Reviewing 8 Common Attack Cases of DeFi Economic Models
Author: Jonas, Foresight Ventures
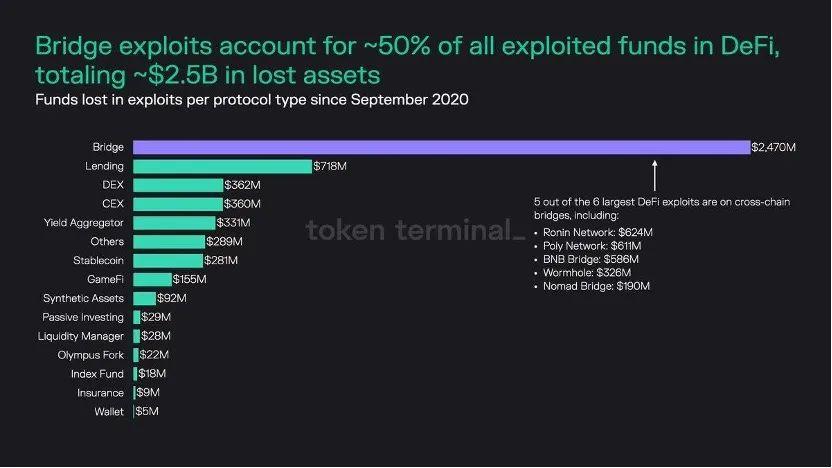
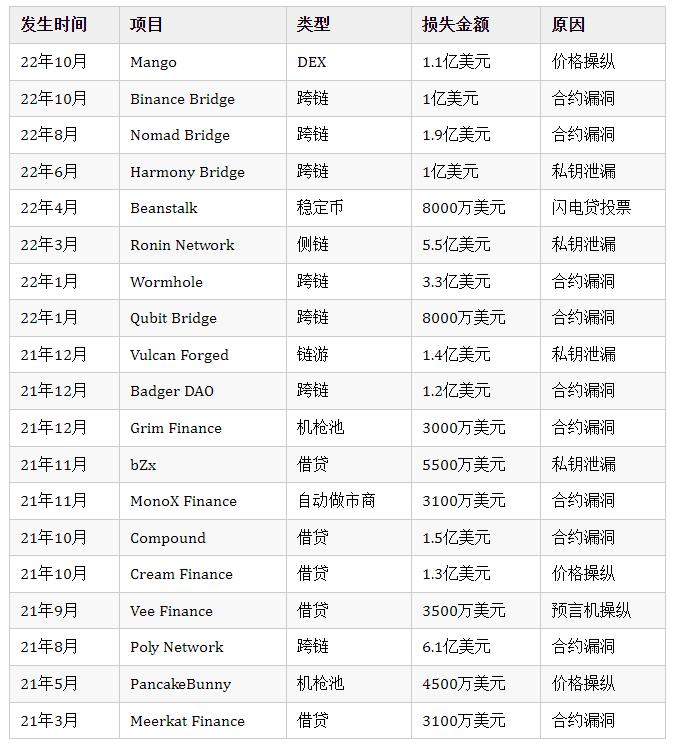
In the dark forest of the crypto industry, DeFi has become a cash cow for hackers, with total losses exceeding $3 billion so far this year. First, DeFi platforms hold a large amount of funds, making the rewards for successful attacks very high. Second, most DeFi protocol codes are open source, making them more susceptible to cybersecurity threats. Third, DeFi ecosystems are often interconnected, amplifying the convenience of attacks. According to a report by Token Terminal, about 50% of vulnerabilities in DeFi occur on cross-chain bridges, followed by lending, exchanges, and liquidity pools.
Attacks on the economic models of DeFi are particularly valuable for research, especially regarding how certain mechanisms behave under extreme conditions, which helps us understand token economics. In a sense, if hackers steal assets through phishing, credential stuffing, and other social engineering methods, it can be considered ill-gotten gains. Conversely, profiting through the rules of DeFi can be seen as brazenly making money, with sophisticated methods that are hard to criticize.
Price manipulation through contract monetization
Price manipulation is one of the earliest and most common vulnerabilities in DeFi. With the rise of on-chain derivatives, the risk-reward ratio for attacks has become very high.
Case 1: MANGO
In October 2022, the decentralized contract platform Mango on the Solana chain was attacked.
