Cryptography Knowledge Pyramid, let's see which level you are on
Original Author: pastry, Co-founder of The Bakery
Original Translation: 0x137, Rhythm
This article summarizes the views of pastry, co-founder of The Bakery, on personal social media platforms, and Rhythm BlockBeats translates and organizes them as follows:
The blockchain and cryptocurrency world is composed of a complex knowledge system, which I divide into five layers of knowledge, gradually unveiling the iceberg of cryptocurrency.
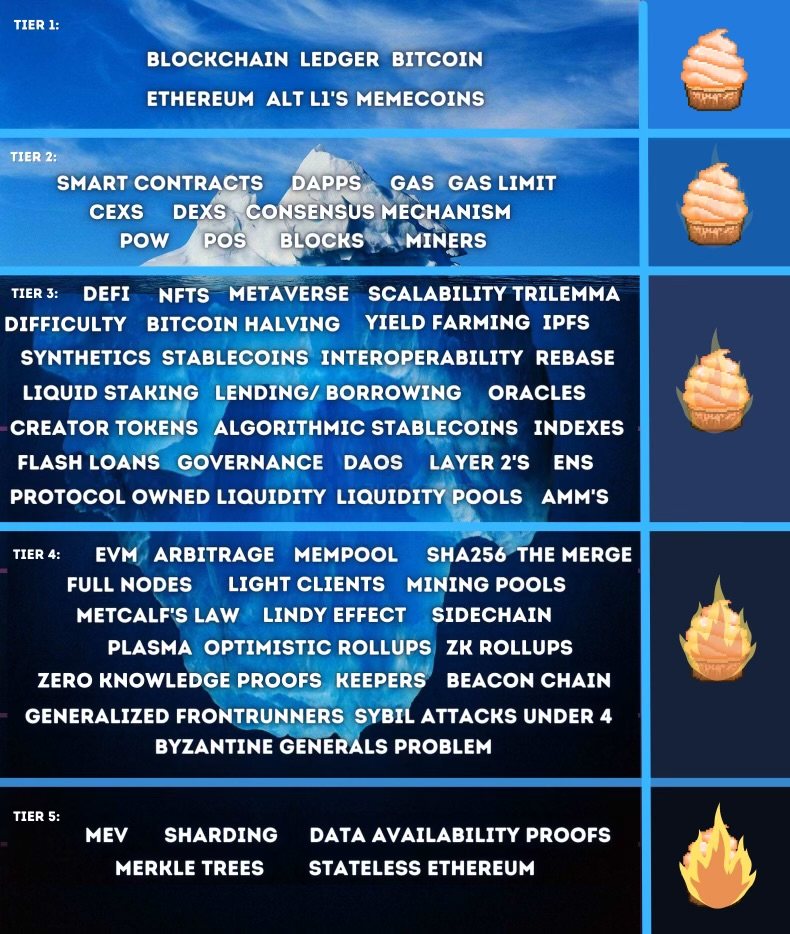
Entry Level: Topics Familiar to Most Beginners
1. Blockchain
A distributed, decentralized public ledger existing on the network.
2. Ledger
An immutable database used to store network blocks.
3. Bitcoin
The first generation of digital currency created by Satoshi Nakamoto.
4. Ethereum
A general platform aimed at surpassing digital currency through the use of smart contracts and dApps.
5. Public Chain
A layer of blockchain that adopts alternative methods to solve the scalability trilemma.
6. Meme Coin
Cryptocurrency tokens that originate from internet memes or have other humorous characteristics, such as Dogecoin, Shiba Inu, etc.
Second Level: Topics Familiar to Most Crypto Natives
1. Smart Contract
A program that runs when specified conditions are met, used for the automatic execution of agreements.
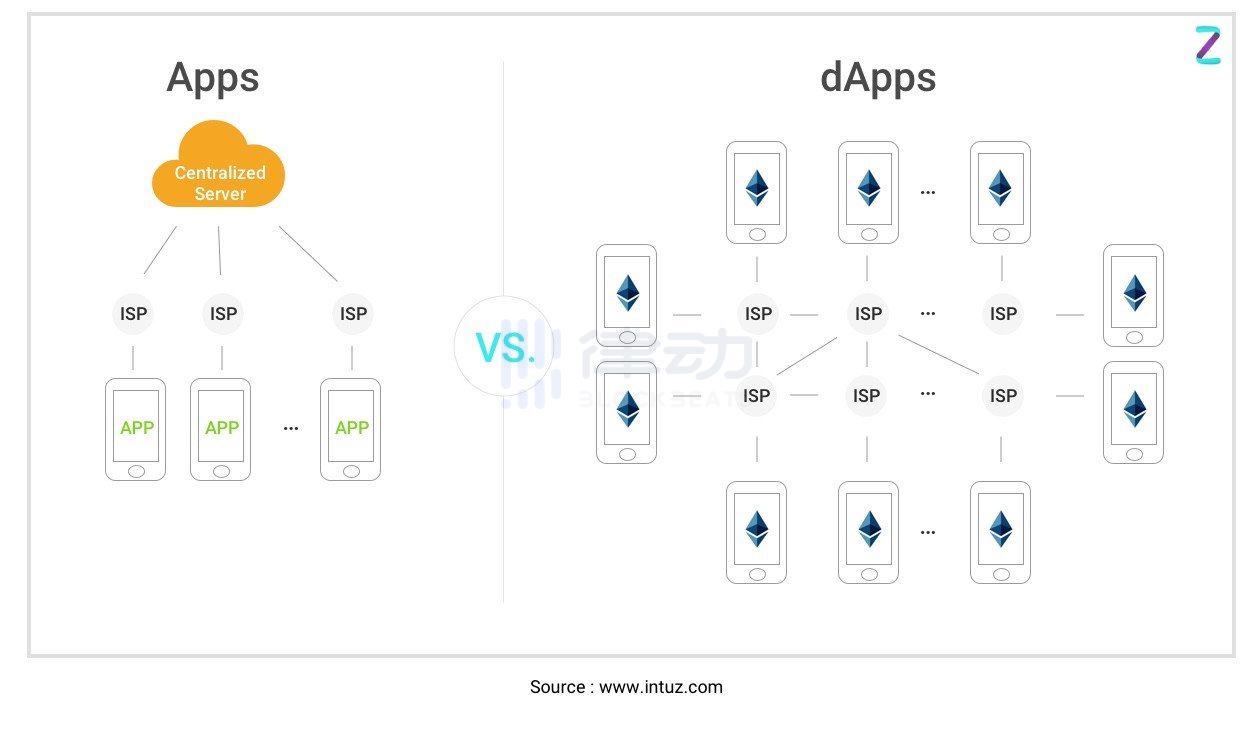
2. dApps
Applications that provide similar functionalities to regular applications but run on a peer-to-peer network.
3. Gas
In public chains like Ethereum, gas is a unit of measurement that describes the computational power required to perform specific operations on the network.
4. Gas Limit
The maximum amount of gas a user is willing to spend on a specific transaction.
5. CEX
Centralized exchanges that act as trusted intermediaries for buying and selling cryptocurrency tokens, belonging to custodial institutions.
6. DEX
Decentralized exchanges that allow users to trade directly on-chain in a peer-to-peer manner, and are non-custodial.

7. Consensus Mechanism
A fault-tolerant mechanism that facilitates agreement among distributed nodes on a single state of the network. The consensus mechanism ensures that all nodes are synchronized with each other and agree on transactions, which are then added to the blockchain.
