The clip was clipped by the clip, analyzing how MEV bots have become hacker cash machines
Author: Qin Xiaofeng, ODAILY Planet Daily
This afternoon, crypto user 3155.eth posted that some top MEV bots are becoming targets for hackers, with their "sandwich attack" transaction modules being replaced, resulting in losses exceeding $20 million. This could become a major turning point for the entire MEV ecosystem.
Odaily Planet Daily found that the hack occurred about 10 hours ago (Ethereum block height 16964664). The hacker used eight wallet addresses (with original funds from Kucoin) to attack five MEV bots, which are:

According to on-chain analysis firm Lookonchain, the total loss is currently about $25.2 million, mainly involving five major cryptocurrencies, specifically: 7461 WETH ($13.4 million), $5.3 million USDC, $3 million USDT, 65 WBTC ($1.8 million), and $1.7 million DAI.
Before understanding this attack, we first need to know what MEV is and how MEV performs sandwich attacks.
MEV stands for "Miner Extractable Value" or "Maximal Extractable Value." Miners or validators have the ability to order transactions within a block, allowing certain transactions to be prioritized. Typically, some MEV bots pay high GAS fees to gain priority in transaction processing from validators, profiting from price differences; of course, there are also validators who directly participate without paying high GAS fees but prioritize packaging their own transactions.
The benign forms of MEV are arbitrage and liquidation, while the "sandwich attack," criticized by DeFi players, involves "cutting in line" to buy assets before the original transaction and then selling them at a higher price to the original buyer. Generally, a bundle can be split into three transactions: 1) a large buy, 2) the victim's transaction; 3) a large sell.
Security company Certik told Odaily Planet Daily that the reason this hacker attack was successful is that the hacker became a validator, allowing them to see the original information of the MEV bots' bundles, thus replacing the second step with their own transaction and exchanging cheap tokens for the MEV bots' funds.
"In order to extract transactions, validators need access to certain specific information, just like in a public mempool, where malicious validators can obtain bundle information. Typically, flashbot validators are reliable and have passed verification (such as completing KYC on MevHUB) to increase trustworthy data sources. However, in this incident, the malicious validator obtained the necessary information, allowing them to act ahead of the MEV bots."
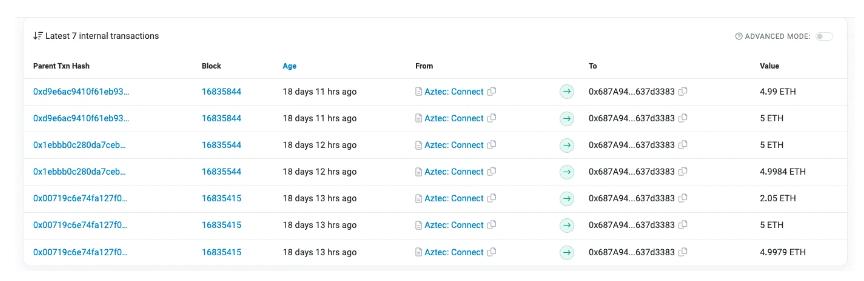
Odaily Planet Daily checked on-chain data and found that Ethereum block 16964664 belongs to Slot 6137846, proposed by validator 552061. The validator's 32 ETH funds were transferred by the hacker over 18 days through the privacy protection protocol Aztec Network, deposited into an address starting with 0x873f73, as shown below:
After completing the preliminary preparations, the attacker would test whether the MEV bots would front-run transactions. For example, in the image below, we can see the attacker testing the MEV bots with 0.04 WETH, enticing them to engage in front-running arbitrage; they found that there were indeed MEV bots monitoring the ETH/Threshold pool on Uniswap V2, and they would use all their funds for arbitrage. During this time, the hacker was also testing whether MEV was using their own validator to produce blocks.
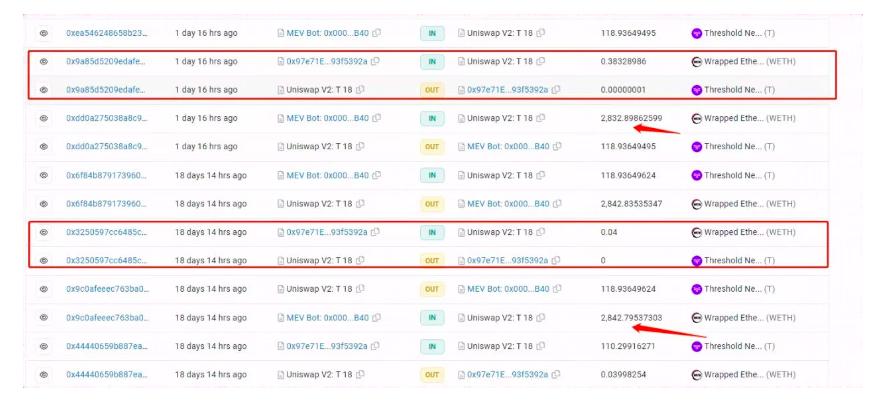
After successful testing, the hacker would use a large amount of tokens pre-exchanged in Uniswap V3 to perform exchange operations in the low liquidity V2 pool, enticing the MEV to use all their WETH to front-run the purchase of worthless Threshold tokens; then they would exchange the Threshold tokens for all the WETH invested by the MEV bots. Since the WETH used for front-running by the MEV had already been exchanged out by the attack transaction, the MEV bots' attempts to exchange back for WETH would fail.
In addition to the aforementioned Threshold tokens, the hacker also manipulated seven other addresses to manipulate the prices of seven tokens in the Uniswap V2 pool, including AAVE, STG, SHIB, CRV, BIT, UNI, and MKR, to achieve profits, as shown below:

Security company Beosin believes that the hacker's success can be attributed to three main reasons: first, MEV bots use all their funds for arbitrage in low liquidity pools, lacking risk control; second, the liquidity in the V2 pool is low and manipulated by the hacker; third, they have validator node permissions, allowing them to modify bundles.
This attack incident has also served as a wake-up call for MEV seekers. To avoid "sandwich attacks," they need to adjust their trading strategies in a timely manner and choose "reliable" validators with a history of verification. Currently, the related funds have gathered in the following three addresses, awaiting the next steps, and Odaily Planet Daily will continue to monitor the subsequent developments:
0x3c98d617db017f51c6a73a13e80e1fe14cd1d8eb;
0x5B04db6Dd290F680Ae15D1107FCC06A4763905b6;
0x27bf8f099Ad1eBb2307DF1A7973026565f9C8f69.