Key factor for success: No position limits on altcoin contracts
Attack process:
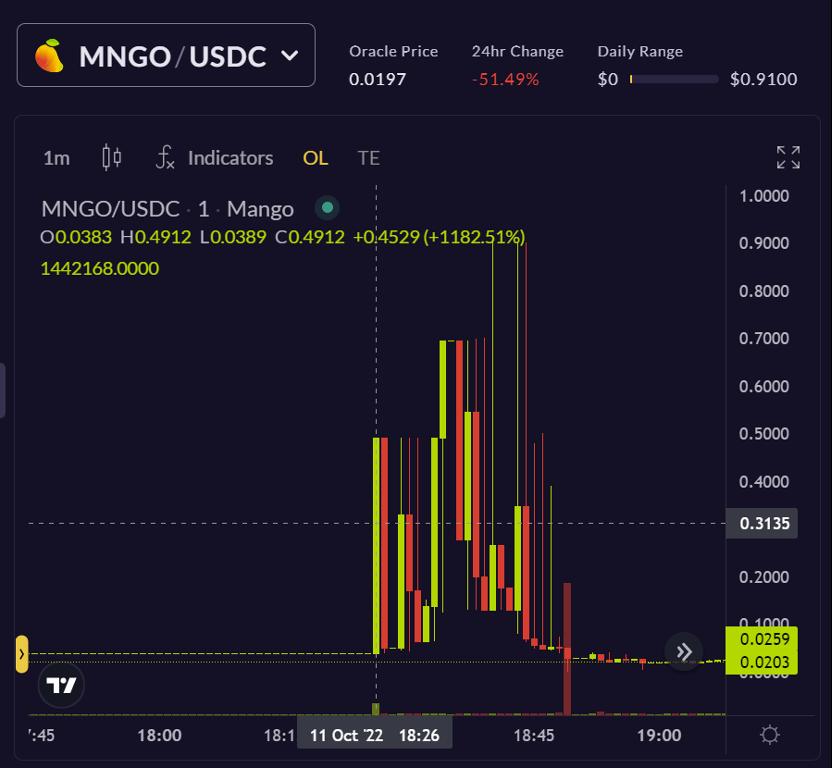
a) Position building: The attacker first transferred $5 million each to addresses A and B on the Mango trading platform. The hacker then shorted the MANGO token using the contract on address A while going long on MANGO on address B. The reason for opening both long and short positions is that, although the Mango platform has no position limits on altcoin contracts, the depth is poor, making it difficult to open such high positions without having a counterparty.
b) Price manipulation: The attacker used more funds to buy MANGO tokens, raising its price from $0.02 to $0.91 within 10 minutes. Since MANGO is a low liquidity token, this allowed the attacker to quickly manipulate the price.
c) Monetization: At this point, the attacker’s long position yielded $420 million, and they borrowed $110 million from the Mango platform using their account's net assets, as the lack of liquidity ultimately limited the borrowing.
Case 2: GMX
In September 2022, the decentralized contract platform GMX on the Arbitrum chain was attacked.
Key factor for success: 0 slippage mechanism, low attack cost
Attack process:
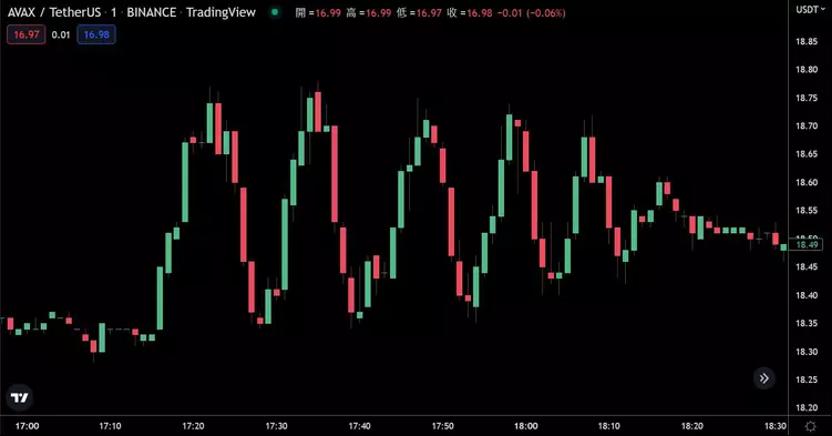
a) Position building: The attacker repeatedly opened large long and short positions on the AVAX token on GMX.