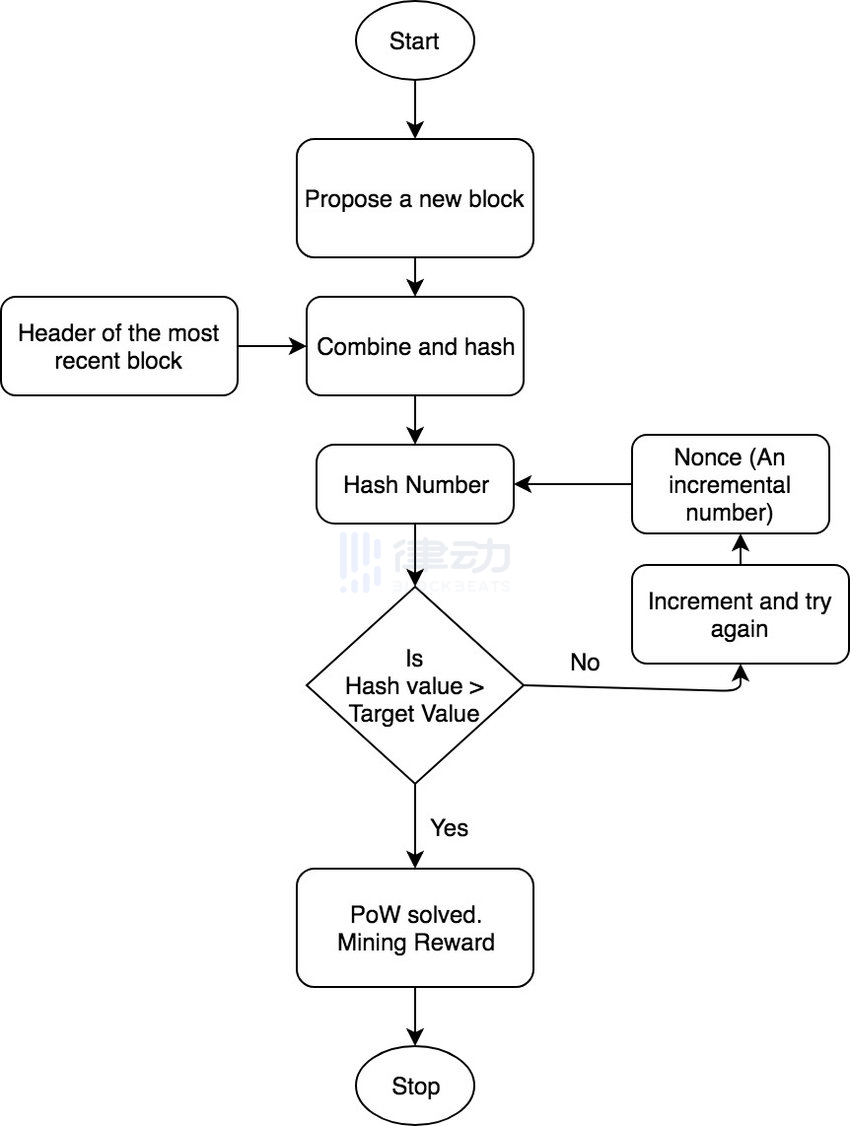
8. PoW
Proof of Work is a type of consensus mechanism that requires network members known as "miners" to expend effort solving arbitrary mathematical problems to validate transactions and add them to the blockchain.
9. PoS
Proof of Stake is another consensus mechanism that requires users to stake tokens to become validators in the network, with responsibilities similar to those of miners in the Proof of Work mechanism.
10. Block
A data structure in the blockchain used to permanently record and store transaction data on the chain.
11. Miner
A computer or group of computers responsible for adding new transactions or validating blocks produced by other miners.
Third Level: Topics Familiar Only to Experienced Crypto Investors
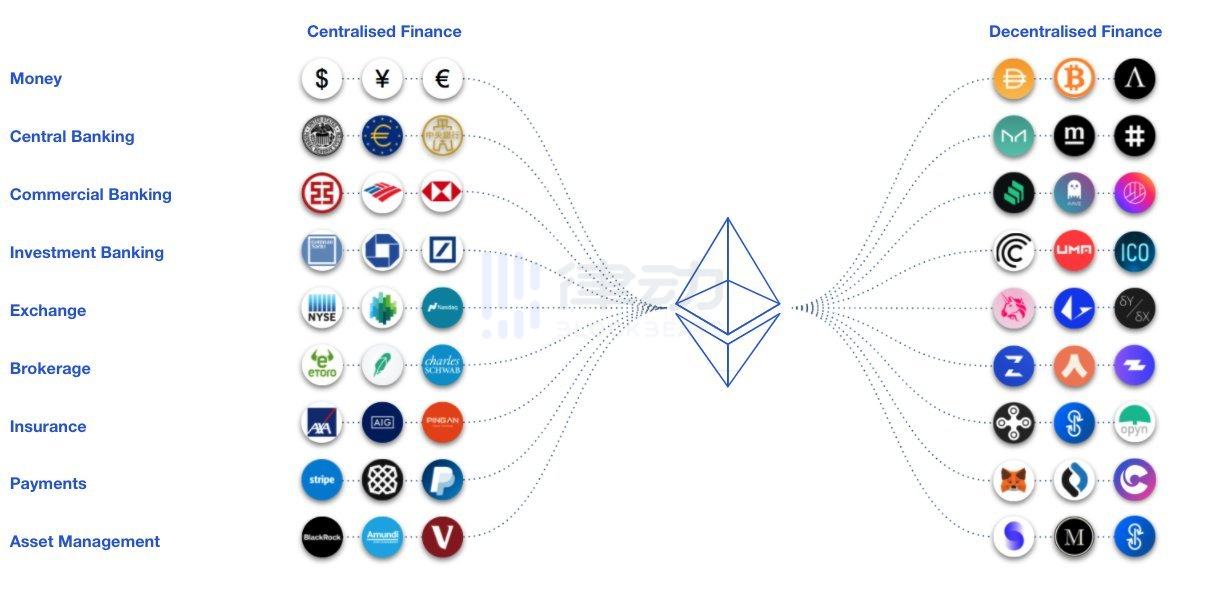
1. DeFi
Decentralized Finance uses smart contract technology on the blockchain to provide financial tools that do not rely on intermediaries such as brokers, exchanges, or banks.
2. NFT
Non-Fungible Token is a non-interchangeable data unit stored on the blockchain, which can be sold or traded. The types of NFT data units can involve digital file forms such as photos, videos, and audio.
3. Metaverse
The Metaverse is a complex, large-scale, and interoperable real-time rendered 3D virtual world network that allows an unlimited number of users to experience it synchronously and continuously.
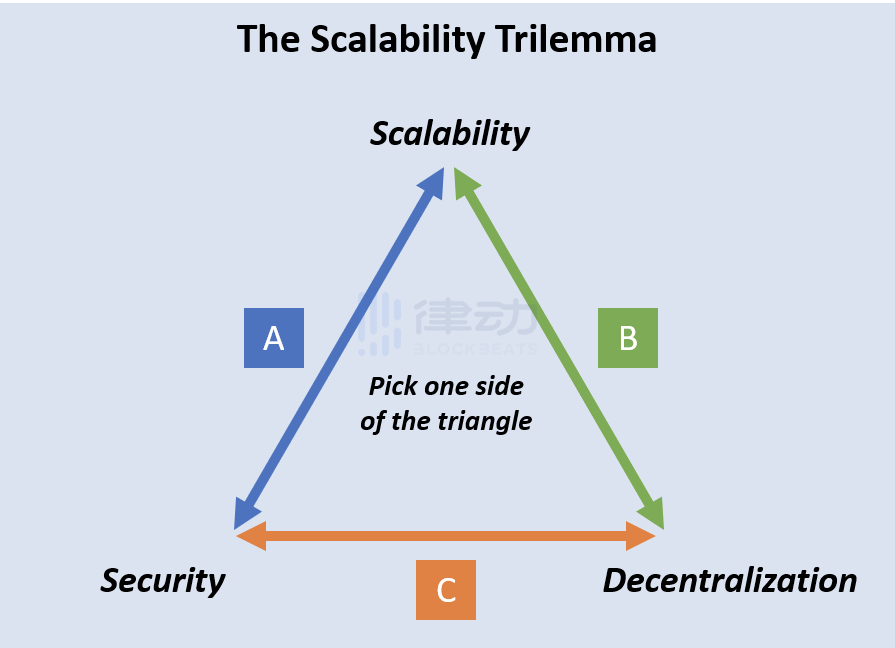
4. Scalability Trilemma
The scalability trilemma proposed by Ethereum founder Vitalik Buterin points out that it is inevitable to make trade-offs among decentralization, security, and scalability; you can cater to one or two properties but cannot accommodate all three simultaneously.
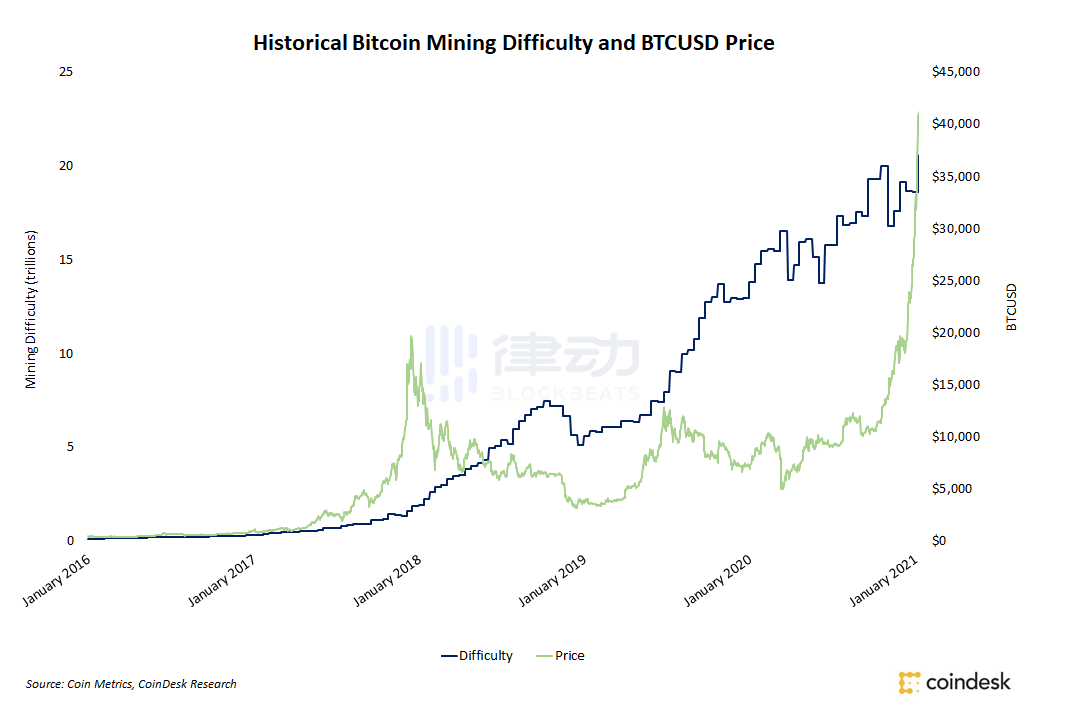
5. Block Difficulty
Block difficulty is one of the most important aspects of Proof of Work mining, derived from the network hash rate, used to determine how quickly miners can validate blocks.
