LD Capital: An Overview of All-Star ZK Projects
Author: LD Capital
Privacy has always been regarded as one of the most valuable features in the cryptocurrency community, as most crypto asset holders do not wish for their assets and transaction records to be fully public. Among the various cryptographic technologies that provide privacy, Zero-Knowledge Proof (ZKP) technology is one of the most important. This article does not delve into specialized cryptographic knowledge but aims to provide a theoretical expression of Zero-Knowledge Proofs, helping readers roughly reconstruct the overall picture of ZKP systems and their current development status.
1. Development of Zero-Knowledge Proof Technology
1.1 Concept of Zero-Knowledge Proof
Zero-Knowledge Proof (ZKP) is an important component of modern cryptography, which refers to the ability of the prover to convince the verifier that a certain statement is true without providing any useful information to the verifier. Zero-Knowledge Proofs essentially involve a protocol between two or more parties, where a series of steps are taken to accomplish a task. The prover demonstrates to the verifier that they know or possess a certain message, but the proof process does not leak any information about the message being proven to the verifier. In simple terms: it proves what the prover wants to prove while revealing "zero" information to the verifier.
Zero-Knowledge Proofs themselves involve relatively complex cryptographic algorithms, but to provide a theoretical understanding, we can use an example of a "Finding the Panda" scenario:
A group of people is trying to find a panda in this picture. Person A spots the panda first but cannot immediately point it out, as that would ruin the game for others.

Is there a way for Person A to prove they know where the panda is without revealing the answer to anyone else?
So, Person A takes a large white sheet of paper and randomly covers the picture with it. Then, Person A cuts a small hole in the white paper, allowing only the panda to show through.

In this way, the panda's location, as the key information, is protected, but Person A can still prove they found the panda without letting anyone else know where it is. This is Zero-Knowledge Proof.
The verification method of Zero-Knowledge Proof emphasizes completeness and soundness. The completeness principle states that the prover can convince the verifier to accept a correct statement; the soundness principle states that the prover cannot convince the verifier to accept an incorrect statement. However, in reality, soundness is still probabilistic, meaning the likelihood of the prover cheating is extremely low.
The credibility of Zero-Knowledge Proofs depends on two factors: the difficulty of the proof and the degree of interaction. The difficulty of the proof directly increases the mathematical complexity; the degree of interaction refers to the need for the verifier to continuously question the prover, and as the number of interactions increases, it becomes more difficult for the prover to deceive the verifier, as the probability of providing a correct proof without knowing the correct information statistically decreases.
1.2 Evolution of Zero-Knowledge Proof Theory
The concept of Zero-Knowledge Proof was initially proposed by S. Goldwasser, S. Micali, and C. Rackoff in 1985, introducing "interaction" and "randomness" in their paper, constructing the early [Interactive Proof Systems]. Interactive proofs require the verifier to continuously ask a series of questions about the "knowledge" possessed by the prover. The prover answers a series of questions to convince the verifier that they indeed know this "knowledge." The more questions generated, the more interactions occur, but this method does not ensure that both the prover and verifier are honest; they could collude in advance, allowing the prover to pass verification without knowing the answer.
In the following decades, many legendary cryptographers made significant contributions to the development of Zero-Knowledge Proof systems. For example, M. Blum, P. Feldman, and S. Micali pointed out that "interaction" and "hidden randomness" are not necessary, subsequently proposing the [Non-Interactive Zero-Knowledge Proof Systems] based on the Common Reference String (CRS) model. Non-interactive proofs mean that the prover does not need to interact with the verifier; a set of public parameters must be set up in advance, and transactions are constructed and verified based on the public parameters of Zero-Knowledge Proof. This means the prover can independently generate proofs, avoiding the possibility of collusion between the prover and verifier.
In 2010, Jens Groth proposed a controversial Knowledge of Exponent Assumption, which hid some secret random values in the CRS, reducing the proof length to a constant level. This process can be understood as creating a secret that only the system "knows," while anyone who knows how to generate the public parameters can forge proofs; this process is known as [Trusted Setup Initialization]. Although this scheme significantly reduced the proof length, it also introduced some security risks, as anyone who knows how to generate the public parameters can forge proofs. However, this scheme established one of the most important branches of Zero-Knowledge Proof technology for the next decade.