b) Price manipulation: Since GMX has 0 slippage, the price fed by the oracle is approximately equal to the execution price. However, large positions on GMX affect the AVAX/USD price on other exchanges, and only then does the oracle react and feed the price back to GMX. 0 slippage means the attacker has unlimited liquidity at any moment. For example, if they go long $1 billion of AVAX on GMX, such a large amount would normally raise the actual trading price, but due to GMX's 0 slippage mechanism, the position is still opened at the oracle's fed price. However, this volume of trading would raise the price of AVAX on other exchanges, and assuming it rises by 20%, the oracle would then feedback the latest price to GMX, allowing the attacker to close their position at the 20% higher price and withdraw the earned AVAX to sell on other exchanges.
c) Monetization: At this point, the attacker closed their position profitably, and the AVAX earned by the attacker is the AVAX lost by GLP holders.
Exploiting oracle errors to monetize through collateralized lending
These types of attacks are very complex to execute, but the pattern is similar, relying on price-feeding systems that temporarily manipulate prices to distort the internal accounting of the protocol. Then, funds are deposited at favorable rates, and immediately withdrawn in another currency or the same currency after resetting the oracle to normal values.
Case 3: ANKR
In December 2022, the lending protocol Helio on the BSC chain was attacked.
Key factor for success: Delayed oracle price feeds
Attack process:
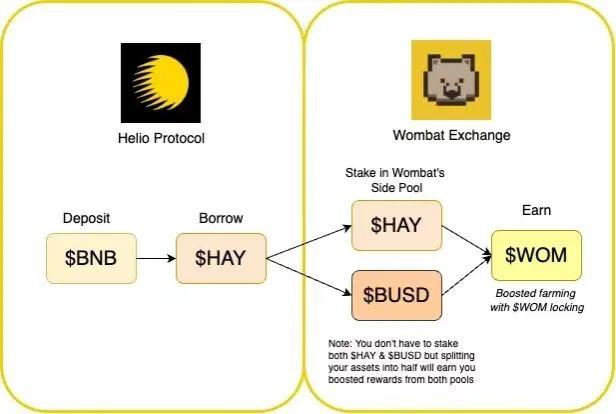
a) Oracle error: The staking project Ankr on the BSC chain was directly exploited by hackers through a contract vulnerability, minting 100 trillion aBNBc out of thin air, causing the price of aBNBc to nearly drop to zero. The lending protocol Helio's oracle price feed uses a 6-hour average weighted setting.
b) Position building: The attacker used 10 BNB to buy 180,000 aBNBc that were over-issued by Ankr, and then exchanged aBNBc for hBNB on Helio.
c) Collateralized lending: The attacker used hBNB as collateral to borrow 16.44 million stablecoins HAY from Helio.
d) Monetization: The attacker exchanged the stablecoin HAY for approximately $15 million worth of assets in BNB and USDC, and withdrew them.
Case 4: XVS
In May 2022, the lending protocol Venus on the BSC chain was attacked.
Key factor for success: Delayed oracle price feeds
Attack process:
a) Oracle error: When LUNA's inflation collapsed, Chainlink's price feedback for LUNA reached the price floor and was paused at $0.107. However, the LUNA market on the lending protocol Venus on the BSC chain continued to operate, with prices coming from Chainlink. The protocol was only paused when the price of LUNA was around $0.01.
b) Position building: Arbitrageurs massively increased the supply of LUNA from the secondary market and brought it to the BSC chain.
c) Collateralized lending monetization: Arbitrageurs used LUNA as collateral on Venus to borrow approximately $14 million worth of assets and withdrew them.
Case 5: BZRX
In May 2020, the lending protocol bZx on the BSC chain was attacked.