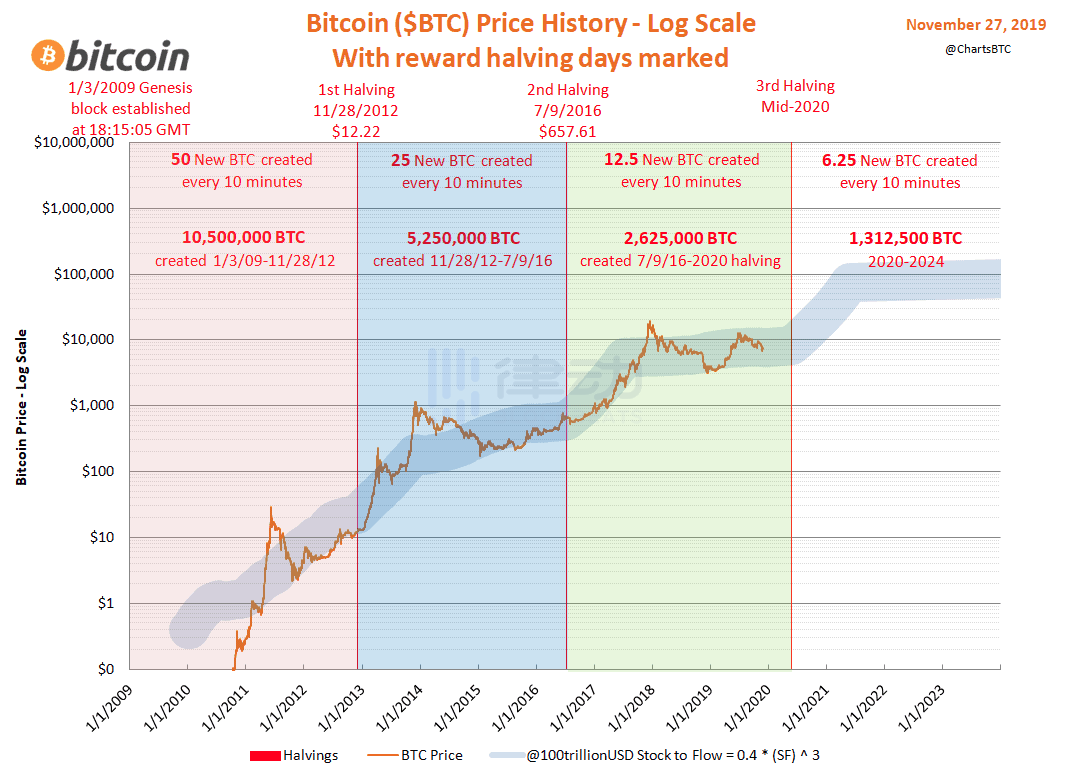
6. Bitcoin Halving
Bitcoin undergoes a "halving" event every four years, reducing the miner's reward by half to decrease the number of Bitcoins entering circulation, aiming to tighten supply until the total of 21 million BTC is mined.
7. Layer 2
Layer 2 refers to auxiliary frameworks or protocols built on existing blockchain systems, primarily aimed at solving transaction speed and scalability issues faced by the underlying network.
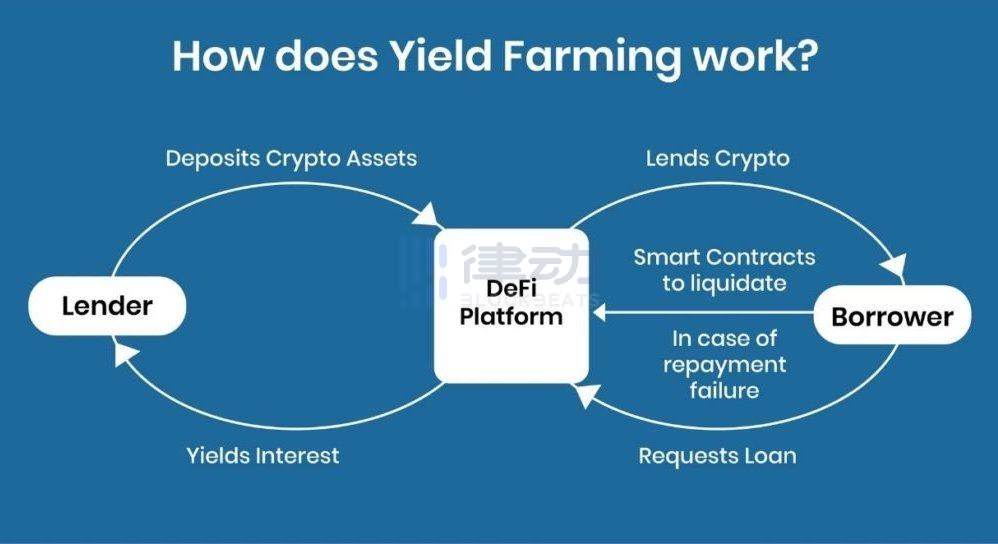
8. Yield Farming
Yield Farming is akin to earning annual interest by depositing money in a bank. Essentially, Yield Farming is the process where liquidity providers lock their assets in liquidity pools and earn incentives in the form of transaction fees or governance token emissions.
9. AMM
Automated Market Maker is an underlying protocol that supports DEX, allowing assets to be traded permissionlessly using liquidity pools instead of traditional buy-sell markets.