As the theory of Zero-Knowledge Proofs continued to develop, cryptographers began to delve into engineering aspects. In 2013, Rosario Gennaro, Craig Gentry, and others made further optimized improvements based on Jens Groth's 2010 work, greatly shortening proof times and reducing proof lengths to even smaller constant levels. Subsequently, Parno and others implemented a verifiable computation protocol called Pinocchio and continued to optimize and improve it.
In 2014, the encrypted privacy currency ZeroCash was born, with Eli Ben-Sasson, Alessandro Chiesa, and others slightly improving the Pinocchio protocol, marking the first successful implementation of Zero-Knowledge Proof technology in the blockchain field. ZeroCash is the predecessor of Zcash, and the Zcash team also made significant contributions to the engineering of Zero-Knowledge Proofs.
1.3 Current Development Status of Zero-Knowledge Proofs
The combination of Zero-Knowledge Proof technology and Zcash highlights its potential in the blockchain field and represents an important practice of moving Zero-Knowledge Proof technology from theory to application.
Currently, there are several main Zero-Knowledge Proof schemes, each representing different practical implementations of Zero-Knowledge Proofs, which yield different effects mainly reflected in security, proof size, computational speed, and verification speed.
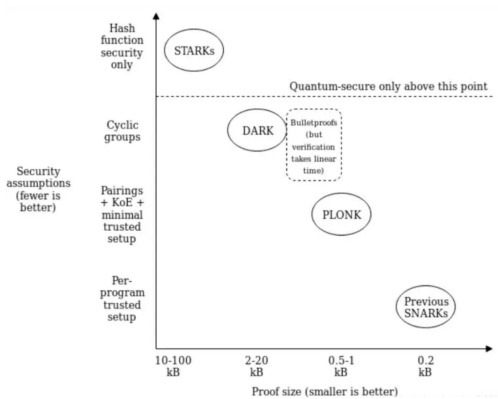
The horizontal axis represents the size of the proof, while the vertical axis represents the security assumptions. Among them, the highest security is the STARK algorithm, which does not rely on mathematical problem assumptions and is quantum-resistant; the smallest proof size is the Groth16 algorithm in the SNARK scheme; PLONK is also a type of SNARK, with moderate security and proof size. Currently, the most widely used are the zk-STARK and zk-SNARK categories.
1.3.1 zk-SNARK
SNARK (Succinct Non-Interactive Argument of Knowledge) is an abbreviation for succinct non-interactive knowledge proofs. This scheme is characterized by its succinctness, meaning the verification process does not involve large data transfers and the verification algorithm is simple, which implies that verification time does not exponentially increase with computational throughput. Secondly, non-interactive knowledge proofs consist of a single piece of information from the prover to the verifier, making the entire verification process more efficient. Groth16 is currently the fastest verification speed and smallest data size zk-SNARK, with Zcash being its first widespread implementation. Groth16 further optimized the Pinocchio protocol, compressing the proof size by nearly half while slightly strengthening security assumptions.
However, one controversial aspect of the Groth16 scheme is [Trusted Setup Initialization], as the random values hidden in the CRS are typically determined by a small group, leading to potential trust issues. Moreover, theoretically, if the prover has sufficient computational power, they can submit false proofs, thereby affecting the overall security of the system. This is also why quantum computers are considered a threat to this algorithm. Therefore, Trusted Setup Initialization is the most critical issue that other Zero-Knowledge Proof technologies are striving to overcome. The PLONK algorithm also makes improvements regarding trusted setups, and we will discuss the differences between these two algorithms in detail later.
To address this issue, Stanford cryptographer Benedikt Bünz and others proposed Bulletproof technology, which, compared to earlier zk-SNARKs, does not require a trusted setup, but both computation and verification times are longer than STARKs, while the proof size is much smaller than STARKs. This scheme was quickly adopted by the Monero project.