Key factor for success: Single source of oracle price
Attack process:
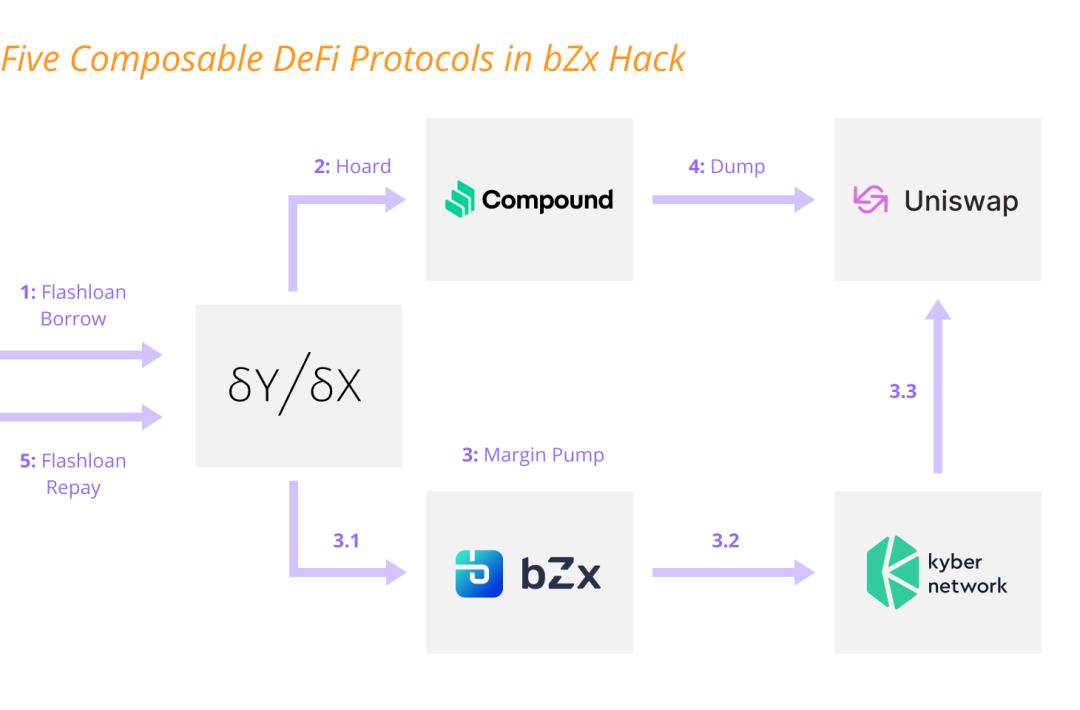
a) Position building: The attacker first borrowed 10,000 ETH through a flash loan from the decentralized contract platform DYDX, using 5,500 ETH to borrow 112 WBTC on the lending platform Compound.
b) Oracle error: bZx is a margin trading protocol where users can pledge one coin as collateral to borrow another coin, relying solely on the price from Uniswap for oracle feeds. The attacker used 1,300 ETH to open a 5x short position on ETH on bZx (i.e., using 5,637 ETH to exchange for WBTC), and due to the limited WBTC available for exchange in the Uniswap pool, the price of WBTC was driven up to three times its normal value.
c) Monetization: The attacker then sold the 112 WBTC borrowed from Compound, making a profit of $360,000.
Oracle manipulation remains a major disaster area for DeFi attacks, with similar cases including Vee Finance, Harvest Finance, Value DeFi, Warp Finance, etc., which will not be listed here one by one.
Shorting DeFi leverage leads to a death spiral
In a bear market, liquidity gradually diminishes, and the price depth of non-mainstream assets becomes insufficient, leading to increased volatility. Large-scale shorting may be driven by DeFi leverage liquidations and capital shorting.
Case 6: LUNA
In May 2022, the stablecoin UST on the Terra chain was attacked.
Key factor for success: Funding schemes facing liquidity runs in a bear market
Attack process:
a) Position building: The attacker believed that the LUNA-UST mechanism could not be maintained long-term. The high yield offered by Terra through Anchor was a strategy to attract users to use UST more. However, a 20% yield is unsustainable. When the interest rate level dropped from 20% to between 7-12%, approximately $9 billion worth of LUNA would leave, but due to insufficient liquidity for LUNA/UST, it was estimated that about $5 billion worth of UST would face exit difficulties. To safely exchange $5 billion of UST for LUNA and leave the market, it would require a market cap of $40 billion for LUNA, while at that time, LUNA's maximum market cap was only $40 billion. It seemed that Terra had exhausted its reserves, lacking funds to maintain the stability of UST, or had given up on maintaining UST's stability. Therefore, the window to observe sustainability was whether the UST Pool on Curve showed signs of imbalance. When Terra removed $150 million in liquidity from Curve to prepare for the 4pool, the smaller liquidity pool size meant that selling UST would have a greater impact on the price than usual. The attacker began to sell $285 million worth of UST, causing the stablecoin to start to de-peg.