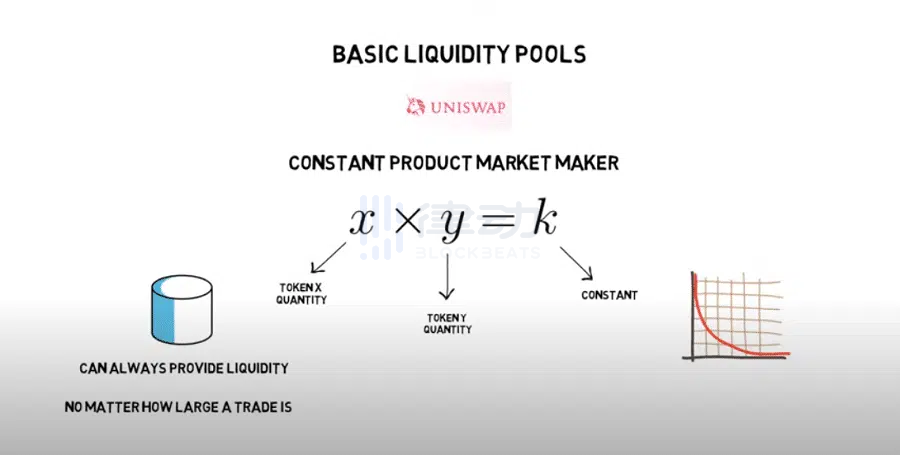
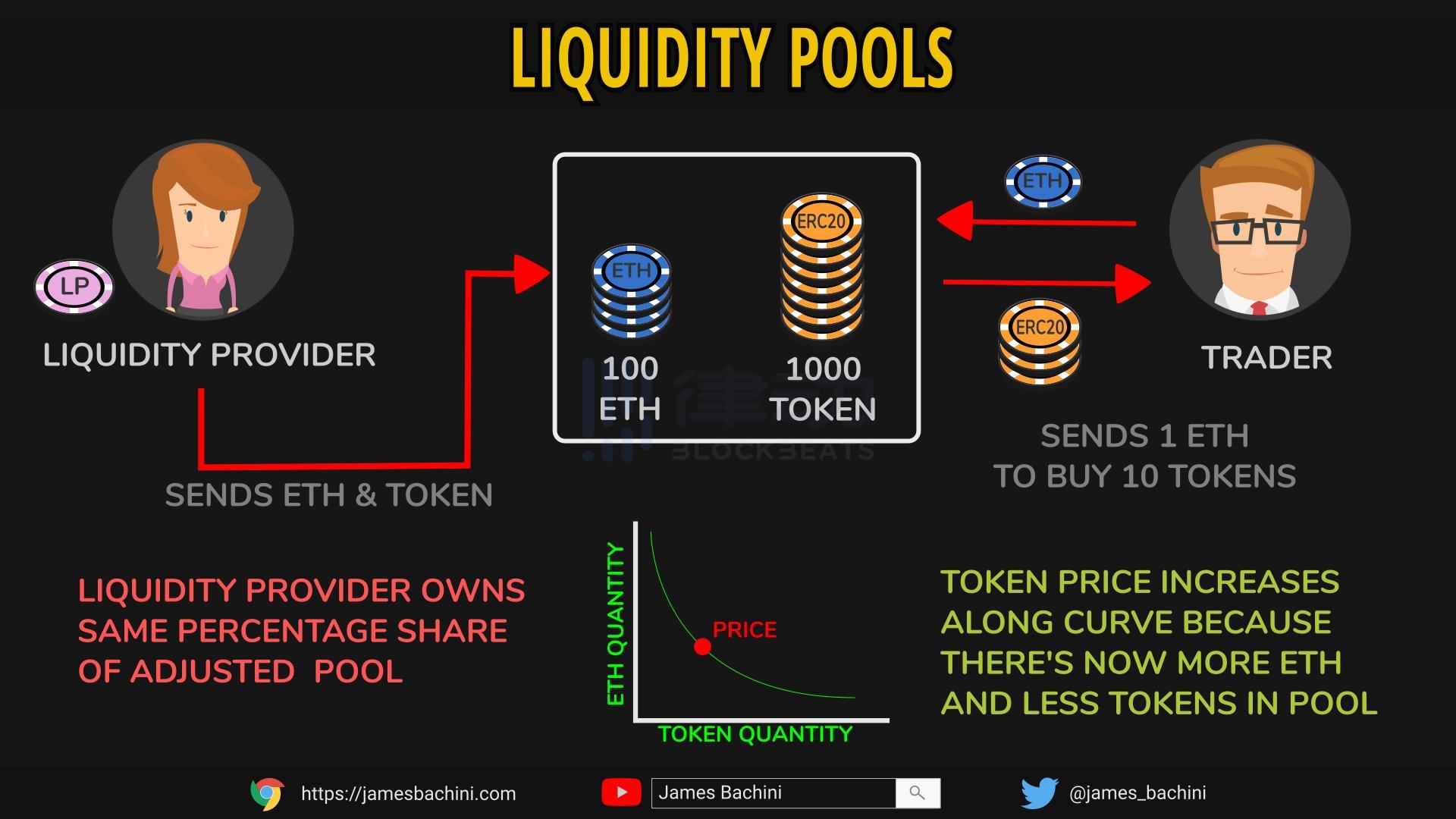
10. Liquidity Pool
A liquidity pool is a crowdfunding token pool locked in a smart contract to support trading on decentralized exchanges. For example, when users trade using liquidity pool protocols like Uniswap, they can complete transactions without needing to match buy and sell orders.
11. Crypto Lending
Crypto lending is similar to the concept of traditional lending, where crypto token lenders can lend their idle assets to borrowers, who in turn pay interest on the lender's assets.
12. Synthetic Assets
Synthetic assets are essentially tokenized derivatives. In traditional finance, derivatives represent stocks or bonds that traders do not own but wish to buy or sell, while crypto synthetic assets allow investors to trade any crypto asset on the blockchain.
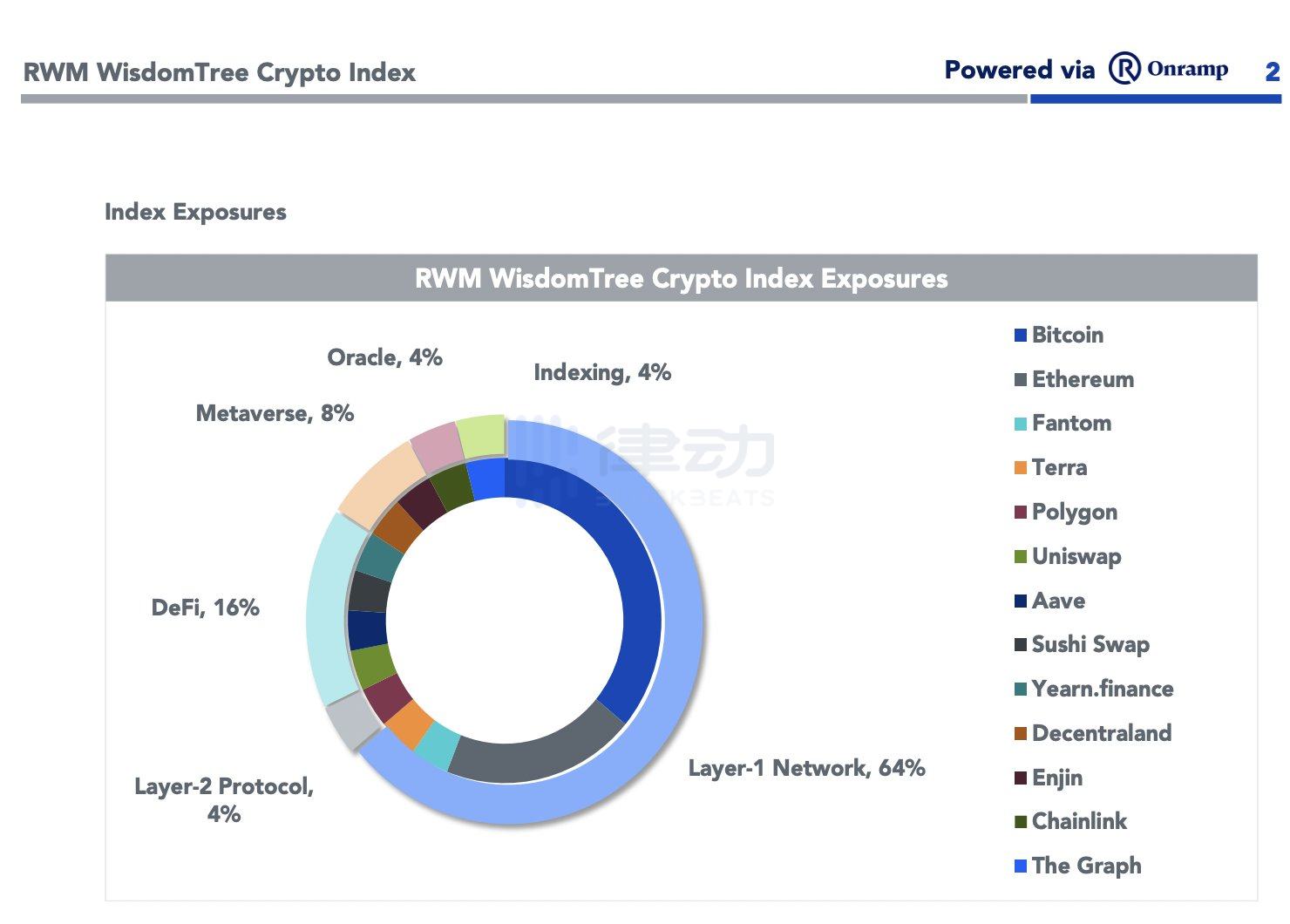
13. Crypto Index
A crypto index is a way to gain exposure to a basket of different crypto assets, with each index composed of various crypto assets. These indices allow investors to gain exposure to multiple tokens without needing to purchase them individually.
14. Oracle
A blockchain oracle is an entity that connects the blockchain to external systems, allowing smart contracts to execute specific code based on real-world inputs and outputs.
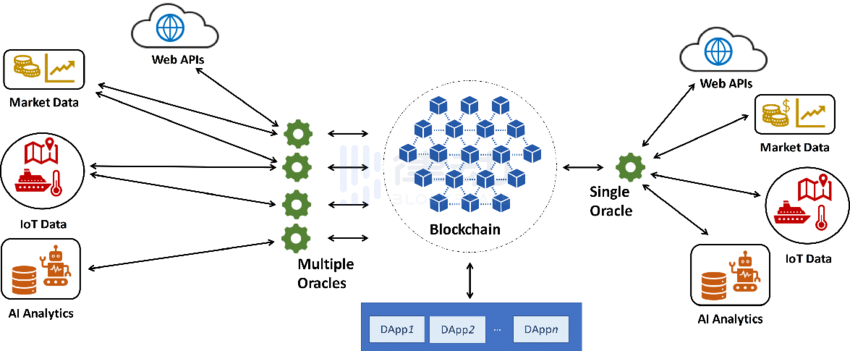
15. Governance
The governance structure relied upon by decentralized networks in the absence of a central authority. Blockchain governance typically employs various mechanisms to determine the direction of project development and ongoing updates to ensure the network operates efficiently.