1.3.2 zk-STARK
STARK (Scalable Transparent Argument of Knowledge) is a scalable transparent argument of knowledge created as an alternative to SNARK. Unlike the "S" in SNARK, which stands for Succinct, the "S" in STARK stands for Scalable, primarily reflected in the fact that the time complexity of generating proofs (Proof) in STARK is approximately equal to the computational complexity, while the time complexity of verifying proofs (Verify Proof) is much smaller than the computational complexity. In other words, as STARK's scalability increases, the proof complexity does not correspondingly increase.
More importantly, STARK does not require a trusted setup, as it relies on a more streamlined symmetric encryption method through hash function collisions. This is also the transparent aspect of STARK.
The third improvement of STARK compared to SNARK is quantum resistance, meaning it cannot be broken by quantum computing. Of course, these improvements come with sacrifices. Compared to SNARK, STARK is more complex, with proof sizes increasing from 288 bytes to several hundred KB, and the Ethereum verification fees consumed are also higher.
1.3.3 Zero-Knowledge Proof Schemes with Trusted Setup
Although Zero-Knowledge Proof systems based on trusted setups require the generation of public parameters, they have been proven to have advantages in computational costs and proof sizes, making them the preferred tool for many privacy-focused blockchain applications. The security of trusted setup Zero-Knowledge Proof systems largely depends on the security of the public parameter generation, and generating these parameters in a trusted centralized manner is possible but incompatible with decentralization goals. So far, the preferred technology used in trusted setups is Multi-Party Computation (MPC).
MPC schemes attempt to ensure that no party can generate or obtain knowledge of the underlying mathematical structure of these parameters. This is achieved by requiring the generation process to be shared among as many independent participants as possible, with only a few (or even one) needing to act honestly to ensure the setup's security. Clearly, the more participants involved in MPC, the higher the security of the parameters.
Zk-SNARK is a trusted setup Zero-Knowledge Proof scheme, but different algorithms have evolved within it. Groth16 and PLONK are currently the most widely adopted trusted setup Zero-Knowledge Proof schemes, and the differences between them are:
Groth16 is the fastest verification speed and smallest data size scheme, but due to Groth16's secret computation being associated with specific problems, each time it requires a new round of MPC trusted setup based on different problems. The multi-party computation protocols usually are extremely cumbersome, which significantly affects Groth16's performance.
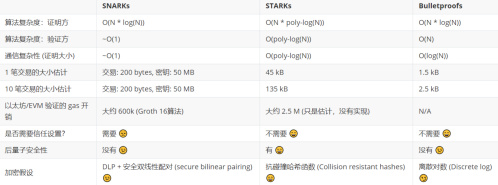
PLONK is an improved version of Sonic, reducing proof time by five times. Sonic is an updatable global CRS scheme. The term "updatable" means that the trusted pre-setup can be updated at any time if there are suspicions that secrets have been leaked. The term "global" means that the computation process is no longer bound to the CRS; an application only needs to complete a trusted pre-setup once to achieve different Zero-Knowledge Proof circuit computations. In other words, the trusted setup only needs to be set once, and apart from updates, there is no need to conduct new MPC for different problems each time. The following diagram compares the performance of Groth16 and PLONK:
The PLONK algorithm was developed collaboratively by researchers from Protocol Labs and two researchers from the Ethereum privacy transaction protocol Aztec Protocol. PLONK was proposed later than Groth16, with some differences in proof size and verification speed, but its characteristic of updatable trusted setups allows the PLONK algorithm to occupy a place in the field of Zero-Knowledge Proofs.
2. Applications of Zero-Knowledge Proof Technology
Two important characteristics of Zero-Knowledge Proof technology are the main factors for its application in the blockchain field: 1) Zero-Knowledge Proofs can protect data privacy by proving it without leaking data information; 2) Zero-Knowledge Proofs only require generating a small amount of proof data to complete proofs for large volumes of data, which can play a significant role in compressing data and improving performance.