Rumors circulated that the attacker Alameda borrowed nine figures of BTC from Voyager before the UST collapse to short BTC and counteract Terra's reserves. At the same time, Genesis Trading provided Alameda with $1 billion in UST, supplying ammunition for the attack against the UST de-pegging.
b) Leverage cycle liquidation:
UST is an algorithmic stablecoin that uses a simple mint-and-burn mechanism to maintain stability. To mint UST, an equivalent value of LUNA must be burned; similarly, users can redeem equivalent LUNA by burning UST. As UST's price fell, the hypothetical death spiral became a reality, with investors destroying UST for LUNA at increasingly lower prices, causing the outstanding supply of LUNA to balloon. In fact, the supply of LUNA increased from less than 350 million to over 6.5 trillion in just a few days.
At the same time, UST faced massive liquidations on Abracadabra. In November of last year, Abracadabra launched the Degenbox strategy for UST, allowing users to collateralize UST to borrow MIM, significantly increasing yields through cyclical collateralization. As long as UST remained at $1, this strategy was essentially risk-free; however, once UST de-pegged, users faced the risk of liquidation as the value of their collateral decreased. When the price of UST dropped to 0.97, a batch would explode, and below 0.9, over 50% of those using this strategy would be liquidated. The cycle continued, with the lower the price of UST, the more liquidations occurred.
Case 7: CRV
In November 2022, the decentralized stablecoin trading platform Curve on the Ethereum chain was attacked.
Key factor for success: Lending protocols can collateralize long-tail assets
Attack process:
a) Position building: The token lock-up mechanism of Curve combined with bribery mechanisms led to severe liquidity shortages. The attacker first opened high-leverage short positions on CRV on exchanges.
b) Borrowing to short: The attacker collateralized a total of 63.6 million USDC on AAVE, borrowing 92 million CRV to short. As the price of CRV plummeted, the collateral of USDC on the lending protocol AAVE could continue to borrow more CRV to short.
c) Leverage cycle liquidation: Since CRV itself is collateral for the lending protocol, the rapid price decline also triggered a large amount of CRV liquidation, potentially causing a chain reaction of death spirals. The attacker aimed to breach the liquidation line of the founder's collateral position, intending to liquidate them. Although the shorting attempt ultimately failed and resulted in liquidation with the joint efforts of the founder and the community, the operational thinking is still worth learning from.
Flash loan governance attacks
DeFi attacks are no longer limited to price manipulation; if the protocol's defenses are insufficient, governance mechanism vulnerabilities may also be exploited by attackers.
Case 8: BEAN
In April 2022, the decentralized stablecoin Beanstalk on the Ethereum chain was attacked.
Key factor for success: No time lock added to voteable funds
Attack process:
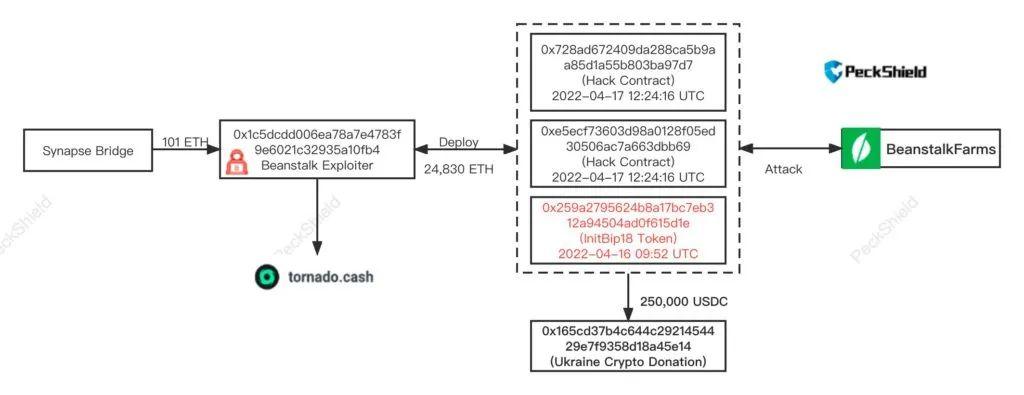
a) Proposal: The attacker published a malicious proposal the day before the attack, which would extract funds from the Beanstalk contract once passed.