16. Stablecoin
A cryptocurrency token pegged to other cryptocurrencies, fiat currencies, or exchange-traded commodities, with algorithmic stablecoins aiming to achieve price stability and asset circulation supply. In other words, the algorithms used by algorithmic stablecoins ensure that more tokens are issued when prices rise and buy back from the market when prices fall, thus maintaining price stability.
17. Flash Loan
Flash loans are a new type of low-collateral loan that allows users to instantly obtain crypto loans without providing collateral.
18. Arbitrage
Crypto arbitrage is a trading strategy where investors exploit slight price differences of digital assets across multiple markets or exchanges, buying assets on one exchange and immediately selling them on another at a higher price.
19. Creator Token
Creator tokens allow creators, social influencers, athletes, musicians, etc., to launch their own crypto tokens to monetize their communities and expand their audience.
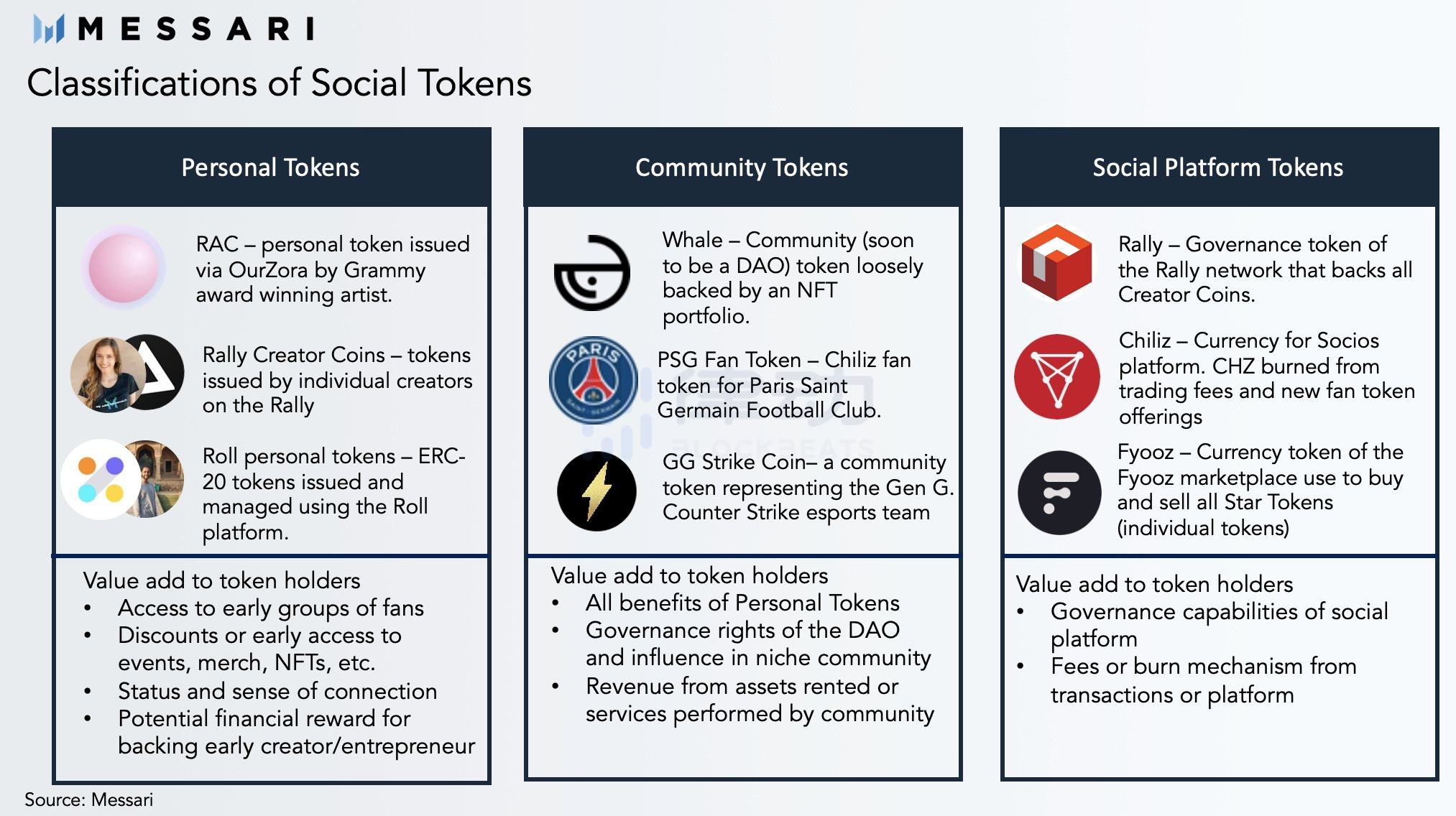
20. Protocol Owned Liquidity
Protocol Owned Liquidity is a new method of providing liquidity pioneered by Olympus DAO, which does not rely on incentivizing liquidity providers but instead sells discounted tokens to buyers in exchange for tokens that serve as collateral, forming part of the protocol treasury.
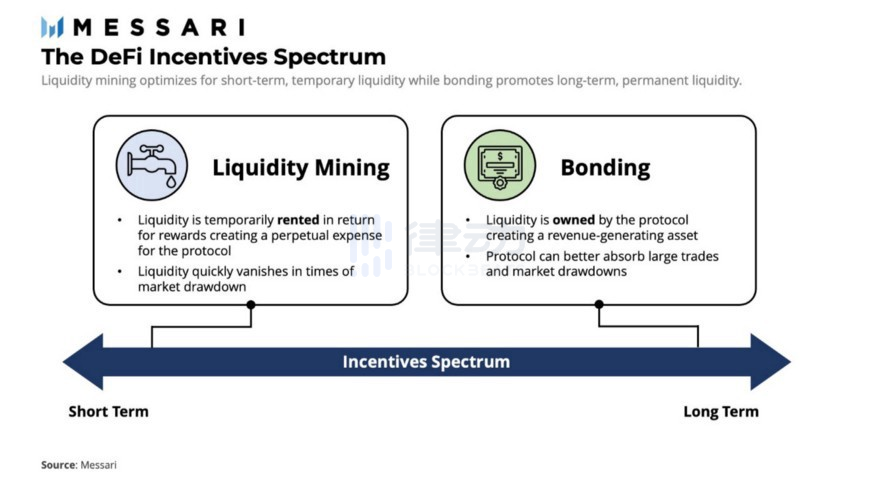
21. Liquid Staking
Liquid staking allows token holders to stake their assets and receive liquidity derivatives that can be used across various dApps. With liquid staking, ETH 2.0 stakers can stake their Ethereum while maintaining liquidity.
22. DAO
Decentralized Autonomous Organization is an organization represented by rules encoded in computer programs that are transparent, controlled by the organization's members, and not influenced by central power.
23. Interoperability
Blockchain interoperability refers to the ability of different blockchain networks to exchange and utilize data to move unique types of digital assets between their respective blockchains.
24. IPFS
InterPlanetary File System is a peer-to-peer network protocol used for storing and sharing data in a distributed file system. IPFS uses content addressing to uniquely identify each file in a global namespace that connects all computing devices.
25. ENS
Ethereum Name Service is a domain name lookup service built on Ethereum that allows crypto users to convert their machine-readable addresses into human-readable addresses; you can think of it as a nickname generator for public Ethereum addresses.
Fourth Level: Formally Delving into the Rabbit Hole
1. EVM
Ethereum Virtual Machine is a software platform that developers can use to create dApps on Ethereum; it is where all Ethereum accounts, smart contracts, and the entire state history of Ethereum reside.