Therefore, the two directions of Zero-Knowledge Proofs are:
2.1 Privacy Protection
Privacy protection has always been an extremely important concept in blockchain, representing the ability to protect transactions and participants in a distributed network. Although blockchain has always advocated anonymity, in most transactions, participants do not need to use their real names, but they can still be identified by repeatedly using public key hashes as transaction identifiers, so these transactions only have pseudonymity and do not achieve true anonymity. By default, every transaction by a user is public, and once a user address is locked, it is possible to view the source of funds, calculate holdings, and even analyze the user's on-chain activities based on that address.
Zero-Knowledge Proof technology can confirm the validity of transactions by submitting proofs that do not disclose any information, achieving complete anonymity of transaction information. During the period emphasizing encrypted privacy issues, many developers have devoted themselves to exploring privacy public chains, and the privacy protection and data compression capabilities of Zero-Knowledge Proofs are significant reasons for their importance in public chain technology. During this period, projects like Zcash and Monero have shone brightly.
Taking Zcash as an example, ZCash initially adopted the Pinocchio protocol and switched to the Groth16 proof system in 2019. ZCash wallet addresses are divided into hidden addresses and transparent addresses. Transactions between transparent addresses are no different from Bitcoin transactions: the sender, receiver, and transaction amount are all publicly visible; transactions between hidden addresses also appear on the public blockchain, but the transaction addresses, amounts, and memo fields are encrypted, and zk-SNARK proves the validity of the transaction under network consensus rules; additionally, transactions can also occur between hidden and transparent addresses. Zcash protects transaction privacy while maintaining friendliness towards auditing and regulation, allowing senders and receivers of hidden address transactions to publicly disclose transaction details to third parties for witness, compliance, or auditing needs.
2.2 Scalability
The "impossible triangle" is a perpetual dilemma faced by Layer 1 blockchains like Ethereum, as different chains constantly seek a balance between decentralization, security, and scalability. Ethereum leans more towards decentralization and security, thus facing limitations in scalability. The high gas fees and long transaction confirmation times on Ethereum significantly affect user experience. Therefore, its core development team and community have been exploring various scalability solutions.
There are two methods to scale a blockchain: 1) scaling the Layer 1 blockchain itself, methods include increasing block size or sharding, which divides the nodes in the blockchain network into several relatively independent shards, with each shard responsible for a smaller processing scale, even storing only part of the network state, allowing multiple shards to process transactions in parallel, theoretically increasing the overall network throughput. However, this approach sacrifices decentralization; 2) transferring transactions on the Layer 1 network to Layer 2, where Layer 2 aggregates transactions and then sends them to the Layer 1 network for settlement. In this way, each batch of transactions pays one gas fee instead of each transaction paying a gas fee. Thus, all transactions share the gas fees, effectively reducing the cost per transaction. In this way, Layer 1 becomes the settlement layer for all executed transactions on Layer 2. Layer 2 scalability solutions can address the scalability issues of Layer 1 without sacrificing decentralization and security.
Of course, Layer 2 scalability solutions have also evolved from state channels to Plasma and then to Rollup. Currently, Rollup is the most mainstream and promising Layer 2 solution. Rollup refers to performing complex computations and state maintenance off-chain first, then saving data related to state changes on-chain through contract calls, using cheaper CALLDATA to package a large number of transactions into one transaction, ultimately improving TPS while ensuring data availability.
The common point of Rollup solutions is to emphasize on-chain data availability, meaning anyone can reconstruct the global state based on the data stored on-chain, thus eliminating security risks brought by data availability issues. Zero-Knowledge Proofs play a role in compressing on-chain computation while ensuring data correctness.
The ZK Rollup solution originated in the second half of 2018, and its key lies in ZK, where each state transition requires providing a Zero-Knowledge Proof, verified by contracts on the main chain, and only upon successful verification can the state be changed. That is, the state transitions of ZK Rollup strictly depend on cryptographic proofs. (Note: For a detailed explanation of the ZK Rollup principle, refer to Li Hua's "Clarifying Layer and Cross-Chain Methods in One Article.")