b) Position building: The attacker obtained 350 million DAI, 500 million USDC, 150 million USDT, 32 million BEAN, and 11 million LUSD as capital reserves through a flash loan, accumulating a large amount of governance tokens for the protocol.
c) Voting: The attacker used BEAN3CRV-f and BEANLUSD-f to vote on the proposal, leading to its passage. The attacker obtained 24,830 ETH and 36 million BEAN stablecoins, profiting approximately $80 million.
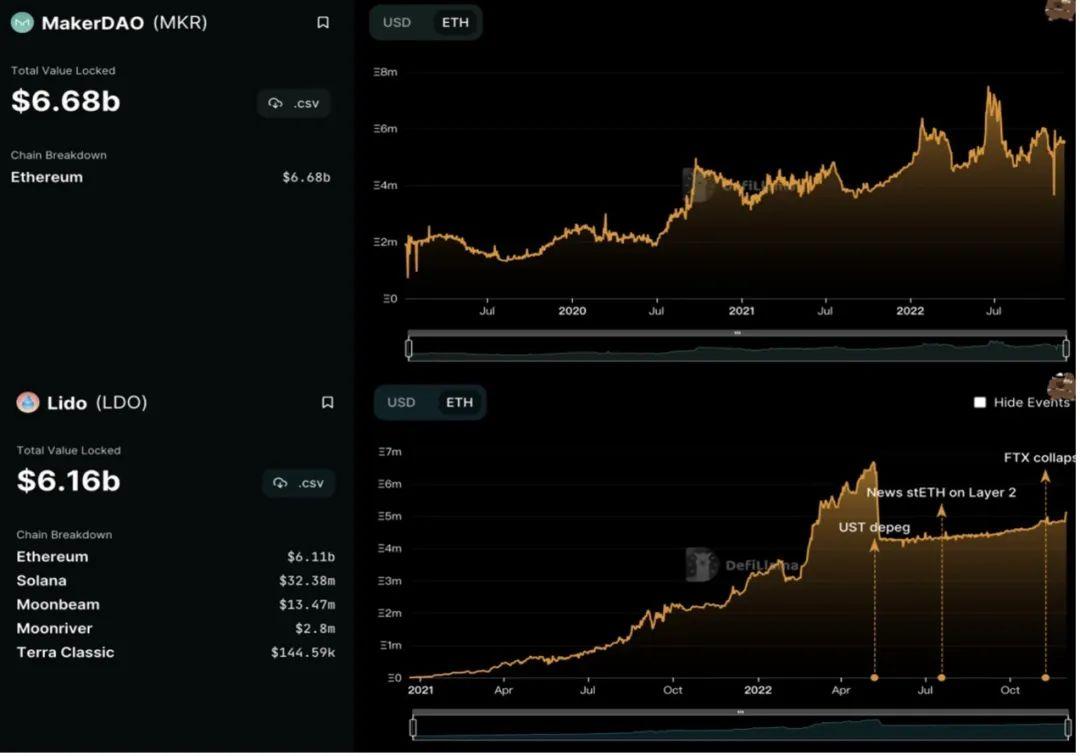
Although it is a bear market, the DeFi market still maintains a certain level of vitality. From the perspective of locked assets, if the crypto market is measured in native assets like ETH rather than USD, the TVL of leading projects like Maker DAO and Lido in 2022 would still show positive growth. Even when calculated in USD, the DeFi market still maintains a TVL of over $40 billion, which is much better than a year ago, indicating that the DeFi market has become an indispensable part of the crypto market.
This bull market marks the starting point of DeFi's prosperity. As the industry rises to become a focal point of attention, attackers have correspondingly shifted their focus to this area. From the attacks mentioned above, it is clear that there is no single method for attacking DeFi protocols; rather, there are common attack vectors that have led some young DeFi projects to become victims. So far, the losses caused by these increasingly frequent attacks have not been catastrophic. However, as the ecosystem continues to develop and the total locked amount increases, the funds involved will become larger, and attacks will become more profitable, leading to more complex DeFi attacks in the future. Practice makes perfect.