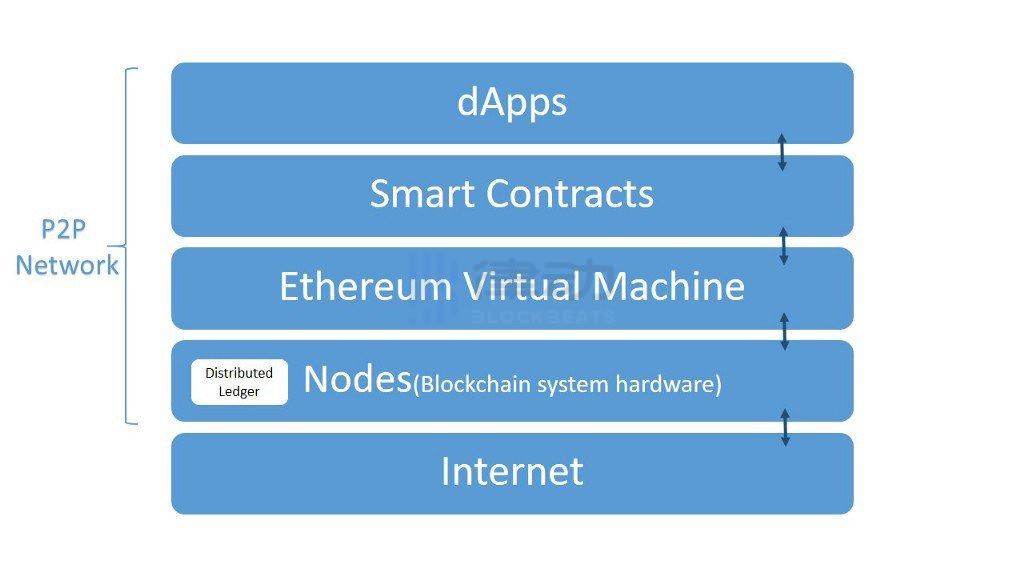
2. Mempool
In blockchain terminology, the mempool is the waiting area for transactions that have not yet been added to a block and are still unconfirmed.
3. Frontrunners
Frontrunners are bots on Ethereum that constantly scan the mempool for profitable transactions. Frontrunners participate in priority gas auctions (PGA) with other bots to gain priority for their transactions in a block.
4. Byzantine Fault Tolerance
In blockchain, Byzantine Fault Tolerance, derived from the Byzantine Generals Problem, refers to the network's ability to tolerate faults when validating nodes fail and run inconsistently.
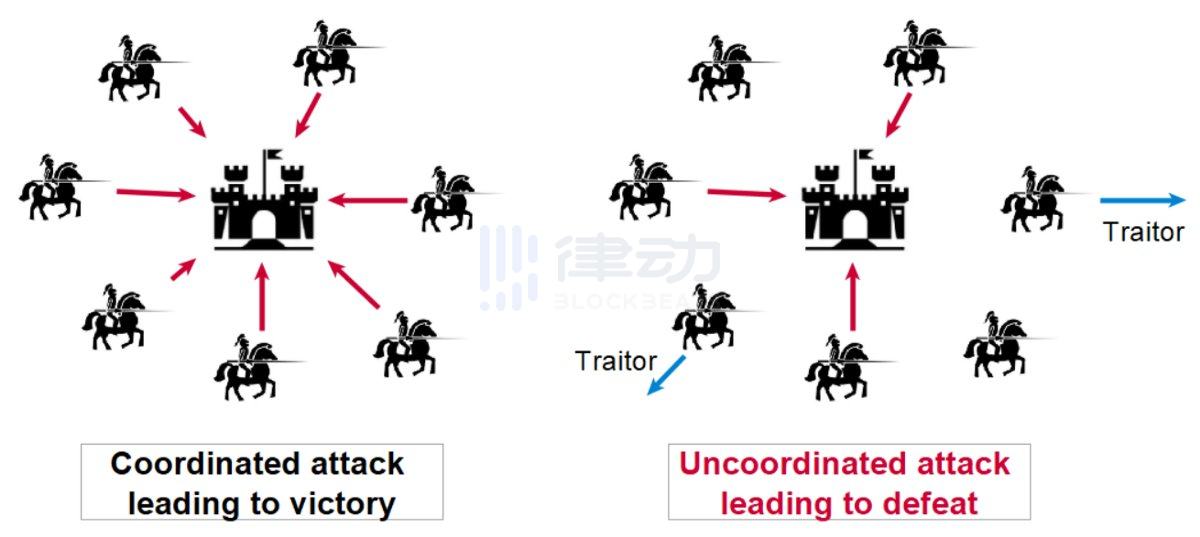
5. Sybil Attack
A Sybil Attack is a type of attack on a computer where an attacker creates a large number of fake identities to gain disproportionate influence over the network and undermine the server's reputation system.
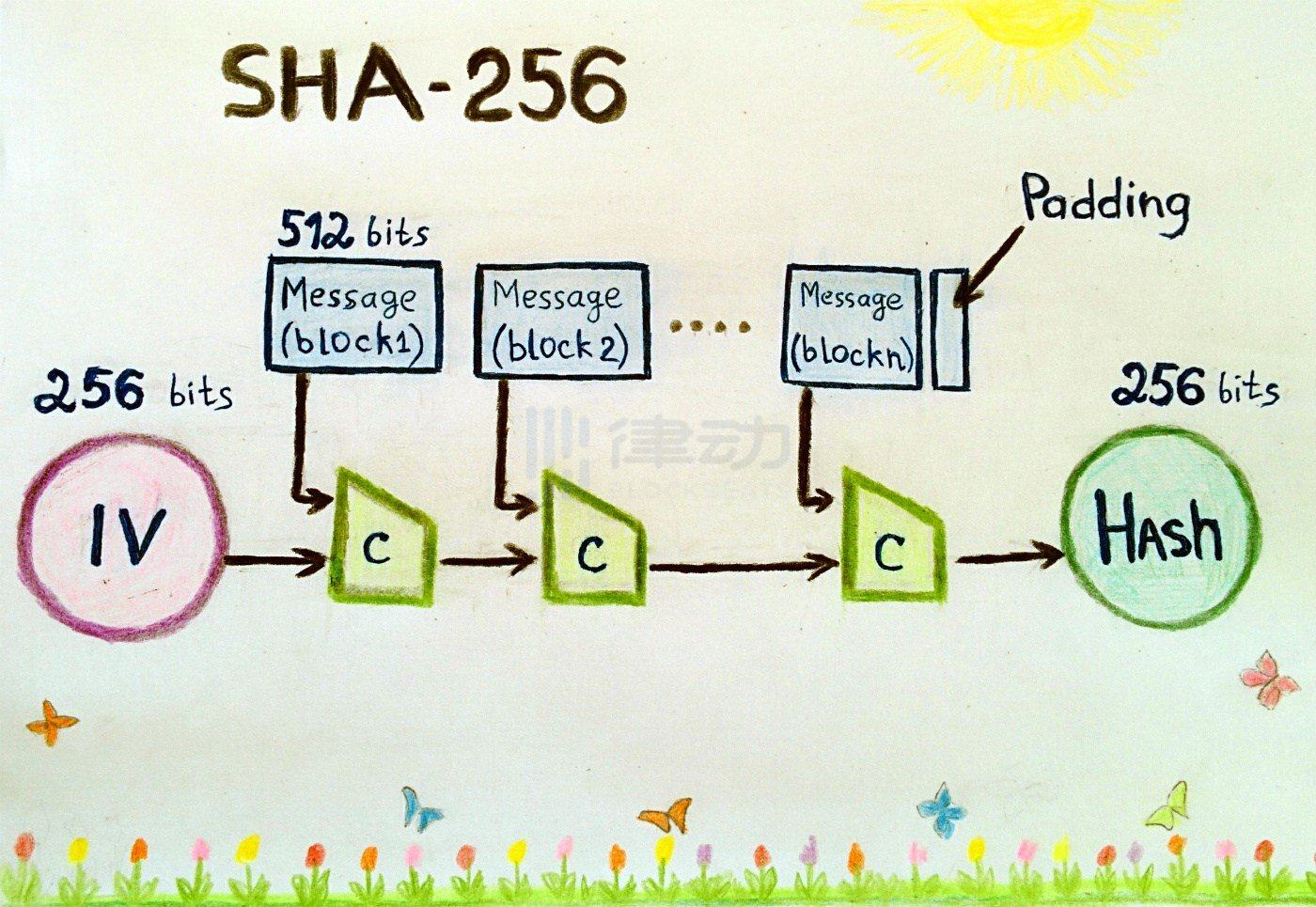
6. SHA-256
SHA-256 stands for 256-bit Secure Hash Algorithm, used to enhance cryptographic security. Cryptographic hash algorithms produce irreversible and unique hashes; the larger the number of possible hashes, the smaller the chance that two values will create the same hash.
7. Full Node
A full node is a node that downloads and checks every transaction in the blockchain for validity, requiring significant resources and hundreds of GB of disk space, but they are the most secure nodes as they are not easily deceived by invalid transaction blocks.
8. Light Client
If a computer does not have enough resources to run a full node, it can run a light client. Light clients do not download or verify any transactions; they only verify block headers and assume that the block contains only valid transaction records.
9. Metcalfe's Law
Metcalfe's Law states that the value of a network is proportional to the square of the number of nodes in the network. For example, if a network has 10 nodes, its value is: 10x10=100.
10. Lindy Effect
The Lindy Effect is a theoretical phenomenon where the future expected lifespan of some durable things (such as technology or age) is proportional to their current age.