Of course, there are other Rollup solutions, such as Optimistic Rollup, which emerged in the second half of 2019. Its state transitions do not require strict verification; it optimistically assumes that each transition is correct, and within a certain time limit, a transition can be challenged. If the challenge is successful, it proves that the previous submission had issues, punishing the submitter and rolling back the state. That is, the state transitions of Optimistic Rollup rely on economic incentives and game theory.
The prominent issue with ZK Rollup is its difficulty in achieving programmability, but ZkSync's virtual machine and related designs can enable programmability; the most concerning issue with Optimistic Rollup seems to be the delay caused by the challenge period when funds return from Layer 2, but intermediaries can provide advance payment services, thus allowing Optimistic Rollup solutions to be implemented more quickly.
The performance comparison between the two is shown in the following diagram:
Compared to Optimistic Rollup, the ZK Rollup solution has a very high technical complexity, requiring a lot of computation, and the transaction latency may increase, with higher computational costs; however, the transaction fees are lower, and verification costs are much lower than computation costs, making this simplicity a condition for scalability.
According to the latest data from I2beat.com, the total locked assets in Layer 2 solutions are approximately $6.7 billion, among which the Optimistic Rollup Layer 2 scalability solutions proposed by Arbitrum and Optimism occupy half of the market share. The assets locked in Zero-Knowledge Proof solutions are only about $1.7 billion, due to the higher technical implementation difficulty and the ecosystem applications not yet fully realized.
3. Star Projects of Zero-Knowledge Proof Solutions
Although early Zero-Knowledge Proof projects like Zcash and Monero performed well in privacy protection, they could only serve as a means of value storage and struggled to support other applications. With the efforts of many developers, they are attempting to combine Zero-Knowledge Proofs with smart contracts to explore greater potential. Current applications can be roughly divided into three categories, and this section will introduce some very promising Zero-Knowledge Proof projects, most of which have not yet issued tokens.
3.1 Mina
Mina was established in 2017, formerly known as Coda Protocol. Its development team is O(1) Labs, which currently consists of world-class cryptographers, engineers, PhDs, and entrepreneurs.
Mina focuses on building a lightweight blockchain, maintaining a block size of 22 KB compared to the hundreds of GB of block space in Ethereum and Bitcoin, enabling most people to participate and become nodes. The low barrier to node deployment makes it easier for various users to access and deploy nodes, further decentralizing the network and enhancing security.
The core of Mina's ability to maintain a constant block size lies in the use of recursive Zero-Knowledge Proofs, which compress each block into a single proof using zk-SNARK technology during each block production, and each new SNARK proof includes past SNARK proofs, allowing nodes to only check that proof without needing to verify the entire transaction history.
But this is just the first step; a characteristic of blockchains is that each block must reference the previous block. If only SNARK proofs are generated for each block, the overall capacity will still grow linearly. Therefore, Mina creates SNARKs for SNARKs (i.e., recursion) and continuously iterates and nests these SNARK proofs in a recursive structure, achieving a constant block size of about 22 KB.
Additionally, Mina has built an ecosystem around Zero-Knowledge Proofs that can protect data privacy. Its ecological application Snapps (now renamed zkApps) can implement specific business logic for certain scenarios and can collaborate with other public chains through bridging to enhance interoperability, allowing the entire blockchain ecosystem to benefit mutually. Moreover, with the lightweight node feature, currently, only Mina is developing in this field.
Funding Background:
In March 2022, Mina announced the completion of a $92 million strategic financing led by FTX Venture and Three Arrows Capital, which will be used to accelerate Mina's adoption as a leading Zero-Knowledge Proof platform in Web3 by attracting world-class developers.
Prior to this, Mina had undergone four rounds of financing, raising approximately $48.15 million, with investors including Coinbase Ventures, Polychain Capital, Three Arrows Capital, Paradigm, Multicoin, and other top institutions. Excellent investment institutions often pay more attention to long-term value, and most of these institutions bring their own IP traffic, which is very beneficial for Mina's proactive market expansion in the future.
