive to share their credit records.
For example: A certain DeFi lending protocol holds a "loan rate discount" event, where borrowers can verify centralized credit rating agencies to obtain loan rate discounts. After initiating a verification request through zkPass, borrower Bob can log into his Alipay account, enter his account password to obtain his Sesame Credit score, and generate a credential produced by zero-knowledge proof (for example, Sesame score > 800, eligible for a 5% loan rate discount). If applying for unsecured loans or loan rate reductions from this DeFi protocol, the only result obtained by the DeFi protocol is whether the Sesame score is greater than 800.
Educational Credentials
The Super Rare platform pursues high-quality artworks, so it has high entry requirements for artists; only invited artists can join the network to create artworks.
For example: Alice uses the zkpass platform's educational verification module to log into the educational website and generate a zero-knowledge proof for the Paris School of Fine Arts. When filling out the application, she can submit it to the platform, improving the efficiency of the platform's background checks while avoiding excessive exposure of other graduation information.
Of course, zkPass can verify not only individuals' identities but also educational credentials, flight records, bank balances, work experience, etc. On the Web2+Web3 internet, any personal data you can access can generate zero-knowledge proofs, creating verifiable zk SBTs. Use cases involve user acquisition, existing user activation, as well as anti-fraud, anti-scam, anonymous voting, protection against witch attacks, zkKYC, background checks, educational verification, proof of participation, and more—all within zkPass.
Conclusion
As a pioneer in the evolution from Web2 to Web3, zkPass protects users' personal digital sovereignty while providing a more transparent, democratic, private, and trustworthy information and data exchange solution, better promoting the digital economy and creating new blockchain application scenarios.
Moreover, zkSBT offers a wide range of applications to optimize the current use of Web3. It can be said that on the road to jointly building a decentralized society, zkPass is a very important identity verification infrastructure.