11. Sidechain
A sidechain is a separate blockchain that is connected to its parent chain using a two-way peg. The two-way peg allows for asset swaps between the parent chain and the sidechain at a predetermined rate.
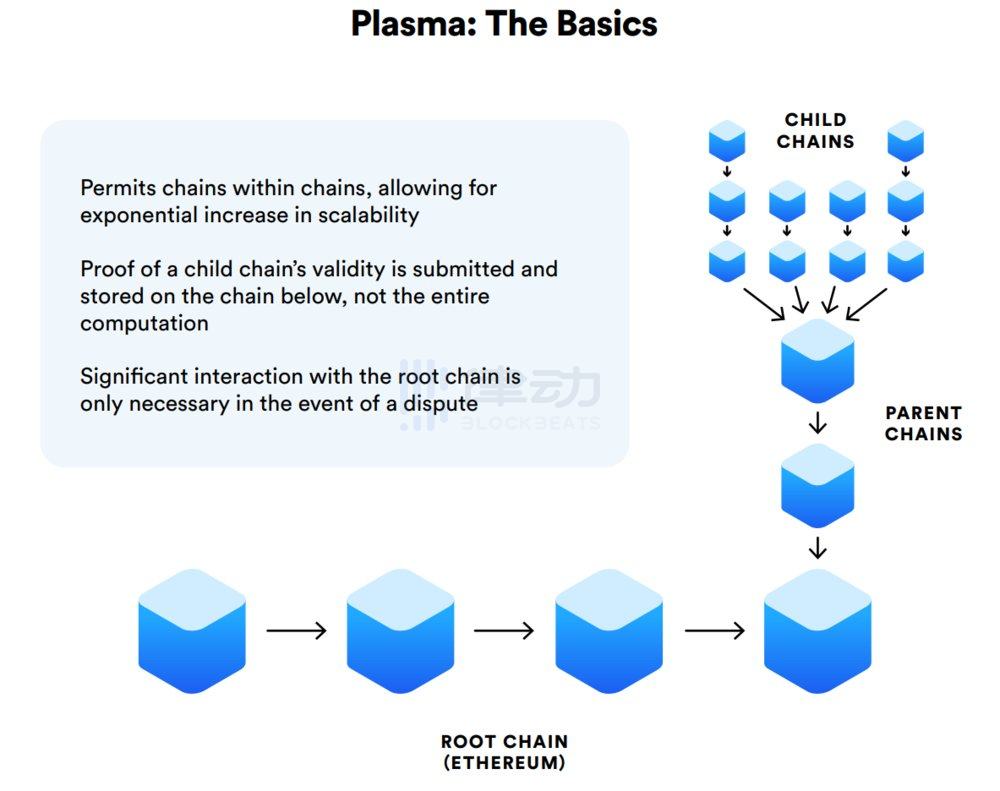
12. Plasma
Plasma is an Ethereum Layer 2 scalability solution that allows the creation of "child" blockchains using the Ethereum mainnet as a trust and arbitration layer.
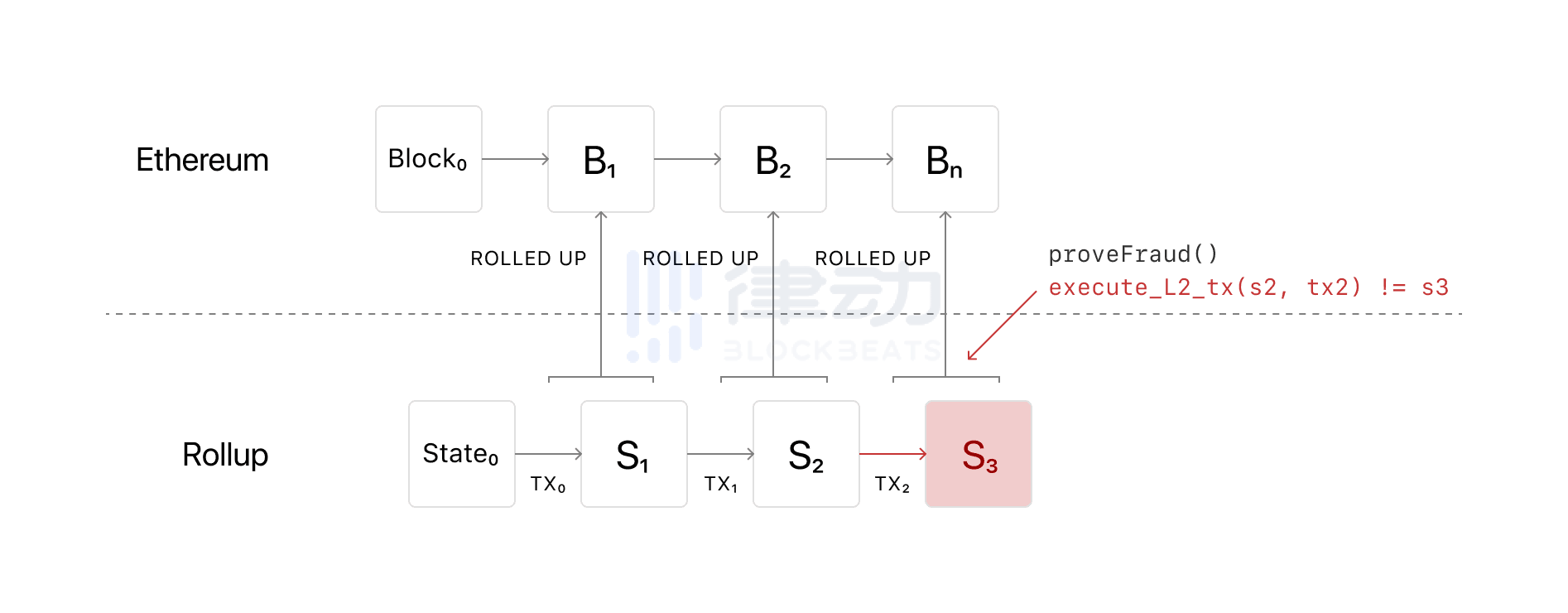
13. Optimistic Rollups
Optimistic Rollups use smart contracts to relay transaction data from the Ethereum mainnet to Layer 2 networks, where sorters can bundle multiple transaction records into a batch and submit that batch back to the mainnet chain through a single transaction.
14. Zero-Knowledge Proof
In cryptography, a Zero-Knowledge Proof allows one party to prove to another that a given statement is true without conveying any additional information beyond the fact that the statement is indeed true.
15. ZK Rollups
Zero-Knowledge Rollups are another Ethereum scaling solution that can extract transaction records from the Ethereum mainnet. ZK Rollups generate cryptographic proofs of transaction validity, with each batch of transaction records containing its own validity proof, submitted to the mainnet.
16. Keepers
Keepers are a class of accounts owned externally by protocols, incentivized to perform specific operations within DeFi protocols. Keepers are rewarded in the form of fixed fees or a fixed percentage of incentives, such as fees for liquidating collateralized debts.
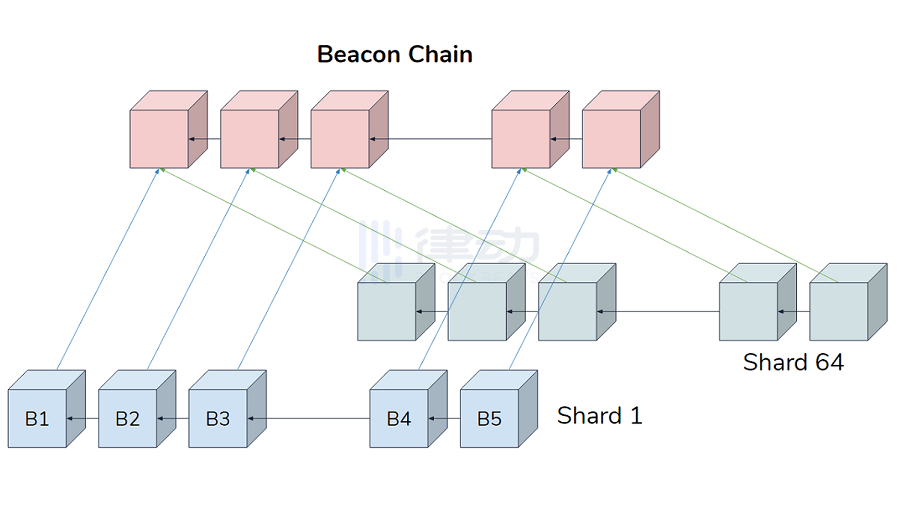
17. Beacon Chain
The Beacon Chain is an upgraded version of Ethereum that will eventually replace the currently used traditional Ethereum blockchain. Its purpose is to introduce a new PoS consensus mechanism and coordinate the expanded shard and staker networks.