3.2 ZkSync
zkSync is a project built by the Matter Labs team, which was established in December 2019, primarily targeting Ethereum scalability. zkSync 1.0 is a ZK Rollup (Zero-Knowledge Proof) Layer 2 scalability solution on Ethereum, mainly focusing on payments, and was launched on the Ethereum mainnet in June 2020. The SNARK algorithm initially used by zkSync was Groth 16. Using Groth 16 not only requires a trusted setup once (such as at the genesis of zkSync) but also requires a trusted setup for each new application upgrade on zkSync. This created obstacles for zkSync 1.0 in creating an EVM-compatible environment, so zkSync 1.0 was limited to specific applications, such as payments.
zkSync 2.0, on the other hand, is an EVM-compatible Layer 2 solution built on Ethereum, also known as zkEVM, as it recompiles EVM code and uses Zero-Knowledge Proofs to verify Rollup transactions, allowing developers to build and deploy decentralized applications in a low gas fee, highly scalable Layer 2 environment using Ethereum's native programming language.
In May 2021, zkSync released the Alpha version of zkEVM and expected the mainnet to launch in August 2021, but it was delayed due to technical difficulties. In February 2022, the public testnet of zkSync 2.0 was launched. zkEVM has been released, making it the first EVM-compatible ZK Rollup on the Ethereum testnet.
Funding Background:
In March 2021, Matter Labs completed a $6 million Series A financing led by Union Square Ventures, with other notable investment institutions including Placeholder and Dragonfly. This round of financing is particularly noteworthy for introducing many ecological partners, including some of the most well-known companies and founders in the cryptocurrency field.
In November 2021, Matter Labs completed a $50 million Series B financing led by A16Z, with several centralized exchanges (Blockchain.com, Crypto.com, ByBit, OKEx) among other strategic investors. Shortly after the financing announcement, these exchanges announced partnerships with zkSync to support deposits/withdrawals between exchanges and Layer 2.
3.3 StarkWare
The StarkWare team was established in May 2018, consisting of world-class cryptographers and scientists, with the core member being the former chief scientist of Zcash, who has innovated in the field of Zero-Knowledge Proofs for many years. The zk-STARK technology was proposed by this team in a scholarly paper in 2018. The authors of this paper subsequently founded StarkWare.
Like zkSync, StarkWare is also a player in the Zero-Knowledge Proof scalability solutions, but StarkWare is based on STARK. The issue with STARK is that its technology is not as mature as SNARK, and if it achieves Turing completeness, it becomes challenging to be compatible with EVM. StarkWare created a specific programming language called Cairo to run autonomous programs supported by STARK. The StarkWare team is currently collaborating with the Nethermind team to create a code translator called Warp, which seamlessly converts Solidity smart contracts into Cairo to ensure compatibility with EVM.
StarkWare launched StarEx, allowing the creation of application-specific ZK Rollups supported by Cairo and STARK. dydx, Immutable, and Deversifi are three major applications supported by StarkEx. So far, StarkEx has processed over 5 million transactions through these applications, worth over $250 billion.
On November 29, 2021, they released the Alpha version of StarkNet's mainnet. StarkNet is a ZK Rollup Layer 2 application network that plans to develop its own ecosystem.
Funding Background:
StarkWare has completed four rounds of financing, raising over $160 million, with many top institutions such as Paradigm, Polychain, Sequoia Capital, and IOSG participating, and angel investors including Ethereum founder Vitalik Buterin (V God), who is highly favored in the crypto community.
3.4 Aztec
The Aztec team was established in 2018, with many members being PhDs from world-class universities, including former researchers from Zcash, possessing strong technical backgrounds. Their self-developed PLONK algorithm has been adopted by several projects in the industry.
Aztec also addresses Ethereum's scalability issues through ZK Rollup technology. From the project's inception to the launch of Aztec 2.0, the team has been conducting in-depth research on the PLONK algorithm, during which they released Zero-Knowledge Proof algorithms like PLONKUP, and V God has praised the team's research capabilities.
The Aztec network primarily serves two purposes: first, to ensure user privacy during interactions, and second, to allow users to establish fully private applications through Aztec's programmable privacy contracts.
After the launch of Aztec 2.0, they introduced the zk.money private transfer application, where sending and receiving tokens is anonymous. Transactions are encrypted through recursive Zero-Knowledge Proofs, and no transaction data is publicly released to protect user privacy; however, it currently only allows users to perform deposit transfers. Aztec Connect, as the first privacy cross-chain bridge, is also currently in the testing phase.
The development of the Aztec project can be roughly divided into three stages: the first stage is Aztec 1.0, a privacy transaction tool on Ethereum; the second stage is Aztec 2.0, which becomes Ethereum's privacy Layer 2 through zk-Rollup, bringing scalable privacy to Ethereum; based on current disclosures, the future third stage will be Aztec 3.0, which will implement privacy smart contracts on Ethereum Layer 2 through the Noir privacy programming language. However, most zk-Rollup Layer 2 projects face the issue of EVM compatibility, and the Aztec network is currently still unable to be compatible with EVM, which increases the difficulty and cost for many projects to construct privacy smart contracts. The project team has also disclosed that they are working on improving this issue through technical research.
Funding Background:
In November 2018, Aztec completed a $2.1 million seed round of financing led by ConsenSys Labs. In December 2021, Aztec completed a $17 million Series A financing led by Paradigm, with IOSG and others participating, including angel investor Stani Kulechov, the founder of the leading lending project Aave. This round of financing will be used to continue developing the ZK system and further improve Aztec Connect, which, according to its explanation, can save up to 100 times the gas fees during privacy transactions.
3.5 Aleo
The Aleo project was officially established in 2019, with team members consisting of world-class cryptographers, engineers, designers, and operators from companies like Google, Amazon, and Facebook, as well as research universities like UC Berkeley, Johns Hopkins University, NYU, and Cornell University.
Aleo shields identities and transactions through its structured zkCloud system, allowing shielded identities to interact directly (e.g., asset transfers) or programmatically (via smart contracts). In a typical public blockchain, program execution occurs on-chain in a global "virtual machine" (VM) run by each network node. Therefore, every node in the network must recompute (and collectively agree on) each step of a given program. This is not only inefficient but also slows down processes and increases costs for end users. zkCloud overcomes these limitations by separating application runtime from the state maintained by the blockchain (on-chain + off-chain), combined with recursive Zero-Knowledge Proofs, enabling Aleo to achieve complete programmability and privacy, as well as higher transaction throughput.
To enhance the developer experience, Aleo has built a programming language called Leo that is more friendly for developing Zero-Knowledge Proof applications. Leo is a statically typed programming language inspired by Rust, designed specifically for writing private applications. In addition to being developer-friendly, they have also launched developer incentive programs and testnet incentives to support the early development of the Aleo ecosystem.
Funding Background:
In April 2021, Aleo completed a $28 million Series A financing, led by a16z, with participation from Placeholder, Galaxy Digital, Variant Capital, and Coinbase Ventures.
In February 2022, Aleo announced the completion of a $200 million Series B financing, the largest single financing amount in the Zero-Knowledge Proof track to date, led by Kora Management LP and SoftBank Vision Fund 2, with participation from Tiger Global and Sea Capital.
Conclusion
Zero-Knowledge Proof technology has indeed occupied a very important position in the blockchain field, but it has not yet fully matured. Various schemes still have shortcomings in quantum resistance, performance optimization, and compatibility with EVM. However, current Zero-Knowledge Proof schemes are in a period of rapid development, and projects like zkSync and Starknet bring more possibilities for blockchain development.
References
1. "Development Report on Zero-Knowledge Proof Technology," Torus Research Institute, Anbi Laboratory
2. "What is Zero-Knowledge Proof? | ZK Popular Science Series (1)," ZK Enthusiasts
3. "[Public Due Diligence] In-Depth Report: Mina," First Class Cargo
4. "The Development of Layer 2 and the Rise of zk-Rollup | ZK Popular Science Series (2)," ZK Enthusiasts
5. "Clarifying Layer and Cross-Chain Methods in One Article," Li Hua
6. "[Cryptography Column] Advanced: PLONK VS Groth16 (Part 1)," Fun Chain Technology