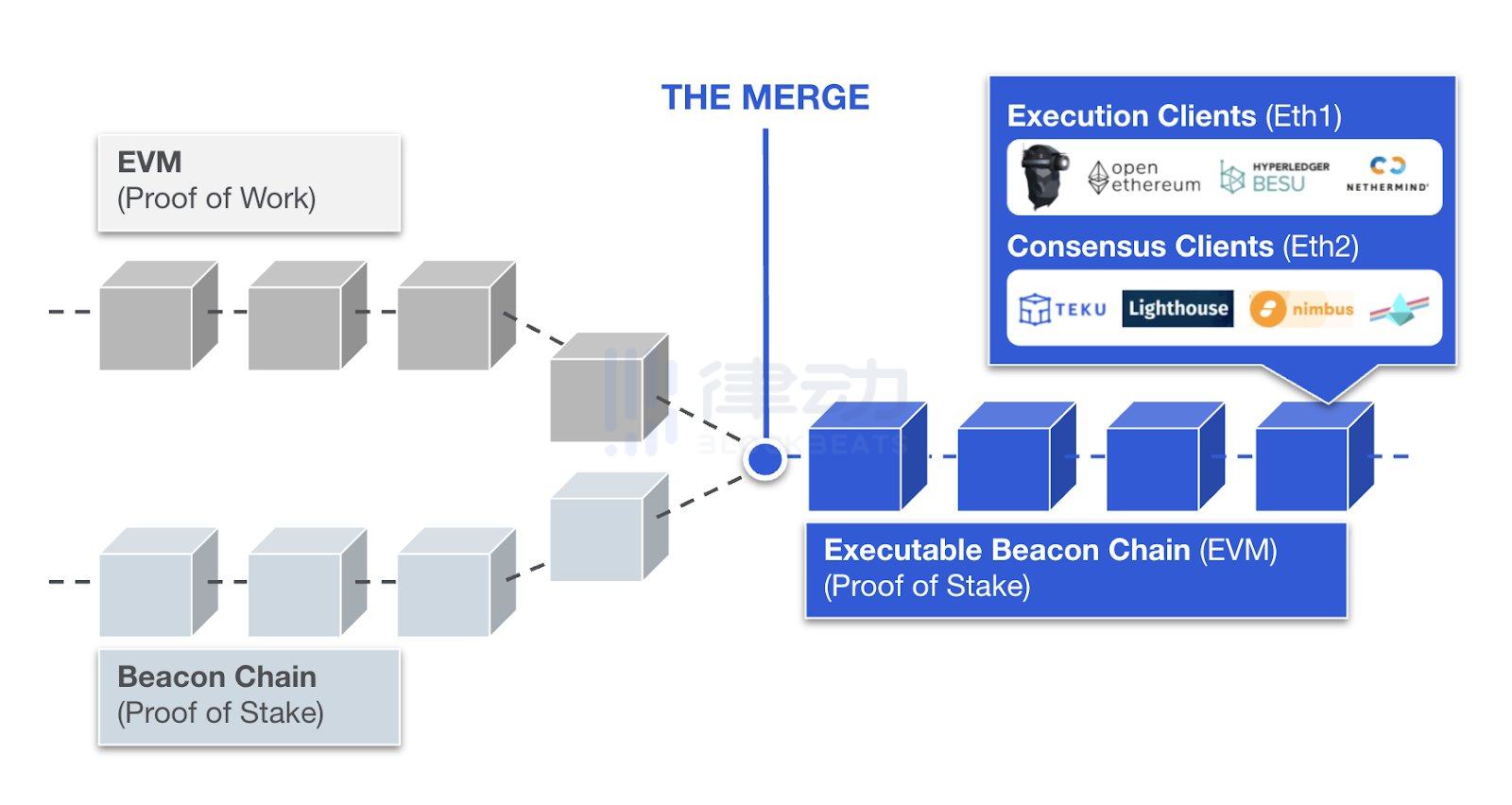
18. Merge
The Merge refers to what will happen when the Ethereum mainnet running on PoW integrates with the Beacon Chain as a PoS chain.
Fifth Level: The Most Esoteric Crypto Knowledge
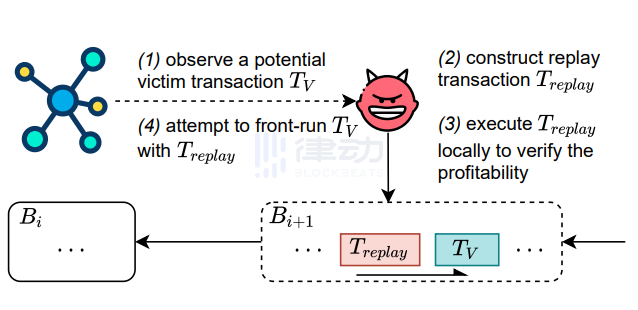
1. MEV
Maximal Extractable Value refers to the ability of miners to earn profits by arbitrarily including, excluding, or reordering transactions in the blocks they produce.
2. Sharding
Sharding refers to dividing the entire Ethereum network into multiple parts, hence called "shards." Each shard will contain its own independent state, significantly reducing network congestion and increasing Ethereum's transaction throughput.
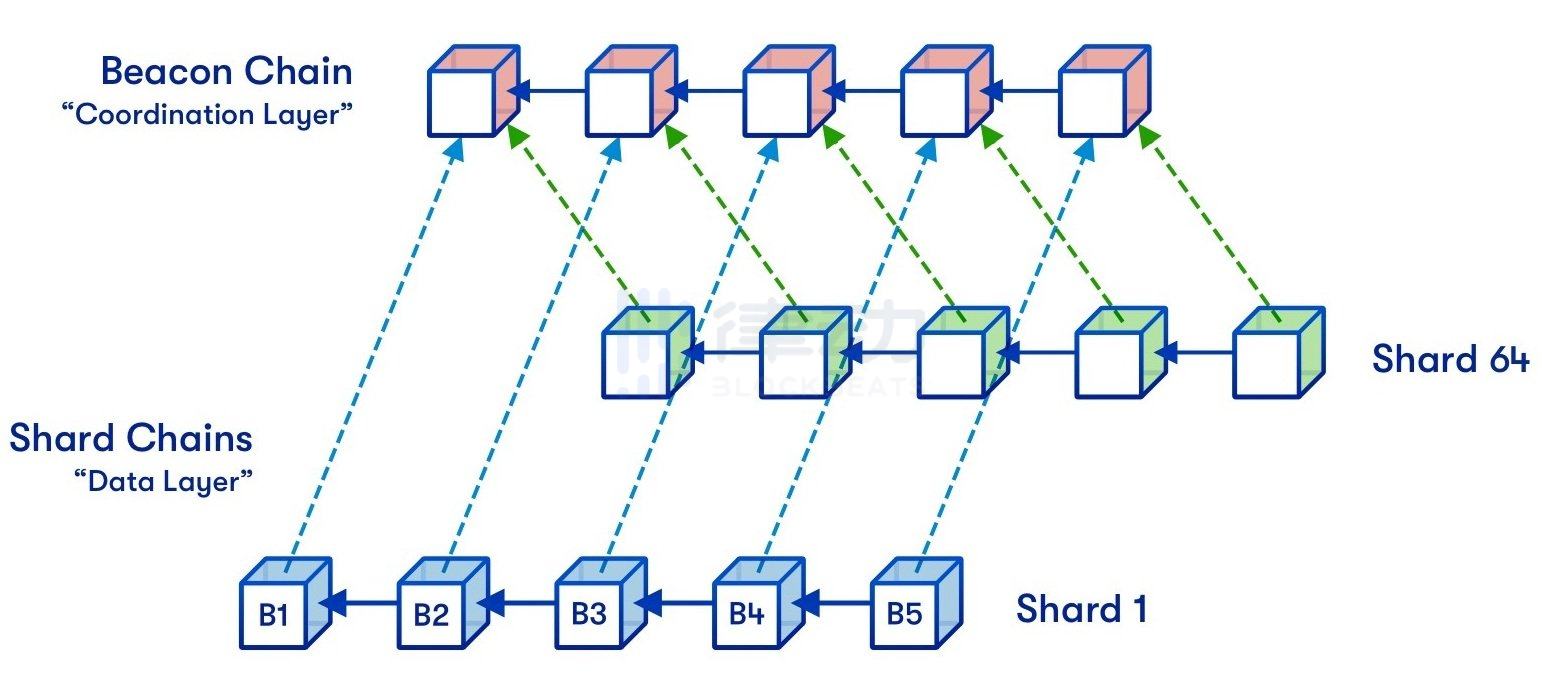
3. Data Availability Proofs
Data Availability Proofs is a new technology that allows users to check whether all data of a block has been published by downloading only a small portion of that block with a very high probability.
4. Merkle Tree
A Merkle Tree is a fundamental component of blockchain technology, a mathematical data structure composed of hash values of different data blocks, serving as a summary of all transactions within a block.









